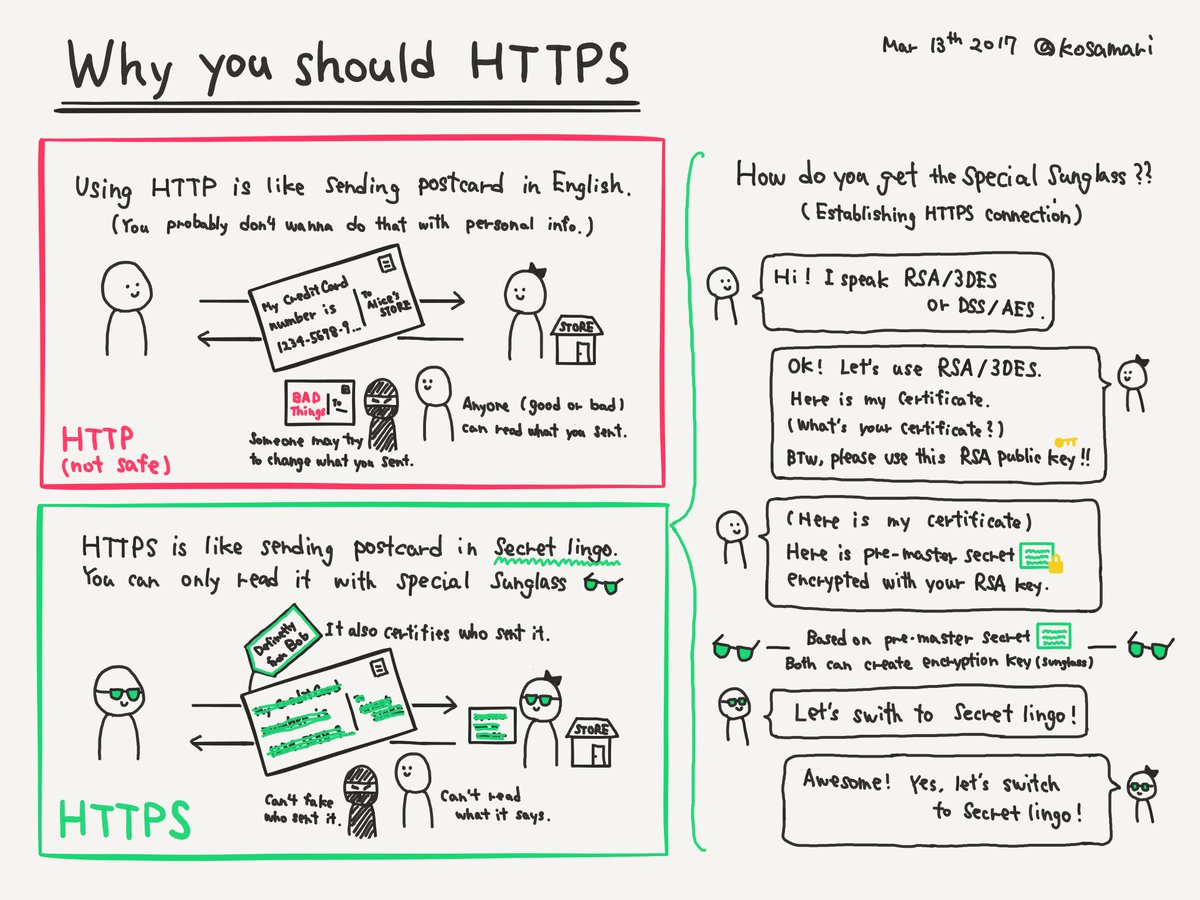
Collection on all things HTTPS. Includes settings for TLS on nginx (which desperately need an update!).
Until I update this, I'd recommend you take a look at https://github.com/jukbot/setup-nginx-webserver
See https://www.nginx.com/resources/wiki/start/topics/tutorials/install/#official-debian-ubuntu-packages on how to install the lastest version of nginx.
Most settings are sourced from https://bettercrypto.org/static/applied-crypto-hardening.pdf#subsection.2.1.3, https://danpalmer.me/blog/ssl-labs-grade-a, https://gist.github.com/plentz/6737338 and https://scotthelme.co.uk/
I'm a newbie to large scale webhosting, but really interested in it. This is my take on a nginx config to deploy on my servers.
So if you find a way to do something better: Please leave a comment! Thanks!
