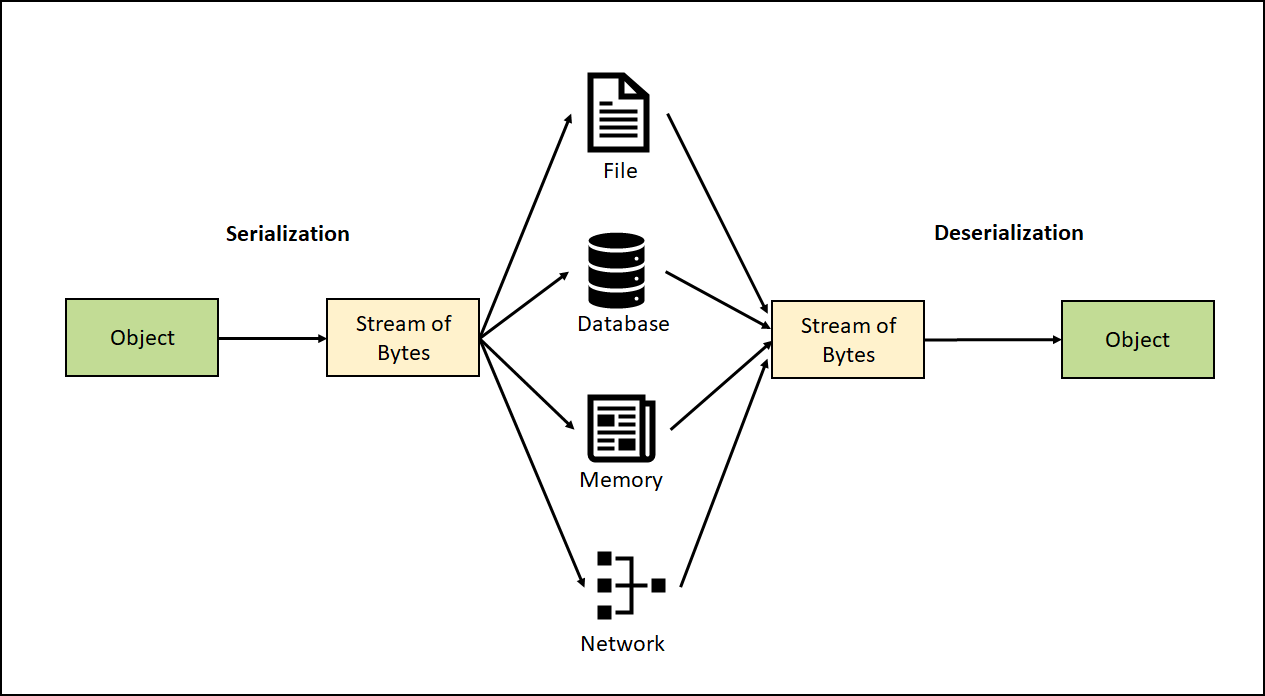
The goal of this writeup is to give a quick walkthrough of practical scenarios of Deserialization vulnerabilities that arise in many programming languages, specifically Java in our case, and how we can go from using a simple pre-built gadget chain to writing our own custom gadget chains and eventually gaining code execution on a target server.
Deserialization is the process of building a data object from a stream of bytes (objects and other complex data structures formatted in a certain manner):