- In layman's terms: Protecting computers from theft or damage
- In more technical terms:
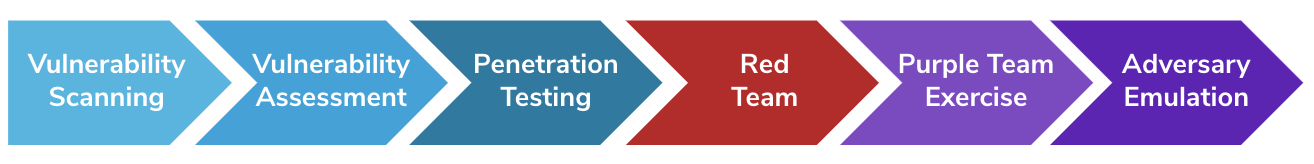
- Penetration Testing
- Vulnerability Assessment
- "Ethical Hacking"
- Cyber Defence
- Threat Monitoring
- Threat Hunting
- Threat Intelligence
- Counter-Espionage
- Cyber Warfare
- A lot more!
- We depend more on technology
- Threats and attacks against tech we use every day are popular as ever
- Attackers are no longer script kiddies or hackers having fun when everyone else is asleep
- APT Groups, Governments, and Cybercrime Gangs/Companies are now actively trying to attack their enemies:
- Damaging their reputation
- Stealing from them
- Destroying or disabling their infrastructure
- Examples:
- APT14 (Allegedly) --> PoisonIvy Rootkit (Popularly used, especially by Molerats, a Palestinian hacker group)
- USA/Israel (Allegedly) --> Stuxnet attack on Iran's Nuclear Plants (2010)
- Conti Ransomware (Rebranded into 3 other companies in late 2022): Huge cybercrime group with over 350 members, and HR department, recruiters, and $2.7 billion in revenue through cryptocurrency in only one year
Conti Ransomware and its family rebranding
Now to the big question, where do we geeks, developers, and infosec researchers fit in all this?
Mainly responsible for defending, responding, and improving defence capabilities.
Log --> Alert --> Respond
- Security Operations Center
- Incident Response
- Digital Forensics
- Malware Analysis
- Compromise Assessment
- Threat Hunting
- Threat Intelligence
- Vulnerability Assessment
- Network and Security Appliances Configuration Review?
- Governance, Risk, and Compliance (GRC) Auditing?
Responsible for finding security holes, exploiting them, and reporting them without causing any real damage.
- Penetration Testing
- Phishing
- Spearphishing
- Email Phishing
- SMS
- Vishing
- Social Engineering
More of a virtual team: pretty much a mix between the two teams, responsible for enhancing the process of both teams.
- Adversary Emulation
- Detection Enhancement
- Red Team Exercise Automation
SCYTHE’s Ethical Hacking Maturity Model
In Egypt, there is quite a bit of limited role types. However, the market is booming and growing.
- Security Operations Center (SOC) Analyst (T1/T2)
- Threat monitoring
- Responding to threats
- Sometimes, threat hunting
- Digital Forensics and Incident Response Engineer
- Responding to larger escalated threats
- Performing deep-dive forensics when it is required
- Enhancing detection and response through playbooks and use cases
- Network Security Engineer/Security Infrastructure Engineer
- Responsible for network security infrastructure
- Network services, AD Security, Security Appliances etc... are usually part of their responsibility
- SIEM Admin
- Responsible for managing and tuning the SIEM for the SOC
- Threat Hunter (Usually a SOC T2, sometimes T3)
- Usually, a senior SOC analyst who is designated to perform threat hunting activities
- Penetration Tester: Mobile, Desktop, Web, etc...
- Cybersecurity Engineer
- A bit of a generic title, you could be doing anything
- Mostly I've seen it with red team jobs
- When I had the title, I did mobile penetration testing, reverse engineering, red teaming activities (phishing simulations), DFIR, and desktop app penetration testing
- GRC Specialist/Consultant
- Responsible for auditing governance, risk, and compliance for clients or internally
- Relevant standards include: PCI/DSS, ISO 27001, and some others
- Security-oriented development roles
- Not that common in Egypt
- Some companies hire developers specifically to make sure the apps get secured properly
In other parts of the world, there are many other roles which are related directly or indirectly to Cybersecurity. For the sake of time and brevity, I won't get into them. Feel free to check LinkedIn, GlassDoor, and any other website where you can find job titles and then just look up what they do.
The good ol' question, how do I get started in Cybersecurity?
Well, there isn't one route. As a matter of fact, I don't actually have a route to recommend. However, I can try and tell you what to study based on what you want to do!
