- Ubuntu 18.04 (16.04 works the same)
- Apache 2.4.18 or higher
- OpenSSL 1.0.2g-1ubuntu4.10 or higher
- e.g. LetsEncrypt certificate
OS: Ubuntu 18.04 Apache/2.4.18 1.0.2g-1ubuntu4.10
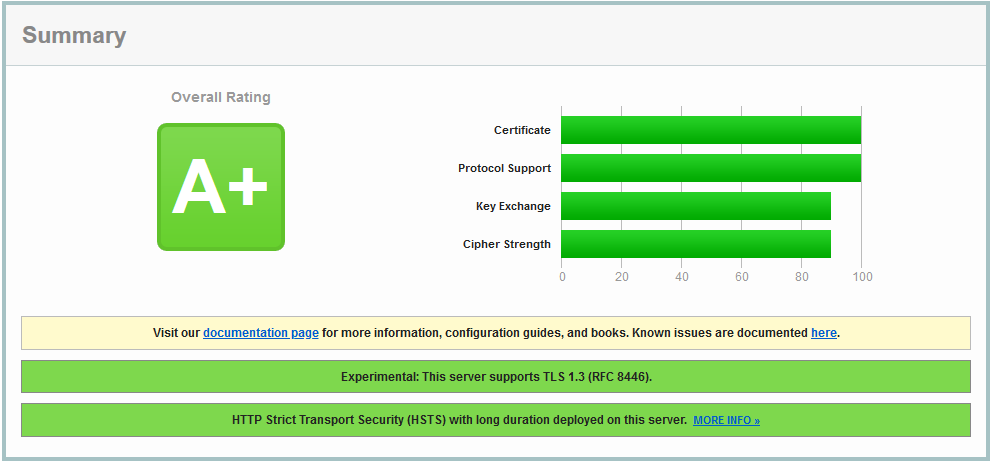
SSL Labs: A+ RSA 2048 bits (SHA256withRSA)
Certificate: 100%
Protocol Support: 100%
Key Exchange: 90%
Cipher Strength: 90%
Interesting is also --> https://mozilla.github.io/server-side-tls/ssl-config-generator/
Read how to enable HTTP2.0 afterwards --> https://gist.github.com/GAS85/990b46a3a9c2a16c0ece4e48ebce7300
sudo a2enmod headers
sudo service apache2 restart
NOTE: TLSv1.3 is now supported in Apache2 version 2.4.36 with OpenSSL 1.1.1. Since using of it will avoid such clients as Windows 7 I enable both TLS 1.2. and 1.3.
SSLCipherSUite "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH EDH+aRSA !CAMELLIA !SEED !3DES !RC4 !aNULL !eNULL !LOW !MD5 !EXP !PSK !SRP !DSS"
# This TLSv1.2 only
SSLProtocol TLSv1.2
# To use TLSv1.2 and TLSv1.3 uncomment line below and comment one above. Please read note above.
#SSLProtocol +TLSv1.2 +TLSv1.3
SSLCompression off
#enable of OCSP stapling, only in httpd 2.3.3 and later
SSLUseStapling on
SSLStaplingResponderTimeout 5
SSLStaplingReturnResponderErrors off
SSLStaplingCache shmcb:/var/run/ocsp(128000)
#if you want to add DHE (Diffie-Hellman key exchange) unkomment lines below AND RUN Command from "Optional" below
#SSLOpenSSLConfCmd Curves secp384r1
#SSLOpenSSLConfCmd DHParameters "/etc/ssl/certs/dhparam.pem"
ServerName YOUR.Server.com
SSLEngine on
SSLCertificateFile /etc/letsencrypt/live/YOUR.Server.com/cert.pem
SSLCertificateKeyFile /etc/letsencrypt/live/YOUR.Server.com/privkey.pem
SSLCertificateChainFile /etc/letsencrypt/live/YOUR.Server.com/chain.pem
#Header always set Strict-Transport-Security "max-age=15552000; includeSubDomains"
Header always set Strict-Transport-Security "max-age=15552000; includeSubDomains; preload"
sudo service apache2 restart
if you want to participate in Diffie-Hellman key exchange run and take a coffee:
sudo openssl dhparam -out /etc/ssl/certs/dhparam.pem 4096
after that uncomment last 2 lines in SSL.conf and restart apache2
If you would like to enable Certificate Pinning, please read here about: https://gist.github.com/GAS85/a668b941f84c621a15ff581ae968e4cb
P.S. if you would like to reduce amount of ciphers to use to minimum of most secured, please use one of following:
-
valid for all, but a lot of weaks Ciphers screenshot:
SSLCipherSuite HIGH:!aNULL -
valid for all, still a lot of weak Ciphers screenshot:
SSLCipherSUite "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH EDH+aRSA !CAMELLIA !SEED !3DES !RC4 !aNULL !eNULL !LOW !MD5 !EXP !PSK !SRP !DSS" -
still valid for all screenshot:
SSLCipherSUite "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:DHE-RSA-AES256-GCM-SHA384" -
IE11/WinPhone 8.1 will not be able to connect as also Safari before 9 screenshot:
SSLCipherSUite "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:DHE-RSA-AES256-GCM-SHA384" -
IE11 on all Windows devices, except Windows 10 will not be able to connect as also old Safari screenshot:
SSLCipherSUite "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384"