This article is for my friend who is gonna taking the onsite interview next week. He got some incident response background, so part of the details bellow would be omitted (((( I guess he know that
And, if you’re full-stack web engineer or junior incident responser, the article would give you the idea for the preparation.
I haven't got the offer while writing this article, This is never being as a criteria or a guidelines or a standard
I have never learn anything about incident response before the interview, the ideas are the thing I read in these few days. So, the answers below might not be the best answer, just kinda the example of train of thought.
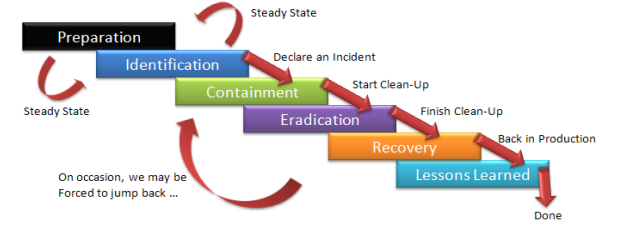
- Know the incident response process ( Very Important )
- The basic processes of the incident response (Indeed are following SANS)
- Understand how to containment the hacking and malware
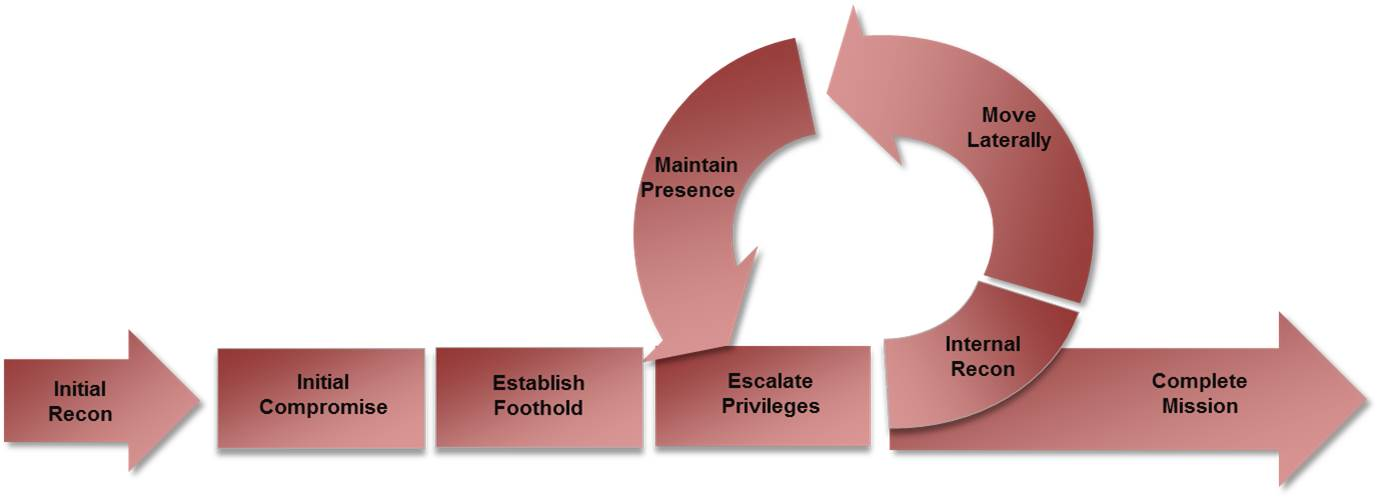
- Understand the mandiant attack lifecycle & combine with the incident response procss also the containment
- Snort Rule
- They would not ask you to write rule code but need to understand what is the rule for.
- Linux Log
- ((( Indeed is still using data centres, so the linux log was mentioned serveral times in the interview )))
- Log of the actions
- current processes usages
- current memory usages
- how to detect the malware
- SSH Access & Apache Log
- Understand does the server was accessed
- API Log
- Understand if the API was hacked by directory traversal & if the hacker get data & what's their target & next step
- Combine with the mandiant attack lifecycle
- Phishing Email
- Determine if the email is a phishing email
- The consequence response of the situation that the users download the malware & executed the files
- OWASP Top 10
- SQL Injection
- XSS
- PHP & Apache
- eval
- local include
- remote include
I am a full-stack engineer who is looking forward to getting into the security area, so I applied the Incident Response Position.
In this article, I will focus on who to prepare the on-site interview and what kind of questions are the interviewers cared about.
Also, I will highlight the points you might have to spend time on, if you're a software engineer.
Do not do the interview in an early morning
First of all, congradulations to the onsite interview cycle.
Cuase the covid-19 and the incident response team members are almost in the states.
The onsite interivew will be sperate into 6 sections ( Phishing / Alert Analysis and Detection / Log Analysis / Major IR / team culture / manager )
No matter which topics, all of the questions are log reading -> identifying -> containment.
Whatever the sections, the questions are all in these logic, but using different logs.
Ex:
- phishing -> mail log
- alert -> network log
- log -> linux log & API log
- Magor IR -> Apache Log & API Log or etc.
The team are not expecting the candidate doesn't have any incident response knowledge,
but almost all of the question will rotate back to the incident response process...
A tip for answering the question is that forget all of the modern structure thing Ex WAF, RDS, LB, Kubernate, Docker, Snapshot, Datadog, Cloud Watch, Distributing Couting, Seperated Front/Backend, and etc....
Event forget those meaningful IP address such as 1.1.1.1 or 8.8.8.8 Those are just example IP
But don't forget the monolithic server with Apache which rendering the front in server and the framework such as CodeIgnither, CakePHP, or Dijango(the old version)
Keep the structure in your mind as simple as possible, it would help you to answer.
The team culture is quite a casual talk. The interviewrs are the security team members in Tokyo.
And the security team in Tokyo is quite a small team, so you will work with them quite a lot. (They said that 😂)
About the conversation to the manger ... TBH... I don't really remember what we speak...
Cuase the interview before the manager was until 1 am ... and the manage meeting was 8 am ...😂
So here is a tip Never have the interview in an early morning. Seriously. 😂
Understand the mandiant attack lifecycle & combine the incident response procss that knowing how to dealt with the situation and contain the situation
下面這張圖是 Incident Response 的基礎 Process
考試時你要清楚的知道你現在在什麼階段,該做什麼事情,且下一步是什麼動作。
例如 identifying 時,清楚知道這個是什麼樣的攻擊,Hackers 可能拿到了什麼的東西,Hackers 有沒有成功
雖然他們一直說你如果不知道Incident Response 沒關係
但其實沒有準備 Incident Response 根本沒辦法回答他們的問題
這個一個攻擊的思維模型
當一個 Hacker 打破了第一個環境,這個 LifeCycle 會提供一個思路,知道接下來要怎麼做,然後完成你的 Target
基本上就是要你想辦法維持你的 Access 和 不斷先辦法提升權限
在回答問題的時候,你總是好去思考,這個攻擊到了什麼地步,他有沒有提升權限了,怎麼查他有沒有提升權限
例如:當你看到了一個 `../../../../../../passwd 的文件被 Access 了之後, 你要能想到,Hacker 能知道【誰】擁有了【什麼權限】, 或其實 Hacker 什麼都不能幹嘛。
((( 因為 Linux 已經把 Password 移到 etc/shadow 了...所以雖然是 passwd 但其實沒有 passwd,如果不知道的話,就只能猜那裡面有 Password 了啊!誰叫他叫那個名字!!)))
進而去看有沒有辦法找到什麼密碼或是什麼途徑可以去的權限
從一個 普通權限 -> 管理層權限 這就是個權限提升
如果 Hacker 得到了權限提升之後,Incident Response 的 Process 就不一樣了
怎麼去應對怎麼去 Contain 就是實際在問考官,他會給你更詳細的步驟
其實不只 Major IR 會問到這一塊,其他 Section 雖然表面是說讓你看 Log,但其實這個模型會持續出現
所以下面我們再來看遇到每個狀況怎麼回答吧
其實我自己覺得被問到這個有點過分
如果只是開發 Software 的話基本上不會有機會摸到這個
而且我都跟他說我用的是 Mac,直接去 Activity Monitor 的看有沒有奇怪的 Process,還是被追問 Linux 的指令 ((( ... 我都直接看 CloudWatch 的... murmur 🤣
所以還是乖乖準備一下吧
提供了最基礎的思路,例如去查是不是有多出來的用戶,或是有沒有啟動一些神奇的程式
考官可能問,只有 /var/log 那你該怎麼尋找這個有麼有被 Hacked
這個網站
是說 Linux 的 /var/log 分別是記錄什麼,再利用基礎思路分析 (例如去查是不是有多出來的用戶,或是有沒有啟動一些神奇的程式)
例如 /var/log/cups 找什麼東西被執行過了,或是 /var/log/utmp 找有沒有奇怪的Access
題外話,不要想用 Python 去分析,因為考官沒有耐心聽
記一下基礎的 Linux 指令 find、grep 、egrep、awk、sed
他應該不會考到 find 後面的 -- 應該要填什麼
知道要找什麼比較重要
這邊提供更詳細的排查方案
另外當你的服務器被入侵時,你不能直接關閉服務器,只能在 Sever 繼續運行的狀態下排查和對應
你該怎麼辦?
FullStack 應該很直覺就.. 我再開一個 ECS 的 Container 改個 Terraform 的 Param 然後重新 Deploy Code 就好了啊
這個絕對不是他們想要的答案.........
Indeed 大部分的 Service 還是在 Data Center (唯一一個我記得我問了 Manager 什麼的地方 😌 )
不太可能直接跑去 Data Center 做這種事( 也不像不像東京的 Data Center 從赤坂搭15分鐘的車就會到 )
基本上還是剛剛的思路例如:
什麼 IP 入侵了我 -> 什麼 Port / 是否能關掉 -> 【是否權限被提升了】 或 【有新管道】-> 移除管道
The question will looks like the logs in this video https://youtu.be/ZmVOGVbnYvo or https://youtu.be/UVpu78B1pWQ
In this section, the interviewer will give you a detection rule which looks like the following snort rule
alert tcp $EXTERNAL_NET any -> $HOME_NET $HTTP_PORTS (
msg:"SQL use of concat function with select - likely SQL injection";
flow:to_server,established;
http_uri; content:"SELECT ",nocase; content:"CONCAT|28|",within 100,nocase;
metadata:policy max-detect-ips drop,policy security-ips drop; service:http;
reference:url,ferruh.mavituna.com/sql-injection-cheatsheet-oku/;
classtype:web-application-attack; sid:24172; rev:2;
)
This is not the interview question, just an example from Snort Example
And