127.0.0.1 is the loopback Internet protocol (IP) address also referred to as the localhost. The address is used to establish an IP connection to the same machine or computer being used by the end-user.
0.0.0.0 is a special IP which is "no particular address" (invalid/unknown/not-applicable).
0.0.0.0/0 : all IPs
MyAWSAccount
- VPC1
10.0.0.0/16(256*256 IPs)- subnet-1 (AZ1):
10.0.0.0/24(256 IPs)- ec2-1
- securityGroup-A
- securityGroup-B
- ec2-2
- securityGroup-A
- ec2-N
- securityGroup-B
- ec2-1
- subnet-2(AZ2)
10.0.1.0/24 - subnet-200
10.0.200.0/24
- subnet-1 (AZ1):
- VPC2
- ...
- VPC5
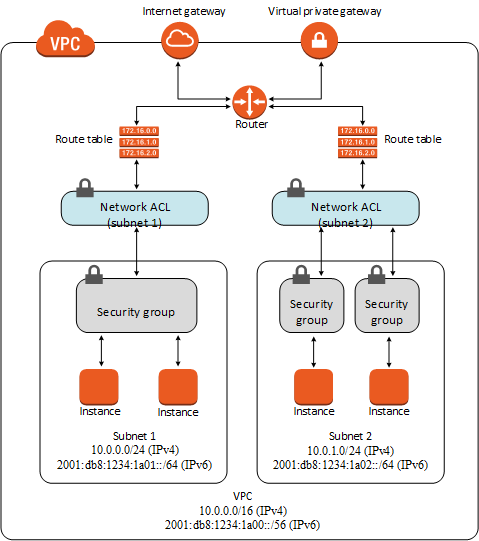
- Security groups — Act as a firewall for associated Amazon EC2 instances, controlling both inbound and outbound traffic at the instance level
- Network access control lists (ACLs) — Act as a firewall for associated subnets, controlling both inbound and outbound traffic at the subnet level
- Flow logs — Capture information about the IP traffic going to and from network interfaces in your VPC
Instance : SecurityGroup = * : 1..*
Amazon security groups and network ACLs don't filter traffic to or from link-local addresses (169.254.0.0/16) or AWS-reserved IPv4 addresses—these are the first four IPv4 addresses of the subnet (including the Amazon DNS server address for the VPC). You can implement additional firewall solutions in your instances to block network communication with link-local addresses.
The client that initiates the request chooses the ephemeral port range. The range varies depending on the client's operating system.
- Many Linux kernels (including the Amazon Linux kernel) use ports 32768-61000.
- Requests originating from Elastic Load Balancing use ports 1024-65535.
- Windows Server 2003 use ports 1025-5000
- Windows Server 2008 and later versions use ports 49152-65535
- A NAT gateway uses ports 1024-65535
For example, if a request comes into a web server in your VPC from a Windows XP client on the Internet, your network ACL must have an outbound rule to enable traffic destined for ports 1025-5000.
If an instance in your VPC is the client initiating a request, your network ACL must have an inbound rule to enable traffic destined for the ephemeral ports specific to the type of instance (Amazon Linux, Windows Server 2008, and so on).
In practice, to cover the different types of clients that might initiate traffic to public-facing instances in your VPC, you can open ephemeral ports 1024-65535. However, you can also add rules to the ACL to deny traffic on any malicious ports within that range. Ensure that you place the DENY rules earlier in the table than the ALLOW rules that open the wide range of ephemeral ports.