- https://www.ssllabs.com/ssltest/
- https://www.htbridge.com/ssl/
- https://tools.keycdn.com/http2-test
- http://www.whatsmyip.org/http-compression-test/
- https://observatory.mozilla.org/
- https://tools.pingdom.com/
- https://tools.geekflare.com/
- https://github.com/s-rah/onionscan/blob/master/doc/what-is-scanned-for.md
- https://securityheaders.io/
- https://hstspreload.org/
- https://report-uri.io/
- https://testssl.sh/ / https://github.com/drwetter/testssl.sh
- https://internet.nl/
- https://www.hardenize.com/
- https://tlsinspector.com/
- https://developers.google.com/web/updates/2015/12/security-panel
- https://www.owasp.org/index.php/Transport_Layer_Protection_Cheat_Sheet
- https://wiki.mozilla.org/Security/Server_Side_TLS
- https://movingtohttps.com/
- https://www.aptive.co.uk/blog/tls-ssl-security-testing/
- https://mozilla.github.io/server-side-tls/ssl-config-generator/
- https://media.ccc.de/v/eh16-62-zeitgemasse_webserver-konfiguration_--_ein_serviervorschlag
- https://hstspreload.org/
- https://weakdh.org/sysadmin.html
- h5bp/server-configs-nginx#72
- https://scotthelme.co.uk/hardening-your-http-response-headers/
- https://geekflare.com/nginx-webserver-security-hardening-guide/
- https://www.keycdn.com/blog/x-frame-options/
- https://geekflare.com/add-x-frame-options-nginx/
- https://www.upguard.com/articles/10-tips-for-securing-your-nginx-deployment
- https://geekflare.com/http-header-implementation/
- https://www.keycdn.com/blog/http-security-headers/
- http://vincent.bernat.im/en/blog/2011-ssl-session-reuse-rfc5077.html
- http://en.wikipedia.org/wiki/Clickjacking
- https://developer.mozilla.org/en-US/docs/HTTP/X-Frame-Options
- https://www.owasp.org/index.php/List_of_useful_HTTP_headers
- https://forum.joomla.org/viewtopic.php?t=845318#p3313092
- https://www.digicert.com/ssl-certificate-installation-nginx.htm
- https://www.digitalocean.com/community/tutorials/how-to-set-up-nginx-with-http-2-support-on-ubuntu-16-04
- https://stackoverflow.com/questions/17413526/nginx-missing-sites-available-directory
- https://serverfault.com/questions/775298/debian-jessie-nginx-with-openssl-1-0-2-to-use-alpn-rather-than-npn
- https://www.cyberciti.biz/faq/linux-unix-nginx-access-control-howto/
- https://www.sslshopper.com/ssl-converter.html
- https://www.nginx.com/blog/nginx-ssl/
- http://www.westphahl.net/blog/2012/01/03/setting-up-https-with-nginx-and-startssl/
- https://www.markbrilman.nl/2011/08/howto-convert-a-pfx-to-a-seperate-key-crt-file/
- https://easyengine.io/tutorials/nginx/enable-gzip/
- https://askubuntu.com/questions/553937/what-is-the-difference-between-the-core-full-extras-and-light-packages-for-ngi
- https://certbot.eff.org/#ubuntuxenial-nginx Always use "letsencrypt certonly" to avoid the automatic installation messing up your config.