Relevant:
- Blog Post by yours truly regarding how there isn't a single roadmap: https://satharus.me/tech/2022/05/08/there_is_no_single_roadmap.html
- YouTube video by LiveOverflow regarding how to start: https://youtu.be/2TofunAI6fU
-
Introduced to roughly what cybersecurity is in 2016 (2nd/3rd year of high school)
-
Learned some tiny bits of general computer knowledge and programming until 2017
-
Joined FCIS, ASU in 2017 (Thus joining OSC)
- Our Linux head, Maha Amin, told us about CyberTalents' new CTF platform
- We started solving it for a while as a fun exercise
- I started learning what security actually is
- I attended CyberTalent's Ain Shams CTF in September 2018, and I came in 2nd place with my team
-
Attended CSCamp in Late 2018
- Introduced to reverse engineering through an inspiring research talk by Dr. Ahmed Shosha
-
Started studying reverse engineering and assembly in early 2019 from OpenSecurityTraining.info (check the resources section)
-
From 2019 to 2020: I kept attending Cybersecurity Conferences and studying random security topics related to what I was interested in: Reverse Engineering, Forensics, etc...
-
January 2020: I got my first job as a SOC analyst at MNZ Technology Solutions
-
April 2020: I moved to the Cybersecurity Services team at MNZ as I knew reverse engineering
- In this role (Cybersecurity Engineer), I learnt a lot more about forensics, system internals, and incident response
Note: Up until this moment, I genuinely still had no idea what I wanted to do in Cybersecurity. All knew was that I loved Cybersecurity, low level stuff, and reverse engineering.
-
January 2021: I moved to Cyber Castle for a DFIR Engineer position
-
From 2021 to early 2023:
- I worked in the same position for ~2 years
- During my military conscription(obligatory in Egypt), I studied LOTS of topics related to hardware and firmware attacks and security on the side. What helped me to understand such topics was a knowledge of electronics, OS internals, computer architecture, etc...
- Worth noting that this had been an area of my interest ever since I started studying cybersecurity and it became even more interesting to me when I started working. So, this wasn't my first exposure to such topics!
- My experience in DFIR, red team activities, and cyber defence definitely helped when studying such topics
- I also learned that reading is one of the good things you can do to pass time and also benefit from it
-
June 2023: I joined HP Inc. UK as a Hardware & Firmware Threat Research Analyst
As you can see, my path wasn't direct and wasn't planned. Yours won't be either. Each person has their own path.
Also, you can see that I shifted a couple of times between different cybersecurity fields. The only thing being consistent between all of my career phases is always trying to do/learn something and not just waiting for glory. Also, having quite a bit of basics helped me learn different topics a bit easier. This also proves the point that no knowledge is useless. Knowledge will add up eventually and serve whatever you want to do.
Take this with a grain of salt. You don't have to do exactly this, I am just trying to put a general guideline.
- First thing, remove the "I don't like this" mentality. You will have to learn stuff you don't like. You may delay studying them a bit but eventually, you will bump into them in your day-to-day job.
- I, for one, had to learn PowerShell. The funny thing is, I actually started to like it after working with it for a while!
- Make sure you're familiar with network and OS fundamentals:
- Linux
- Familiar with the Shell
- Familiar with the general structure of the OS, the filesystem, etc... (A very basic overview)
- Windows:
- Familiar with internals such as the registry, services, filesystems, etc...
- Familiar with the command prompt and PowerShell
- General OS concepts and definitions:
- Processes and Services
- Filesystem
- Logging
- Crashes and Errors
- Networking:
- IPs and Ports
- MAC Addresses
- Type of network connections
- NATing and Port Forwarding
- Linux
- Then, decide whether you want to start doing blue team or red team activities
- How? CTFs!
- Check the resource section for CTF platforms and a video on how to utilise CTFs properly
- After you've decided on what you want to do, start studying more specialised topics according to what you like
- You could actually start with CTFs before studying the basics and learn them as you go. It was what I mostly did. That depends on what you feel like doing. Having good fundamentals never hurts, though.
Side note: You may want to look at So, You Wanna Do Security ?, it is a very detailed video by Mohamed Gamal. He put a huge effort into it and talks about a lot of the key points. You can check the description, look for the job you want, and then listen to what he has to say about it. This video was recommended by my dear friend Islam Mostafa, who co-authored this video with Mohamed and also put a huge effort into it.
- MITRE ATT&CK
- MITRE D3FEND
- Admin has the Power on CyberTalents
- XSS-Game
- Reverse Engineering Challenge
- DFIR Challenge
- The Art of Cybersecurity (And how to get into it): A blog post I wrote before that discusses some of the stuff we discussed here and had more resources
- Linux Tutorial for Beginners Playlist
- OSC19-Linux-Workshop-Sessions
- CompTIA N10-008 Network+ by Professor Messer
- General Computer Science Crash Course by CrashCourse
- The Triad of Success: Education, Experience, and Networking w/ Wade Wells (starts 32:22)
- YouTube Video by LiveOverflow: How To Learn Hacking With CTFs
- PicoCTF
- CyberTalents
- Root-Me
- fareedfauzi.github.io/ctfonline
- CTF Time
- OverTheWire
- LetsDefend: Comprehensive SOC traning and Introductory DFIR training
- CyberDefenders: SOC and DFIR scenarios practice
- OpenSecurityTraining 2.0: More deep cybersecurity training, with subjects related to OS internals, computer architecture, reverse engineering, firmware security, and digital forensics
- OpenSecurityTraining Legacy: An older version of OpenSecurityTraining 2.0, still has a lot of great up-to-date training and it is where I personally started.
