The official website for this software: https://mcer.cn
Binary file repository for this software: https://gitcode.net/to/vlan/-/tree/master
The official tutorial for this software: https://docs.qq.com/aio/DTEpsR1lmbnZLQmln?p=gbkSEKVrKc6kV7qa6SLZ0y
This vulnerability is not an exploitable vulnerability, but is in fact a feature of the software itself, but the main problem with this feature is that the software vendor has too much control over the software user's device.
This feature allows the software vendor to connect to the target device via SSH protocol, and due to the special nature of the software, the software itself has administrator privileges, which is equivalent to a backdoor that can execute arbitrary commands.
Moreover, this feature is open to all users of the network, if not configured additionally, any user who uses the network and has the corresponding SSH private key will be able to use this backdoor to execute arbitrary commands on other users' devices without additional configuration.
- Two devices with access to the Internet
- This article uses two devices with
Debian 12 (Bookwarm)
- This article uses two devices with
- Two software licenses
Since I don't have this SSH private key file (nor am I likely to have it), here's just some evidence that the software has the above problems.
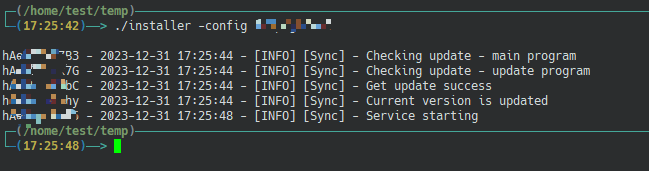
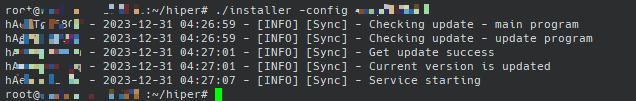
Currently we have two servers, I've named one of them "Attack Server" and the other "Target Server", for some reason I can't change the server hostname, so I'm going to use a different terminal theme to differentiate between the two servers, and note the two servers under the image.
Login to the network with a software license
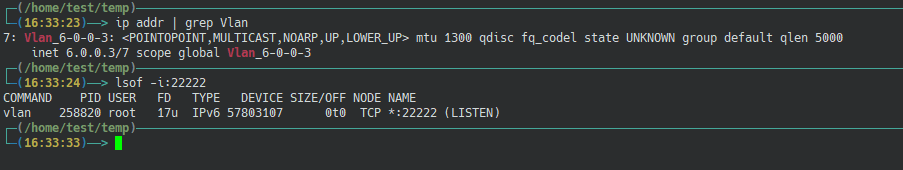
