This process will allow you to create a shortcut on your desktop that will enable automatic entry of your OTP code into FFXIV without having to open up the authenticator each time you log in.
It uses FFXIV QuickLauncher for doing its work.
Feel free to skip this section if you want to just get down to it.
This post was inspired after somewhat unsuccessfully trying to log in on launch weekend for Endwalker and constantly getting 2002 errors, quitting to desktop, and having to start all over again. Each time I'd do that, I'd have to enter my OTP.
...I got sick of entering the OTP.
The FFXIV QuickLauncher app is great because, when it's running it exposes a little HTTP server that you can send your OTP code to. This is great, but if our OTP is the SQEnix app for iOS or Android, we're still pretty restricted. The quicklauncher authors publish a guide on how to integrate this with some smart phone apps, but those apps aren't published via app stores (have to jailbreak your phone) AND they still require you to open them for each launch, only you don't have to type in the code anymore. While this is better, as a WoW player, I've been spoiled by Blizzard's auth method which puts a semi-permanent security token in place of your OTP on the computers you install battle.net on. You just click "Play".
Luckily, as of sometime in 2021, the dev team for 14 added support for Software Authenticators like Authy, Google Authenticator, etc. This means we can bring our own authenticator app. Since OTP is a very well known protocol, you can create the OTP with simple scripts. I grabbed a powershell script on the internet, and got to work.
This script basically gets us "Double click and play FFXIV".
- This script keeps your OTP "secret" on your computer, in plain text. Admittedly it's not the most secure method.
I am considering adding a PR to QuickLauncher in the future to build it right in which would be much more secure. - This exact feature was added to FFXIVQuickLauncher at one point, but did not make it in because the authors felt it was not secure enough and defetaed the point of having OTP at all. While I don't completely disagree with that, I also think the scope of having an FFXIV OTP secret compromised is a risk I'm willing to live with. See discussion here
- It also removes the "2nd factor" (an external smart phone) from being needed to log in. This means if a bad actor got access to your computer, they could get your access to your OTP secret and be able to generate OTP codes.
This approach will make the OTP available in 2 places:
- Your PC where you have FFXIV installed
- An external authenticator app like Authy (my personal preference) or Google Authenticator
DISCLAIMER: Use this as your own discretion. If you don't feel comfortable doing this, just stop and move on with life. This walkthrough comes with no guaranatee, waranty or anything. I am not responsible for anything you do to your own computer. Admittedly, this isn't for the technical novice. Read through the steps below, and if you're so inclined, review the source code of the powershell script. If you're uncomfortable, just close this window and move on with life.
I can tell you that:
- The OTP Secret never leaves your PC
- The script makes no external calls to third parties to do its work
- It only connects directly to the FFXIVQuickLauncher running locally on your computer
- If your password is compromised by a data leak or something, this does not put you in any worse of a position.
If you're already using OTP to log into FFXIV, you'll first need to remove your current authenticator. Head over to mog station.
One Time Password on Mog Station
Follow the instructions to remove your current authenticator.
- Install the FFXIVQuickLaucher - Follow the instructions on the github readme. Get it installed.
