hi
<script> alert('hi') </script>| https://app.land/applications/219?mapset=1970 |
| root@3935c7d86a07:/# cat policy-2.yml | |
| - !user alice | |
| - !group developers | |
| - !grant | |
| role: !group developers | |
| member: !user alice | |
| - !policy | |
| id: conjur/authn-k8s/minikube/default | |
| owner: !group /k8s_admin | |
| body: | |
| - !webservice | |
| annotations: | |
| kubernetes/namespace: default | |
| - !host client |
| - !policy | |
| id: myapp | |
| body: | |
| - &variables | |
| - !variable | |
| id: database/username | |
| annotations: | |
| description: Application database username | |
| - !variable | |
| id: database/password |
Create distinct roles with specific permissions to call untrusted web services.
Client services authenticate as one of these roles when calling an untrusted web service.
When using an externalized (Nginx) forwarder and gatekeeper, a webservice client can send a Conjur access token for its own identity. The client doesn't have to worry about the gatekeeper misusing the access token,
| # Defines a Bastion server layer. | |
| # | |
| # Usage: | |
| # conjur policy load --as-group ops bastion-policy.rb | |
| policy "bastion" do | |
| # Members of this group will be able to adminsiter the bastion. | |
| admins = group "admins" | |
| # Members of this group will be able to login to the bastion | |
| # with a regular, non-privileged account. | |
| users = group "users" |
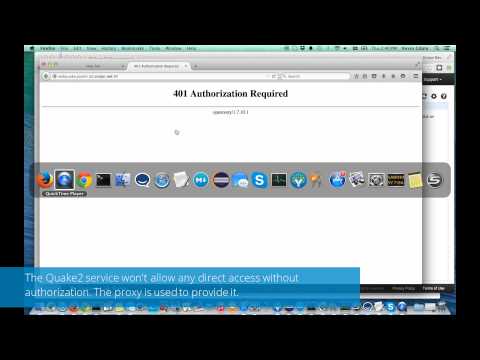
Have you checked out how we secured a Node.js port of Quake2 using Nginx and Conjur and you want to give it a try yourself?
Here's how to do it.
First, install the Conjur CLI. You'll need this to login to Conjur.
Here's a blog post about how we secured a Node.js port of Quake2 using Nginx and Conjur:
http://blog.conjur.net/how-securing-webquake-is-like-securing-an-enterprise-application
There's a link to a 6-minute video walkthrough at the end which is easy to miss so I am including it here:
Hope you find this interesting!
| # Simple script which creates two groups, blue and green. Each | |
| # group contains a couple of users. The groups have different permissions | |
| # on 'webservice' resources. In an SDF gatekeeper scenario, the 'blue' | |
| # team will be able to 'read' service a, and the 'green' team will be | |
| # able to 'read' service b. Neither team can perform any action besides 'read'. | |
| # The owner of the 'webservice' resources (which is the user that runs this script) | |
| # has all permissions on all records, via Conjur ownership. | |
| # Create the blue team | |
| blue = group "blue" do |