Daryl Tucker
Uses chunks of data. Fills extra room in each chunk with padding.
-
Data Encryption Standard (DES)
- IMB developed in 1970's
- Published in 1977
- Vulnerable to attacks due to small key size (56b)
- DEPRECATED => triple-DES
-
Advanced Encryption Standard (AES)
- Published in 2001
- Uses Rijndael Cipher
Encrypts each character or byte in succession.
- RC4
- RSA 'Trade Secret' until September, 1994
- Fast and Simple
- Allows attacker to 'distinguish' encrypted data.
- Causing issues with HTTPS/SSL
Allows authentication of source of data
- RSA
- DSA
Gives a determined-length identifier for a series of bytes.
-
MD5 / SHA-1
- DEPRECATED
- Collisons every 2^64
- Replaced by SHA-2
-
SHA-2 / SHA-3
- Variable bits: 224, 256, 384, 512
- Designed to be used in parallel/contingency
- SHA-3 Uses Sponge Function
$ sha256("Frank").hexdigest()'db605e8f71913d1f3966ad908d78b8a8084f5047122037b2b91a7192b598a9ad'$ sha256("Frank White").hexdigest()'112eed9bd22287808323f9ed7760e566b78798d57cfb834d6a570774c9e1c77e'
Cryptographic hash that allows validation with secret key.
- Symmetric
- The same key is used for encryption and decryption
- Users must all have the same key
- Problems with Secure Channel/MitM
- Asymmetric (1976)
- 1970 James H. Ellis of Government Communications Headquarters, Britain
- 1973 Clifford Cocks of GCHQ
- 1974 Malcom J. Williamson of GCHQ (Diffie-Hellman Clone)
- 1976 Diffie-Hellman
- One Trip
- ElGamal and DSA
- RSA
- TLS => SSL
- GPG/PGP
- Bitcoin (donate: 17Hwm5tuH7rCMf8Ukc2U7RUvxN22WWPur5)
- GPG/PGP
- Certificate Authorities
- Chicken and Egg
- Secure Channel
- Man in the Middle (MitM)
90% of 16,00+ hashed passcodes cracked
"Our goal is to find the most plains in the least amount of time, so we want to find as much low-hanging fruit as possible first."
- 11% 1234
- 6% 1111
- 2% 0000
27% of all PINs cracked using only 20 combinations
- WPA2 with AES
- Password Generation/Storage
- Browser Security
- Trusting your LAN
- Mobile Devices
- Using GPG
- Physical Security
- Deprecation of MD5 and SHA-1
- Specific usage of SHA-3
- Padding (WWII: The World Wonders)
- N+(0-INF)
- HTTP Authentication Protocol
- Uses salts!
- Oauth 2
- Assumes a secure channel (Use HTTPS!)
- Signed/Authenticated
- Tokens are no longer completely randomized
- [Cryptographic] Hashing vs Encrypting
- Cryptanalysis
- Cryptography vs Cryptology
- Hacking vs Cracking
- Storing Passwords
- Misc Learnings and Best Practices
- Integer Factorization
- Discrete Logarithm
- Elliptic Curve
- ECDSA
- Time-Consuming
- Smaller Ciphertext
- NSA Influence [1] [2]
- Please use Curve25519
- Man in the Middle (MitM)
- CA/Arbitrator
- PKI Providers
- Offline/Other secure channel
- Brute Force
- Arbitrary/Random Pausing
- Limiting requests over a timeframe
- Whitelists
- Blacklists
- Rainbow Tables
- Salts
- Chosen-Plaintext
- Collect many ciphertexts
- Gardening
- DES (Vulnerable)
- AES (Secure)
- Side Channel
- DANGER, DANGER
- System/Physical Information
- Sound, Electromagnetism
- Differential Fault Analysis
- Remanent Data
- Covert Channel
- "Hacker's API"
- XSL
- AES (Vulnerable, but not exactly)
- Key Recovery
- Determine entire key vs breaking individual ciphertexts
- AES-128 2^126.1
- AES-192 2^189.7
- AES-256 2^254.4
- Distinguishing
- Random vs Real Data

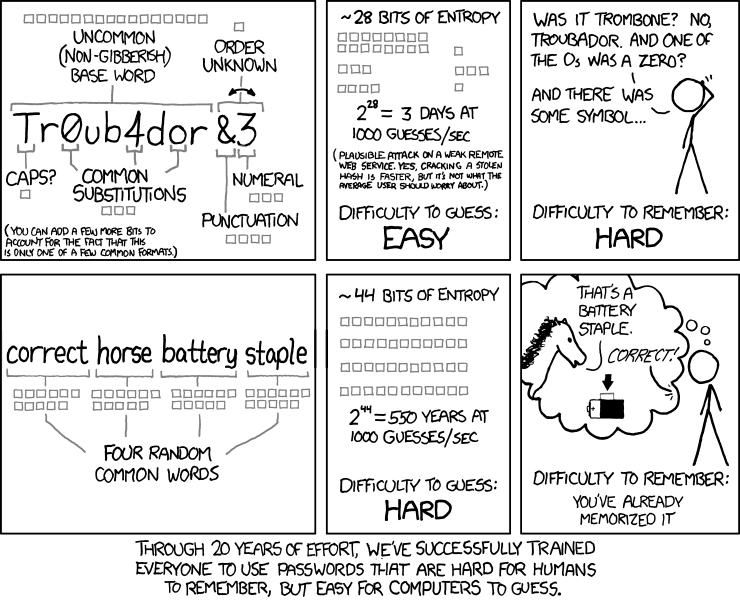
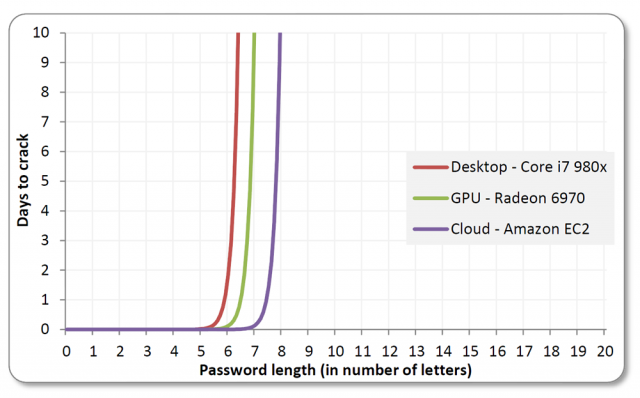


This has been made publicly available to assist people who wish to learn more about cryptography usage and as an opportunity for people to make constructive feedback, if they so choose.