- https://jefferytay.wordpress.com/2010/12/09/converting-a-pfx-file-to-pem-and-key-via-openssl/
- https://security.stackexchange.com/questions/79519/ssl-tls-how-to-fix-chain-issues-contains-anchor
- https://ssl.comodo.com/support/creating-a-pem-file.php / https://support.comodo.com/index.php?/Knowledgebase/List/Index/71
- https://superuser.com/questions/644343/how-do-you-fix-an-incomplete-ssl-chain
- https://certificatechain.io/
- https://community.qualys.com/docs/DOC-1931
- https://community.qualys.com/thread/11685
- https://www.nginx.com/blog/http-strict-transport-security-hsts-and-nginx/
- https://gist.github.com/konklone/6532544
- https://scotthelme.co.uk/hsts-the-missing-link-in-tls/
- https://scotthelme.co.uk/setting-up-hsts-in-nginx/
- https://scotthelme.co.uk/hsts-preloading/
- https://www.netsparker.com/web-vulnerability-scanner/vulnerability-security-checks-index/http-strict-transport-security-hsts-max-age-value-too-low/
- https://https.cio.gov/hsts/
- https://blog.qualys.com/securitylabs/2016/03/28/the-importance-of-a-proper-http-strict-transport-security-implementation-on-your-web-server
- https://en.wikipedia.org/wiki/HTTP_Strict_Transport_Security
- https://www.owasp.org/index.php/HTTP_Strict_Transport_Security_Cheat_Sheet
- https://open.blogs.nytimes.com/2014/11/13/embracing-https/
- https://bits.blogs.nytimes.com/2015/10/14/encryption-is-more-important-and-easier-than-ever/
- https://www.theguardian.com/info/developer-blog/2016/nov/29/the-guardian-has-moved-to-https
- http://www.niemanlab.org/2015/07/s-is-for-secure-why-news-organizations-are-ditching-or-should-ditch-http-for-https/
- https://freedom.press/news/introducing-secure-news-automated-tool-tracking-adoption-https-encryption-across-news-websites/
- https://securethe.news/
- https://twitter.com/tlsallthethings
- https://www.eff.org/encrypt-the-web-report
- http://maulwuff.de/research/ssl-debugging.html
- https://www.maxcdn.com/blog/ssl-performance-myth/
- https://github.com/ssllabs/research/wiki/SSL-and-TLS-Deployment-Best-Practices
- https://github.com/ssllabs/research/wiki/SSL-Server-Rating-Guide
- https://www.techandme.se/set-up-nginx-reverse-proxy/
- https://nginx.org/en/docs/http/server_names.html
- https://www.troyhunt.com/understanding-http-strict-transport/
- https://gist.github.com/StefanWallin/5690c76aee1f783c3d57
- https://www.linode.com/docs/security/ssl/install-lets-encrypt-to-create-ssl-certificates
- https://www.digicert.com/ssl-certificate-installation-nginx.htm
- https://www.digitalocean.com/community/tutorials/how-to-configure-nginx-as-a-reverse-proxy-for-apache
- https://https.cio.gov/
- https://scotthelme.co.uk/alexa-top-1-million-analysis-feb-2017/
- https://www.feistyduck.com/
- https://www.feistyduck.com/books/bulletproof-ssl-and-tls/
- https://www.feistyduck.com/bulletproof-tls-newsletter/
- https://www.hardenize.com/
- https://badssl.com/
- https://www.feistyduck.com/ssl-tls-and-pki-history/
- https://mitmproxy.org/
- https://media.ccc.de/v/33c3-8348-deploying_tls_1_3_the_great_the_good_and_the_bad
- https://noncombatant.org/2017/02/15/decoding-chromes-https-ux/
- https://blog.mozilla.org/security/2017/01/20/communicating-the-dangers-of-non-secure-http/
- https://timtaubert.de/blog/2017/02/the-future-of-session-resumption/
- https://scotthelme.co.uk/ocsp-must-staple/
- https://jve.linuxwall.info/ressources/taf/HTTPSBsidesTampa17/#/
- https://jhalderm.com/pub/papers/interception-ndss17.pdf
- https://blog.appcanary.com/2017/http-security-headers.html
- https://blogs.akamai.com/2017/01/tls-13-ftw.html
- https://f5.com/labs/articles/threat-intelligence/ssl-tls/the-2016-tls-telemetry-report-24674
- https://www.eff.org/deeplinks/2016/12/what-happened-crypto-2016
- https://www.feistyduck.com/bulletproof-tls-newsletter/issue_23_2016_the_year_https_became_dominant.html
- https://blog.pki.dfn.de/2015/03/mehr-privacy-fuer-den-nutzer-ocsp-stapling/ (german, see the next link for english)