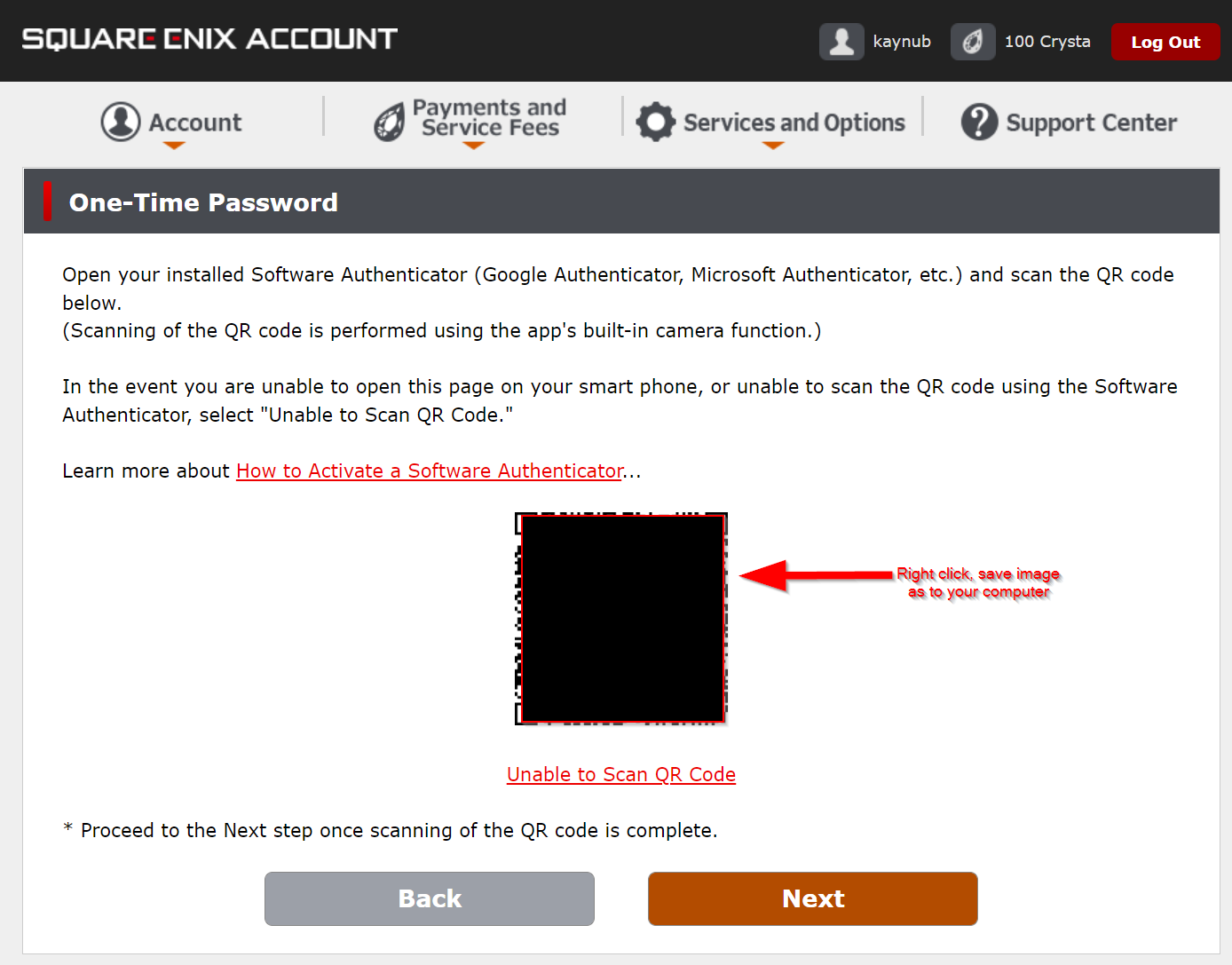
- Go to MogStation, log in, and go to the One Time Password page. Click on the "Software Authenticator" button at the bottom. Another button "Software Authenticator Registration" will appear -- click it.
- On this screen, a QR Code will appear. Right click the image and save it to somewhere on your PC, like your desktop.
Note: This QR Code contains your "Secret" which is used to generate those 6 digit OTP codes. Don't keep this file around, delete it when you're done and treat this as sensitive data.
- Now before we do anything else, lets get this into a legit authenticator app so you can still use it if something goes wrong. If all else fails, this will be your OTP app to use the official XIV launcher, or manual entry into the FFXIVQuickLauncher. Grab your phone, open Authy or Google Authenticator, and use your camera to scan the QR code and add this account to your app. If you need help, follow the official Square Enix help guidance Since you have the QR Code saved now, you can go ahead and complete the setup in Mog Station. Don't forget to save your emergency removal key somewhere safe as well.