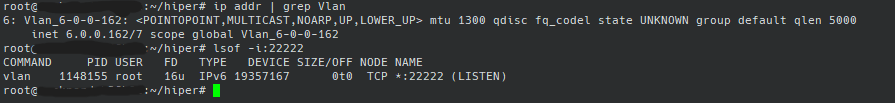
Check the IPs within the networks that the two servers are getting, and check the backdoor SSH ports open on both servers
According to the official tutorials, the names of the two networks should be Vlan_xxx
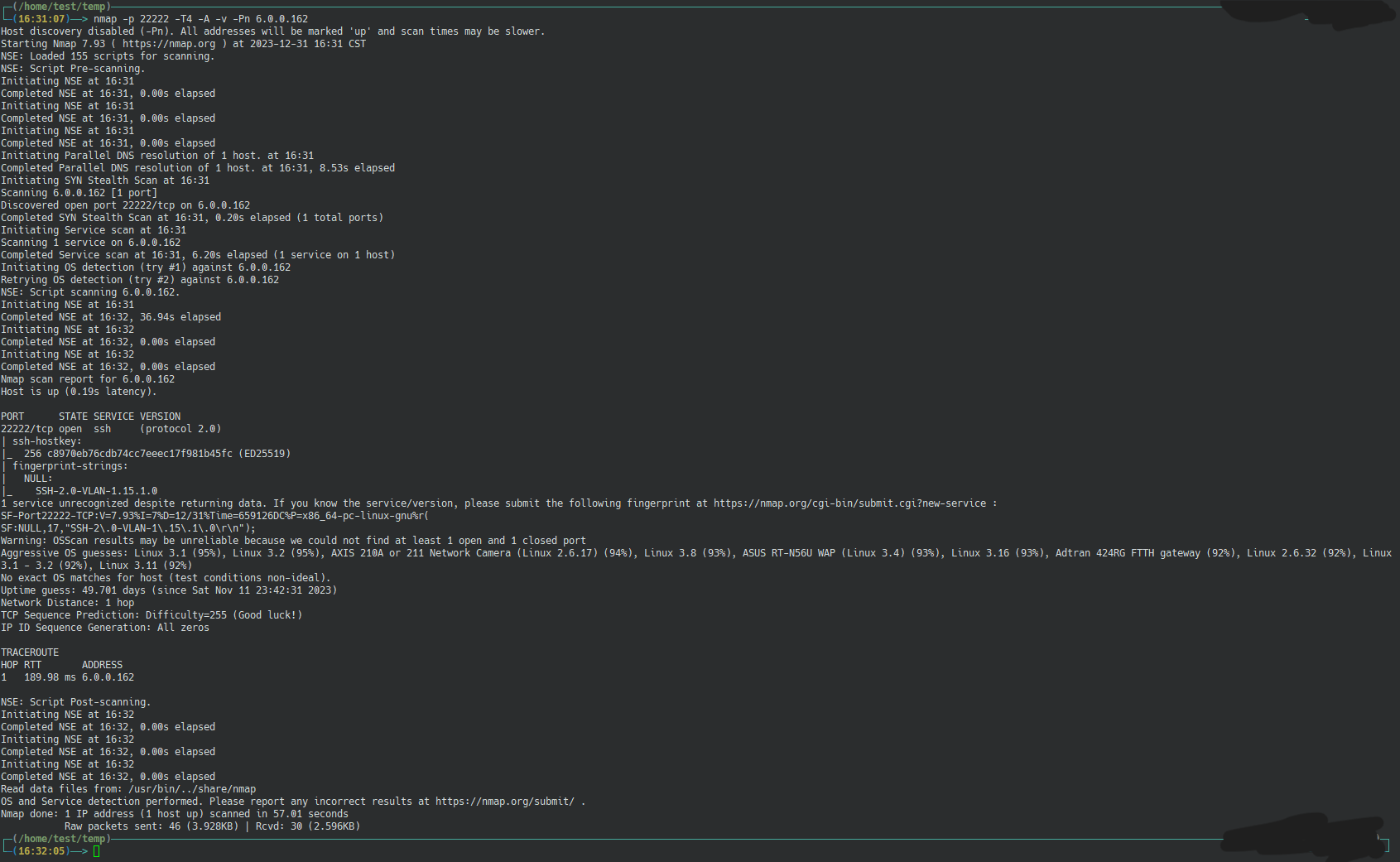
As you can see, the IPs of the two servers are 6.0.0.3 and 6.0.0.162, and both servers have port 22222 open.
- Attack Server IP:
6.0.0.3 - Target server IP:
6.0.0.162
Check the configuration file to make sure that no SSH services are configured (the configuration file is attached separately, with certificate and license related content filtered). Tips: The configuration file is here
Scan the target server with the nmap utility to characterize port openings
As you can see from the results on the graph, there is an SSH service on port 22222 of the target server that has an unknown SSH public key pair, and because the server is not firewalled, this SSH service can be accessed by anyone on the network
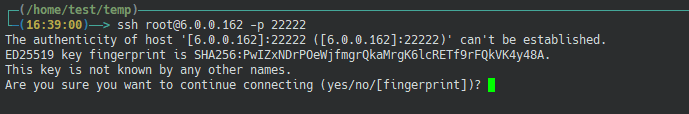
Here I tried to connect directly to the SSH service and found that the SSH service doesn't have any additional authentication other than the key, so if the SSH key is compromised, all users on the network without firewalls or other protections will be able to access the backdoor and do whatever they want
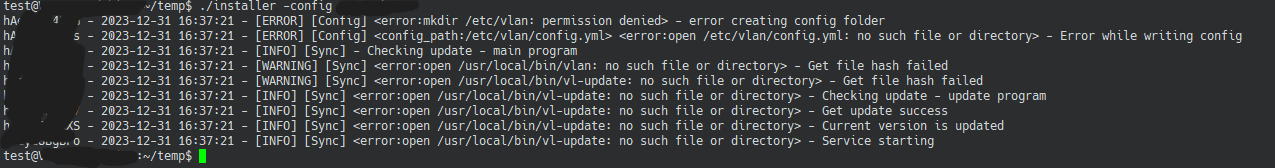
This is an addendum to the previous article, proving that the software cannot be run in non-administrator mode This test was run on the Attack server
Here I created a user without any privileges (including the sudo group) and executed this file, which, as you can see, contains a lot of error messages
This is the second step above, which obviously does not give the same output as above