- https://www.maxcdn.com/one/visual-glossary/ocsp-stapling/ (english)
- https://www.keycdn.com/support/ocsp-stapling/
- https://www.digitalocean.com/community/tutorials/how-to-configure-ocsp-stapling-on-apache-and-nginx
- https://www.digicert.com/ssl-support/nginx-enable-ocsp-stapling-on-server.htm
- https://scotthelme.co.uk/content-security-policy-an-introduction/
- https://content-security-policy.com/
- https://scotthelme.co.uk/a-new-security-header-referrer-policy/
- https://www.pcisecuritystandards.org/documents/Migrating_from_SSL_Early_TLS_Information%20Supplement_v1.pdf
- https://letsencrypt.org/stats/
- https://www.httpvshttps.com/
- https://www.keycdn.com/blog/http2-statistics/
- https://zakird.com/papers/https_interception.pdf
- https://www.us-cert.gov/ncas/alerts/TA17-075A
- https://ssllabs.com/ssltest/clients.html
- https://www.troyhunt.com/https-adoption-has-reached-the-tipping-point/
- https://observer.com/2017/03/redtube-https-security-xvideos-thumbzilla/
- https://www.cloudflare.com/website-optimization/http2/what-is-http2/
- https://blog.cloudflare.com/encryption-week/
- https://blog.cloudflare.com/introducing-tls-1-3/
- https://blog.cloudflare.com/tls-1-3-overview-and-q-and-a/
- https://blog.cloudflare.com/introducing-0-rtt/
- https://www.bsi.bund.de/DE/Themen/ITGrundschutz/ITGrundschutzKataloge/Inhalt/_content/m/m05/m05066.html
- https://www.nginx.com/blog/free-certificates-lets-encrypt-and-nginx/
- https://community.letsencrypt.org/t/is-it-possible/15132
- https://blog.qualys.com/ssllabs/2013/08/07/defending-against-the-breach-attack
- http://breachattack.com/
- https://jlospinoso.github.io/node/javascript/security/cryptography/privacy/2017/02/20/snuckme-cert-query.html
- It's an ad and they say SSL, but it explains stuff well: https://vimeo.com/135666049
- https://permission.site/
- https://www.golem.de/news/tls-1-3-die-zukunft-der-netzverschluesselung-1612-124724.html (german)
- http://mailman.nginx.org/pipermail/nginx-announce/2017/000195.html
- https://www.golem.de/news/webserver-nginx-1-13-erscheint-mit-tls-1-3-support-1704-127503.html (german)
- https://wiki.openssl.org/index.php/Compilation_and_Installation
- https://istlsfastyet.com/
- https://tlswg.github.io/
- https://security.stackexchange.com/questions/94390/whats-the-purpose-of-dh-parameters
- https://www.youtube.com/watch?v=dCvB-mhkT0w ECC
- https://www.youtube.com/watch?v=YEBfamv-_do DH
- https://www.youtube.com/watch?v=wXB-V_Keiu8 RSA
- https://www.nginx.com/resources/wiki/start/topics/examples/reverseproxycachingexample/
- https://www.nginx.com/blog/nginx-caching-guide/
- https://www.nginx.com/resources/admin-guide/content-caching/
- https://www.digitalocean.com/community/tutorials/understanding-nginx-http-proxying-load-balancing-buffering-and-caching
- https://tweaked.io/guide/nginx-proxying/
- mozilla/server-side-tls#135
- https://productforums.google.com/forum/#!topic/chrome/UBp_FtxonXU
- https://www.bjornjohansen.no/optimizing-https-nginx
- http://blog.commando.io/the-perfect-nginx-ssl-configuration/
- https://leandromoreira.com.br/2015/10/12/how-to-optimize-nginx-configuration-for-http2-tls-ssl/
- https://www.cyberciti.biz/faq/linux-unix-bsd-nginx-413-request-entity-too-large/
- https://drownattack.com/
- https://www.google.com/transparencyreport/https/
- https://motherboard.vice.com/en_us/topic/encrypt-all-the-things
- https://www.imperialviolet.org/2010/06/25/overclocking-ssl.html
- https://www.heise.de/security/meldung/TLS-1-3-doch-noch-nicht-jetzt-3780077.html (german on the delay of TLS 1.3)
- https://www.bsi.bund.de/DE/Presse/Pressemitteilungen/Presse2013/BSI_veroeffentlicht_Mindeststandard_fuer_verschluesselte_Internetverbindungen_08102013.html (german federal guideline on the deprecation of SSL & TLS 1.0 / 1.1)
- https://www.bsi.bund.de/SharedDocs/Downloads/DE/BSI/Mindeststandards/Mindeststandard_BSI_TLS_1_2_Version_1_0.pdf?__blob=publicationFile (german federal guideline on the deprecation of SSL & TLS 1.0 / 1.1)
