Because sometimes you just want to f-ing ping!
Modern browsers, believing they are being clever, hide the protocol in the URL bar.
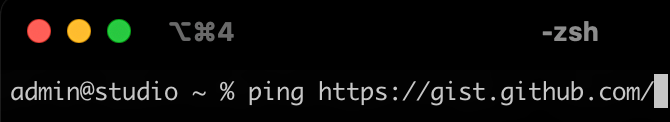
However, even if you only select the hostname, when you paste that URL into your terminal, you will encounter the following: