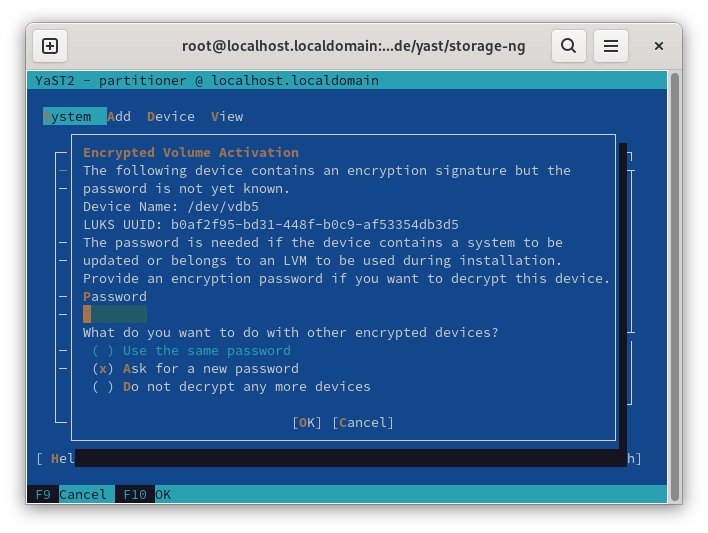
When there are a lot of encrypted devices, the user is asked to provide the password for every LUKS. This can be very annoying in some typical cases. For example, if the user only wants to activate one device, or if all devices use the same password.
Possible use cases
- Accept password for the current luks
- Accept password for the current luks and try to activate next lukes with the same password.
- Cancel activation of the current luks
- Cancel activation of the current and next lukses
The popup to ask for the password should provide options to cover such use cases.
This is a simplified version that only allows to skip the rest of encrypted devices, but it does not offer to reuse the password.
Note: This requires support from libstorage-ng to provide the size and label (luks2) of the device.
Actually this is an alternative/complementary solution. The idea is to preselect what devices to probe. With this, a user could indicate only the device (or devices) for installing/upgrading without bothering with stuff from other devices. As result, the probed devicegraph would only contain the selected devices.
The device selection could offer different filters, for example, by device name, by technology (RAID, multipath, network device, etc).
How to provide this feature? Due to this is a special feature only needed for certain scenarios, it makes sense to activate it by means of a booting parameter like YAST_PRESELECT_DEVICES=1. The Expert Menu could also provide a way to activate it. Once the option is activated, the user would be asked before probing the system. We could use the light probing to inform the user about the available devices. After selecting with devices to probe, that information has to be passed to libstorage-ng in order to limit the probing action.
Caveats:
- The probing with limited devices could report more issues than the regular probing, for example, because incomplete VGs, RAIDs, etc.
- During the upgrade, some fstab devices could not be found if they are not pre-selected.
- During installation, it would not be possible to import some mount points.
This is the original Martin's idea. It consists on offering a boot parameter to indicate the LUKSes we want to open. The rest of encrypted devices will not be decrypted and the user will not be asked for a password. For example: YAST_OPEN_LUKS=/dev/sda2,/dev/sda3.





BTW the PBI is https://trello.com/c/MvkmdI10