- Now lets setupe FFXIVQuickLauncher. Open it and set the following options:
- Enter your username
- Enter your password
- Check "Log in Automatically"
- Check "Use One-Time Passwords"
- Click on the Cogwheel, and check the "Enable XL Authenticator app/OTP macro support"
Now use it to launch FFXIV just to test out that it's working. Enter the OTP from your authenticator app to make sure it's working. If you get into FFXIV and it can connect to the data center, you're good.
FFXIVQuickLauncher needs to actually launch FFXIV once with the "Log in Automatically" setting in order for the script to work correctly.
Note the file location where the .exe is on your hard drive, mine in my user folder at C:\Users\kensy\AppData\Local\XIVLauncher\XIVLauncher.exe. You can find this by right clicking the shortcut on your desktop and clicking "Properties".
- First we're going to need to extract the secret from that QR Code. Open a new browser tab to https://nimiq.github.io/qr-scanner/demo/ which will parse out the data for you. If you have another preferred tool to use for this, feel free to use it. Any QR Code Reader will do. Select the file you saved above (it should be called
download.png) and select it in the javascript app on this site. It will print out what looks like a weird URL, which contains the secret and other OTP specific settings for authenticator apps like Authy. The URL will look like this:
otpauth://totp/Square%20Enix%20ID:kaynub?secret=ABCDEFGHIJKLMNOPQRSTUVWXYZ&issuer=Square%20Enix%20ID&algorithm=SHA1&digits=6&period=30
^^^^^^^^^^^^^^^^^^^^^^^^^^
Copy the "Secret" value here, the random code in between secret= and &issuer -- you'll need it later. Keep this window up for the time being in case you need to come back to it.
Note: This method DOES NOT send your QR code to any server, it's kept locally in your browser
-
Grab the powershell script below. Click on "Raw" button in gist, and save it to your desktop or somewhere as "ffxiv.ps1". By default, it will save it as a
.txtfile, but just change the file name so it is a.ps1(powershell) file. It doesn't matter where you save it, but I'm going to assume you saved it to your user folder for the rest of this walkthrough. Just update the path accordingly if you want it elsewhere. -
Open the script in a text editor,
- Replace the
SECRET HEREon the first line with the value OTP Secret you copied above. - Update the file path below it to point at your FFXIVQuickLauncher .exe from step 1 (probably just replace
YOURUSERNAMEwith the name of your user directory inC:\Users)
- Windows is configured by default to protect users from running unsigned powershell code, including the script below. You will need to turn off this protection in order to run the powershell script. This does put your computer at greater risk of inadvertently running malicious code, but if you're comfortable doing this in the first place, this comes with the territory. Run the following commands:
Set-ExecutionPolicy -ExecutionPolicy Unrestricted -Scope CurrentUser
Unblock-File C:\Users\YOURUSERNAME\ffxiv.ps1 # replace this path with wherever you saved the script- Create a shortcut to run the script. On your desktop, right click somewhere and click "New > Shortcut".
- Location of item:
powershell.exe -f C:\users\YOURUSERNAME\ff14.ps1(Replace the path with the path to where you saved the script) - Click Next, and call it FFXIV-AutoOTP or something instead of powershell.exe, you can always rename it later.
- Click Done
Now you should be good to go! Double click the shortcut on your desktop and it should launch FFXIV in about 5 seconds. A powershell window will open and close after it's done giving the OTP to FFXIVQuickLauncher. You will see a prompt for the OTP but it will go away once the script sends it to FFXIVQuickLauncher.
Hit me up on twitter if you have any questions: https://twitter.com/kensykora
Thank you to jonfriesen for providing the Powershell code for creating OTPs




Haven't checked up on this in a while! Glad some of you are finding use of this.
@Ulinsky @kamiben These are great suggestions
@antonlabz glad you figured it out -- yeah especially when I first startup my computer, occasionally the xivlauncher webserver doesn't start up in time. Feel free to adjust that timeout to be much longer to suit your needs
@TheOddball Great suggestion. I also use onepassword but I have been avoiding adding my MFA's there in the event of a lastpass style breach. But that's awesome that it works for you