- https://www.bsi.bund.de/SharedDocs/Downloads/DE/BSI/Publikationen/TechnischeRichtlinien/TR02102/BSI-TR-02102-2.pdf?__blob=publicationFile (german federal guideline on the deprecation of SSL & TLS 1.0 / 1.1)
- https://www.bsi.bund.de/SharedDocs/Downloads/DE/BSI/Mindeststandards/Migrationsleitfaden_Mindeststandard_BSI_TLS_1_2_Version_1_2.pdf?__blob=publicationFile&v=4 (german federal guideline on the deprecation of SSL & TLS 1.0 / 1.1)
- https://www.fastly.com/blog/phase-two-our-tls-10-and-11-deprecation-plan
- https://www.youtube.com/watch?v=WH5q8dNmAp8
- https://mitm.watch/
- On TLS certs being capped at two years
- https://0.me.uk/ev-phishing/
- https://stripe.ian.sh/
- https://security.stackexchange.com/questions/177182/is-there-a-list-of-old-browsers-that-only-support-tls-1-0/177323#177323
- https://crt.sh
- https://www.ct-observatory.org
- https://blog.mozilla.org/security/2015/04/30/deprecating-non-secure-http/
- https://blog.mozilla.org/security/2018/01/15/secure-contexts-everywhere/
- https://arkadiyt.com/2018/02/04/quantifying-untrusted-symantec-certificates/
- https://sslmate.com/caa/
- https://www.eff.org/deeplinks/2017/12/tipping-scales-https
- https://csrhelp.peculiarventures.com/
- https://security.stackexchange.com/questions/50878/ecdsa-vs-ecdh-vs-ed25519-vs-curve25519
- openssl/openssl#309
- https://caddy.community/t/how-to-enable-ssl-session-resumption/1886
- https://gist.github.com/roycewilliams/1710ade469c05eb0b090d268470aa741
- https://letsencrypt.org/docs/caa/
- https://blog.pki.dfn.de/2017/09/caa-rrs-reihenfolge-im-dns/
- https://www.bsi.bund.de/SharedDocs/Downloads/DE/BSI/Publikationen/TechnischeRichtlinien/TR02102/BSI-TR-02102-2.pdf?__blob=publicationFile&v=6
- https://www.enisa.europa.eu/activities/identity-and-trust/library/deliverables/study-on-cryptographic-protocols/at_download/fullReport
- https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-52r1.pdf
- https://www.datenschutzbeauftragter-info.de/bussgeld-fuer-kontaktformulare-ohne-verschluesselung/
- https://gdpr-info.eu/art-32-gdpr/
- https://www.gesetze-im-internet.de/tmg/__13.html
- https://www.thesslstore.com/blog/secure-contexts-features-chrome/
- http://permission.site/
- https://wiki.crashtest-security.com/display/KB/Prevent+SSL+CRIME
- https://raymii.org/s/tutorials/Strong_SSL_Security_On_nginx.html#SSL_Compression_(CRIME_attack)
- https://www.canada.ca/en/treasury-board-secretariat/services/information-technology/policy-implementation-notices/implementing-https-secure-web-connections-itpin.html
- https://gist.github.com/Timi7007/b5e12ab1aa68f42d0d7136834fd49a02
- https://www.security-insider.de/tls-13-viel-heisse-luft-oder-ein-grosser-wurf-a-713206/
- https://www.sjoerdlangkemper.nl/2016/11/07/current-state-of-breach-attack/
- https://doc.owncloud.org/server/10.0/admin_manual/installation/nginx_configuration.html
- https://poweruphosting.com/blog/secure-nginx-server/
- https://nulab-inc.com/blog/nulab/securing-nginx/
- https://github.com/nulab/nginx-length-hiding-filter-module
- https://www.owasp.org/index.php/Testing_for_Weak_SSL/TLS_Ciphers,_Insufficient_Transport_Layer_Protection_(OTG-CRYPST-001)
- https://www.soeren-hentzschel.at/firefox/firefox-60-automatisches-https-upgrade-fuer-http-ressourcen/
- DNS over HTTPS
- https://www.mnot.net/blog/2016/04/22/ideal-http
- https://support.apple.com/en-us/HT205280
- https://blog.cloudflare.com/rfc-8446-aka-tls-1-3/
- https://tls.ulfheim.net/
- https://www.ietf.org/mail-archive/web/tls/current/msg27066.html
- https://ssl.hakase.io/
- https://www.theregister.co.uk/2018/10/16/browser_tls_killed/
- https://www.eff.org/deeplinks/2019/02/ets-isnt-tls-and-you-shouldnt-use-it
- https://www.heise.de/security/meldung/Verschluesselung-Neue-TLS-Empfehlungen-vom-BSI-4408864.html (new german federal standard for TLS (including 1.3) usage)
You should definitely subscribe to the "Bulletproof TLS Newsletter"!
Also have a look at the alternative webserver Caddy.