- 13Cubed YouTube Channel: Outstanding Resource for everything DFIR
- Cyber Triage/Autopsy DFIR Training
- Forensics – CTF Field Guide
- Malware Unicorn
- Begginers.re
- Incident Response Methodologies by CERT Societe Generale
- Reverse Engineering for Everyone!
- Web Application Penetration Testing Course Instructed by Ebrahim Hegazy: Comprehensive course in Arabic about web penetration testing and getting started with bug bounty programs
- Hacker 101: A course by HackerOne, a bug bounty program platform
- Cybrary: A cybersecurity training platform
- HackTheBox: A website where you can practice "pwn"ing full machines, performing the full attack scenario from Initial Access to as far as you can get!
- TryHackMe
- VulnHub
- Mastering Modern Web Penetration Testing by Prakhar Prasad
- The Tangled Web: A Guide to Securing Modern Web Applications by Michal Zalewski
- OWASP Top 10
Make sure to check the blog post under General Resources to see more resources.
- Caisec
- Arab Security Conference
- BSides Cairo
- Egypt Cybersecurity & Defense Intelligence Systems Conference
- The Future of Data Centers
- Cairo Security Camp
- State of Security
- Let's Play CTF (Learn By Doing)
- كورس_Pentesting_بالعربي
- CyberTalents Community - Ain Shams University
- Follow people in the industry
- Interact with posts, share resources, and get known in the community!
- Cyber Castle
- Cyshield
- Zinad IT
- Security Meter
- Fawry
- Orange
- RedForce
- EG-CERT
- EG-FinCERT
- Binary Keep
- Cysiv MEA
- CYarm
- BARQ Systems
- Jafeer
- Information Technology Solutions
- Optima
- Iken
- Spark Engineering Consultants
- InovaSys
- IP Protocol INC
- Fixed Solutions
- CyberTalents
This is some general advice I have for anyone starting out in pretty much anything, but I have tailored some of the advice for cybersecurity.
- Do something, doesn't matter what it is. Doing something is always better than nothing.
- Learn anything you can. If you don't feel like learning what's in your " studying path", then do something else but don't waste time waiting to find motivation
- Want to write your own malware even though you're a blue teamer? DO IT! It is fun. I personally have and learnt a ton from it
- Don't let your "specialisation" hold you back from trying new stuff or learning things that interest you
- Connect with the community, it genuinely helps on both the technical, professional, and personal levels.
- Some areas of Facebook
- Reddit has a couple of good subs
- Follow the cybersecurity news, this isn't an advertisement but I really enjoy reading the following email newsletters:
- Listen to Podcasts instead of music on your commutes or maybe when you're doing other activities such as running or cooking. I personally really enjoy music so this was hard for me to do, but sometimes I still manage it. I like Darknet Diaries by Jack Rhysider.
- Cybersecurity (and computers in general) may be a bit overwhelming at the start, don't let that get to you. Focus on one thing at a time and leave the rest for later.
- Don't worry about certifications at the start of your career, those come later and you will find out what you want or need to certify in sooner than later.
- It's a fast moving career, no advice or resource recommendation stays constant and accurate for long.
- Latest Revision: V1.8 - 26/07/2024
- Changelog:
- V1.8: Added "Reverse Engineering for Everyone!" to blue team resources
- V1.7: Added Antisyphon talk by Wade Wells
- V1.6: Added an update to my path, fixed some typos, made the doc clearer
- V1.5: Added Dr. Ahmed Shosha's talk
- V1.4: Added Caisec
- V1.3: Added IRM by CERT Societe Generale
- V1.2: Added HackTheBox, TryHackMe, VulnHub
- V1.1: Added Mohamed and Islam's video
- V1.0: Initial Version before the session
- This work is licensed under a Attribution-NonCommercial-ShareAlike 4.0 International license.
- Meaning you are free to:
- Share — copy and redistribute the material in any medium or format
- Adapt — remix, transform, and build upon the material
- Under the following terms:
- Attribution — You must give appropriate credit, provide a link to the license, and indicate if changes were made.
- NonCommercial — You may not use the material for commercial purposes.
- ShareAlike — If you remix, transform, or build upon the material, you must distribute your contributions under the same license as the original.



Great Material! Thank youuu