-
-
Save LukeMathWalker/5ae1107432ce283310c3e601fac915f3 to your computer and use it in GitHub Desktop.
| name: Security audit | |
| on: | |
| schedule: | |
| - cron: '0 0 * * *' | |
| push: | |
| paths: | |
| - '**/Cargo.toml' | |
| - '**/Cargo.lock' | |
| jobs: | |
| security_audit: | |
| runs-on: ubuntu-latest | |
| steps: | |
| - uses: actions/checkout@v3 | |
| - uses: taiki-e/install-action@cargo-deny | |
| - name: Scan for vulnerabilities | |
| run: cargo deny check advisories |
| name: Rust | |
| on: [push, pull_request] | |
| env: | |
| CARGO_TERM_COLOR: always | |
| jobs: | |
| test: | |
| name: Test | |
| runs-on: ubuntu-latest | |
| steps: | |
| - uses: actions/checkout@v3 | |
| - uses: dtolnay/rust-toolchain@stable | |
| - uses: Swatinem/rust-cache@v2 | |
| - name: Run tests | |
| run: cargo test | |
| fmt: | |
| name: Rustfmt | |
| runs-on: ubuntu-latest | |
| steps: | |
| - uses: actions/checkout@v3 | |
| - uses: dtolnay/rust-toolchain@stable | |
| with: | |
| components: rustfmt | |
| - name: Enforce formatting | |
| run: cargo fmt --check | |
| clippy: | |
| name: Clippy | |
| runs-on: ubuntu-latest | |
| steps: | |
| - uses: actions/checkout@v3 | |
| - uses: dtolnay/rust-toolchain@stable | |
| with: | |
| components: clippy | |
| - uses: Swatinem/rust-cache@v2 | |
| - name: Linting | |
| run: cargo clippy -- -D warnings | |
| coverage: | |
| name: Code coverage | |
| runs-on: ubuntu-latest | |
| container: | |
| image: xd009642/tarpaulin | |
| options: --security-opt seccomp=unconfined | |
| steps: | |
| - name: Checkout repository | |
| uses: actions/checkout@v3 | |
| - name: Generate code coverage | |
| run: | | |
| cargo tarpaulin --verbose --workspace |
This is mine, can you review please -> https://gist.github.com/steelx/3d863ceff5ebe0a147b632ff93069991
Deployment is out of scope for this pipeline.
Any reason not to use:
- uses: actions-rs/toolchain@v1
with:
profile: minimal
toolchain: stable
override: true
components: rustfmt
``` vs the separate call to install rustfmt?
Not really! I'll amend it in the next release 😁
Instead of running clippy manually, you can use actions-rs/clippy-check, it can annotate the commit or pull request like this:
The job would look something like this:
jobs:
clippy:
name: Clippy
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v1
- uses: actions-rs/toolchain@v1
with:
toolchain: stable
components: clippy
override: true
- uses: actions-rs/clippy-check@v1
with:
token: ${{ secrets.GITHUB_TOKEN }}Updated both, thank you!
Two audit configs can be easily combined:
name: Security audit
on:
push:
paths:
- '**/Cargo.toml'
- '**/Cargo.lock'
schedule:
- cron: '0 0 * * *'
jobs:
audit:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v1
- uses: actions-rs/audit-check@v1
with:
token: ${{ secrets.GITHUB_TOKEN }}@mattjperez Which token are you using? GitHub Actions will create secrets.GITHUB_TOKEN for you at the start of each run (and expire it at the end), it should work fine for all of the actions here.
@00-matt Works now, thanks for that. I didn't know about GITHUB_TOKEN being generated on each run. I had made a secret directly with repo permissions and was using that at the time of this error.
It looks as if https://github.com/actions-rs/audit-check/pulls has a lot of automated security pull requests from GitHub, dating back to september 10th 2020 👀👀... I wonder if the packages are still maintained?
It looks as if https://github.com/actions-rs/audit-check/pulls has a lot of automated security pull requests from GitHub, dating back to september 10th 2020 eyeseyes... I wonder if the packages are still maintained?
https://github.com/EmbarkStudios/cargo-deny-action looks pretty good. It uses cargo deny rather than cargo audit, of course.
I took a Clippy error that said "Resource not accessible by integration". If you get this error, you need to change "Workflow permissions" into "Read and write permissions" instead of "Read repository contents permission". It's in the "Actions" section under the repository settings.
Terrific job @LukeMathWalker . Does anybody know how to generate code coverage badge for README.md based on the tarpaulin's job?
Thanks for including this in your book
What about including udeps(allows to find unused dependenscies), it can be useful in some cases?
It looks as if https://github.com/actions-rs/audit-check/pulls has a lot of automated security pull requests from GitHub, dating back to september 10th 2020 eyeseyes... I wonder if the packages are still maintained?
https://github.com/EmbarkStudios/cargo-deny-action looks pretty good. It uses cargo deny rather than cargo audit, of course.
This is true for everything in actions-rs as far as I can tell! This seems ... bad
Could you add a LICENSE to that? Assuming MIT, but for legal reasons a proper license notice would be great
ISTM this is a little outdated. actions-rs is unmaintained and has a couple bugs now. Instead, can use dtolnay to implement this CI pipeline.
Updated per @ryanrozanitis comment:
name: Rust
on: [push, pull_request]
env:
CARGO_TERM_COLOR: always
jobs:
test:
name: Test
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v3
- uses: dtolnay/rust-toolchain@stable
- run: cargo test --all-features
fmt:
name: Rustfmt
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v3
- uses: dtolnay/rust-toolchain@stable
- run: cargo fmt --all -- --check
clippy:
name: Clippy
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v3
- uses: dtolnay/rust-toolchain@stable
- run: cargo clippy -- -D warnings
coverage:
name: Code coverage
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v3
- uses: dtolnay/rust-toolchain@stable
- run: cargo install cargo-tarpaulin
- run: cargo tarpaulin --ignore-tests
All actions have been updated - they no longer rely on actions-rs 🎉
Sorry for the delay!
I think checkout@v3 needs to be updated to v4 since Node 16 EOL
@LukeMathWalker - Brother this really could use a short link or something man. Us Printed copy enjoyers are crying over the url length. Maybe a QR Code?
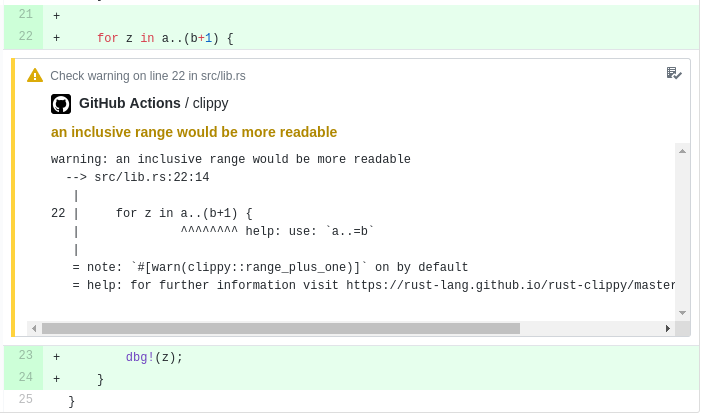

can you also add build step with GCP