extract-and-test is a script which tests the .dll(s) in a nuget package to verify they are strong-name signed using the sn tool.
First, install scoop by running Invoke-Expression (New-Object System.Net.WebClient).DownloadString('https://get.scoop.sh'). Then, in a new window, install the remainding requirements for this script by running ./instal.ps1 in a new elevated instance of powershell.
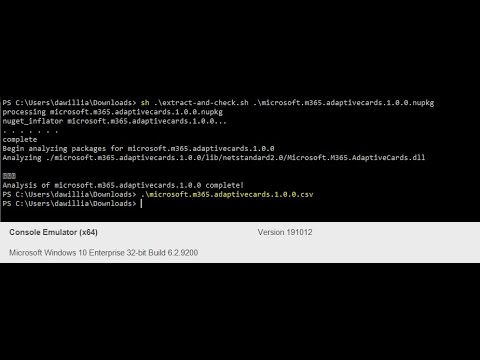
sudo apt-get install monoRun sh .\extract-and-check.sh <\path to your .nuget package>. This will produce a csv file containing details on the .dll(s) contained in the given package.
If your authenitcode cert is not installed on your local machine, chktrust will throw the following error:
ERROR! Microsoft.Bond.dll signature can't be traced back to a trusted root! This is to be expected, and is a good sign, as your .dll does have an authenticode signature.