Category: Reverse
Can you find your way inside the vault?
Author : Elf#4541
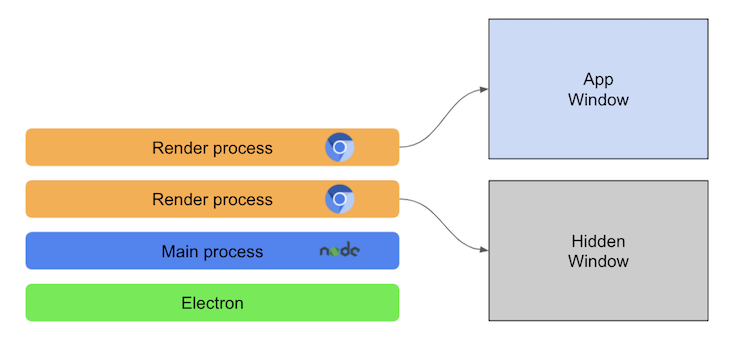
When we open the challenge folder, we instantly understand that it's an electron App, built with Electron Js. In other meaning, an instance of Chromium that render web pages (html, css, js...).
When we launch the app by opening protonic-vault.exe, located in the root of the challenge folder.
/protonic-vault/protonic-vault.exe. It asks us for a password that we don't know!
My first reaction was CTRL + SHIFT + C and F12 to try open the devTools and inspect it, keep in mind that it's Chromium instance, so we are inside a web browser.
But unfortunately in our case the devTools is disabled, it's a feature that can be enabled/disabled by the app dev's
mainWindow = new BrowserWindow({
webPreferences: {
devTools: false //true
}
});Even it was disabled, it still possible to inspect it using remote-debbugin but I don't think it will help us to get the password, debugging still interesting when the app make externals api calls.
C:\Desktop> "/protonic-vault/protonic-vault.exe" --remote-debugging-port=31337
Let's do cooler things 😎... The challenge category's is Reverse, so reading the source code could be enough Hope the code is not obfuscated...
Well, in /protonic-vault/ressources/ folder we have this particular file app.asar, what is it?
Asar file is an archive used to package source code for an application using Electron, an open source library used to build cross-platform programs.
So, let's extract it! 🚀
- First we need to have asar installed in our machine
npm install -g asar - Then move to
cd ./ressources/ - Extract
app.asarin this distination folder./protonic-vault-extrcted
npx asar extract app.asar ./protonic-vault-extrcted
Once extracting is completed, we could open the sources files with VS Code editor for example and start installing the project dependencies.
ressources/protonic-vault-extrcted> npm i
Then all what we need to do is, to take a look inside the project files. we can notice that the password auth is verified by renderer.js.
//...
if (password === truePassword) {
resultDiv.innerHTML = `Welcome, dear master!<br/>Flag: ${await window.electronAPI.getFlag()}`
resultDiv.className = "notification is-success"
}
else {
resultDiv.textContent = `You're wrong!!`
resultDiv.className = "notification is-danger"
}
//...As you see, we have many possibilities to bypass the auth and get the flag, let's use the cheesy one 😛...
if (password === truePassword) {
}
else {
// resultDiv.textContent = `You're wrong!! `
resultDiv.textContent = `You're wrong!! but here is the Flag: ${await window.electronAPI.getFlag()}`
resultDiv.className = "notification is-danger"
}Save your changes and launch the app npm start
Send anything comes in your mind and Submit to get back the flag 🚀
🚩 Flag: RM{V8_by3c0d3_1s_n0t_3n0ugh}