Gynvael’s Mission 15 (en): A writeup by Chris Warrick
(Spoilers ahead!)
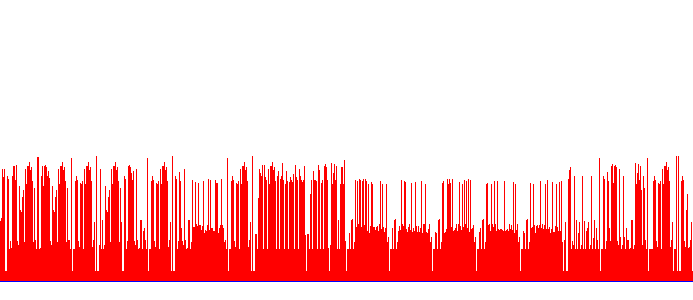
I started solving the mission by opening the chart with GIMP and measuring the first few lines. I found out that the first red bars are:
60 63 112 104 112 10 10
Then, I used Python’s chr() and converted them to letters. I got:
'<?php\n\n'
It became obvious that the height of every red bar is equal to an ASCII code. I wrote a short, hacky Python script using Pillow (02_read_chart.py) to count red pixels in each vertical line and convert it to text.
The result is 03_pass.php — a simple PHP script that checks a 25-character password using MD5. The password is checked twice: once as a whole, and then in 5-character sums. Brute-forcing 5-character strings is much easier than 25-character strings, so that can help us.
How do we proceed from now? A good way to start is to ask Google about each of the 6 sums. I actually found someone else’s solution (with passwords blanked out; I didn’t look any further at that). I also found the last sum — it’s ious!.
We can start brute-forcing now. I wrote yet another hacky Python script — 04_brute_md5.py, which uses Python 2 to avoid .encode() roundtrips. I started by running it with string.ascii_lowercase on all of the 5 fields, and I ended up with
*****harts*****delicious!
So, we can start guessing. Those are bar charts, so perhaps the first part is bar?c? Well, not quite. I started a brute-everything (all printable ASCII) process in the background, but also tried other guesses. Eventually I found that the middle fragment is are (with spaces around). Then another idea came to me: perhaps “bar” misled me there? I tried pie?c — and sure enough, Pie c matched the first fragment.
Final password: Pie charts are delicious!