WPAD is the Windows Proxy Auto Discovery service, used since Windows 95, IIRC, to automatically discover network configurations. Since Windows 10 Microsoft decided for some reason that users shall NOT be allowed to disable this (mostly) useless and problematic service.
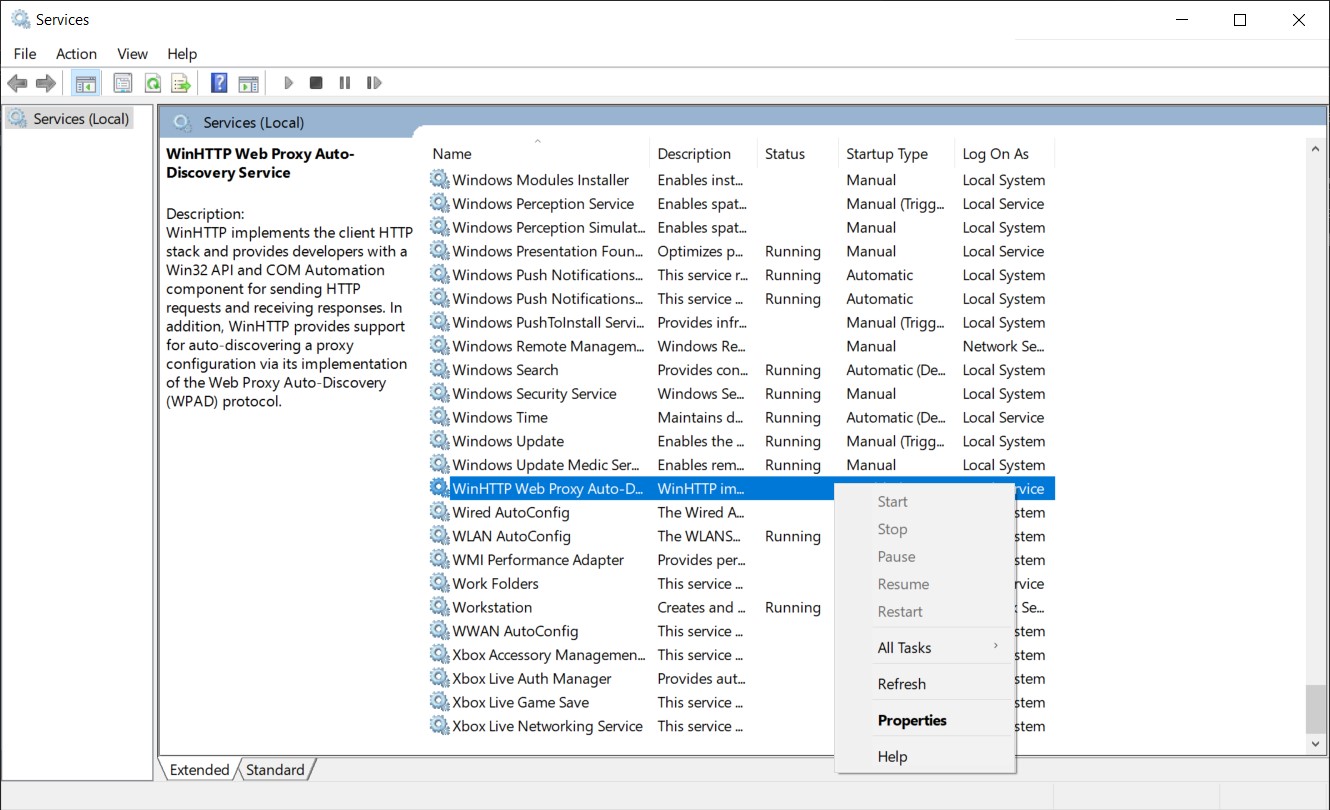
Problem is: on my laptop this feature used up to 20% of the CPU while doing nothing at all due to some bug I don't want to dig into. The best part is that it often triggered after disconnection from a wireless network. Discovering proxies makes lot of sense once you are NOT connected to any network, huh? Also, there were multiple vulnerabilities related to this service and cute tools such as Responder leverage on it.
The service can still be disabled writing in the registry, but it will be randomly re-enabled by windows after upda