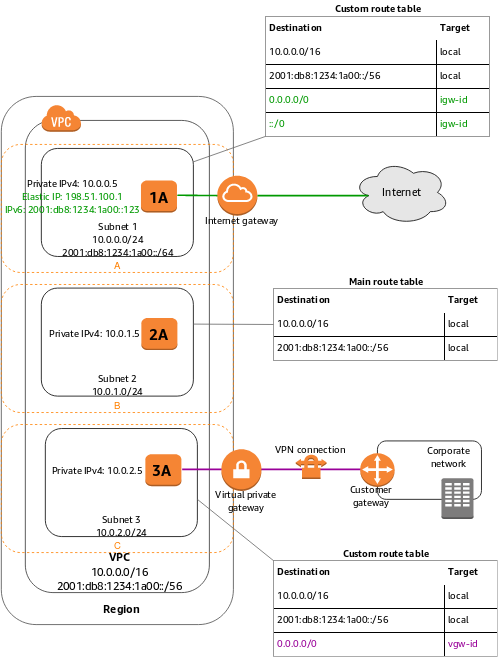
**Subnet : Route table = * : 1 ** A subnet must and can only be associated with a route table at a time.
How to make a subnet public? Add an entry to route table (traffic from any IP can go through internet gateway) :
- destination:
0.0.0.0/0 - target:
igw-id
Allow OUTBOUND only to internet? Use NAT (Network Adderss Translation)
Connect to corporate network? Attache a Virtual Private Gateway to VPC on AWS, and setup a customer gateway in your data center. A virtual private gateway is the VPN concentrator on the Amazon side of the VPN connection. A customer gateway is a physical device or software appliance on your side of the VPN connection
Acces AWS service inside AWS network rather than going though internet?
Use AWS PrivateLink(VPC Endpoints).
You don't need internet gateway, and can access serivce like DynamoDB/S3 inside AWS network.
See below for "IPv4 CIDR Block Association Restrictions"
https://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/VPC_Subnets.html, search by keyword.
VPC creation: the allowed CIDR block size is between a /28 netmask and /16 netmask.
Can attch a second CIDR block to a VPC
- 10.0.0.0/16 (when creating VPC)
- 10.1.0.0/16 (second, allowed CIDR block size /28 to /16)
Subnet: the allowed CIDR block size is between a /28 netmask and /16 netmask.
Recommended VPC CIDR block when creating a VPC When you create a VPC, we recommend that you specify a CIDR block (of /16 or smaller) from the private IPv4 address ranges as specified in RFC 1918:
- 10.0.0.0 - 10.255.255.255 (10/8 prefix)
- 172.16.0.0 - 172.31.255.255 (172.16/12 prefix)
- 192.168.0.0 - 192.168.255.255 (192.168/16 prefix)
A subnet must reside within a single Availability Zone.
VPC IPs are shared cross AZs
Subnet: first four IP addresses and the last IP address are not available for you to use, and cannot be assigned to an instance
- 10.0.0.0: Network address.
- 10.0.0.1: Reserved by AWS for the VPC router.
- 10.0.0.2: Reserved by AWS. The IP address of the DNS server is always the base of the VPC network range plus two; however, we also reserve the base of each subnet range plus two. For VPCs with multiple CIDR blocks, the IP address of the DNS server is located in the primary CIDR. For more information, see Amazon DNS Server.
- 10.0.0.3: Reserved by AWS for future use.
- 10.0.0.255: Network broadcast address. We do not support broadcast in a VPC, therefore we reserve this address.
Public/Private/VPN-Only subnet
- If a subnet's traffic is routed to an internet gateway, the subnet is known as a public subnet
- If a subnet doesn't have a route to the internet gateway, the subnet is known as a private subnet
- If a subnet doesn't have a route to the internet gateway, but has its traffic routed to a virtual private gateway for a VPN connection, the subnet is known as a VPN-only subnet
VPC policy https://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/VPC_IAM.html?shortFooter=true
- VPC and Subnets
- VPC per region: 5
- Subnets per VPC: 200
- IPv4 CIDR blocks per VPC: 5
- IPv6 CIDR blocks per VPC: 1
- NetWork ACL
- ACLs per VPC: 200
- Rules per ACL: 20
- Network Interface per region: 350
- Route Tables
- Route tables per VPC: 200
- Routes per route table(non-propagated routes): 50
- BGP advertised routes per route table(propagated routes): 100
- Security Group
- Security Groups per VPC: 500
- Inbound/outbound rules per security group: 50
- Security groups per network interfaces: 5
- a