Quick and simple role-based Azure Active Directory authentication and authorization using JWT tokens
- Navigate to Azure portal and create app registration:
QuickAndSimpleApiAuthAppwithSingle tenant - Record the data of newly
QuickAndSimpleApiAuthAppcreated app registration:- Client ID:
6f33c1bb-4290-40ed-a026-8fb4bb8b326e - Tenant ID:
b40a105f-0643-4922-8e60-10fc1abf9c4b
- Client ID:
Set application ID URIunderExpose APIblade- Create scope
QuickAndSimpleApiAuth.AllforAdmins and usersunderExpose APIblade - Create roles under
App rolesblade:ManagerAdminReader
PS: Allowed member types are Users/Groups
Use .NET 6.0 Target platform
Microsoft.AspNetCore.Authentication.JwtBearerMicrosoft.AspNetCore.Authentication.OpenIdConnectMicrosoft.Identity.WebMicrosoft.Identity.Web.UI
var configurationSection = builder.Configuration.GetSection("AzureAd");
builder.Services
.AddAuthentication(JwtBearerDefaults.AuthenticationScheme)
.AddMicrosoftIdentityWebApi(configurationSection);app.UseAuthentication();Where Client ID, Tenant ID and Scopes are from Step 1
"AzureAd": {
"Instance": "https://login.microsoftonline.com/",
"TenantId": "b40a105f-0643-4922-8e60-10fc1abf9c4b",
"ClientId": "6f33c1bb-4290-40ed-a026-8fb4bb8b326e",
"Scopes": "QuickAndSimpleApiAuth.All"
},- Controller
[ApiController]
[Route("[controller]")]
[RequiredScope(RequiredScopesConfigurationKey = "AzureAd:Scopes")]- HTTP action
[Authorize(Roles = "Manager")]
[HttpGet("GetWeatherManager")]- Update Windows Powershell as Administrator using:
Install-Module PSWindowsUpdate - Install Azure PowerShell
- Install as Powershell Administrator:
Install-Module AzureAD
- Connect to AD:
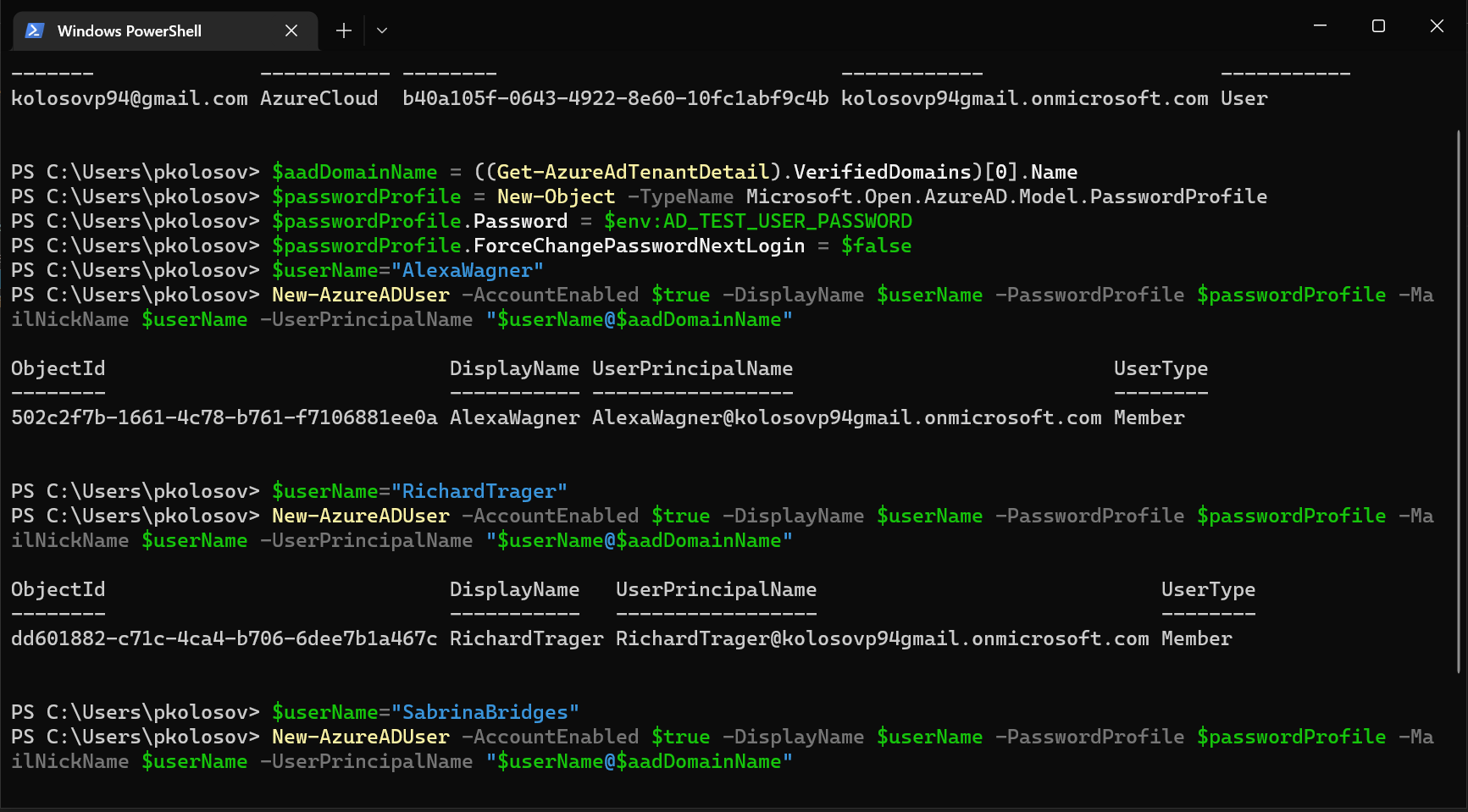
Connect-AzureAD -TenantId "b40a105f-0643-4922-8e60-10fc1abf9c4b" - Define domain variable:
$aadDomainName = ((Get-AzureAdTenantDetail).VerifiedDomains)[0].Name
- Create password profile:
$passwordProfile = New-Object -TypeName Microsoft.Open.AzureAD.Model.PasswordProfile$passwordProfile.Password = $env:AD_TEST_USER_PASSWORD$passwordProfile.ForceChangePasswordNextLogin = $false
- Define username variable:
$userName="AlexaWagner" - Create Alexa Wagner user:
New-AzureADUser -AccountEnabled $true -DisplayName $userName -PasswordProfile $passwordProfile -MailNickName $userName -UserPrincipalName "$userName@$aadDomainName" - Print new user principal name:
(Get-AzureADUser -Filter "MailNickName eq '$userName'").UserPrincipalName - User Principal Name (UPN):
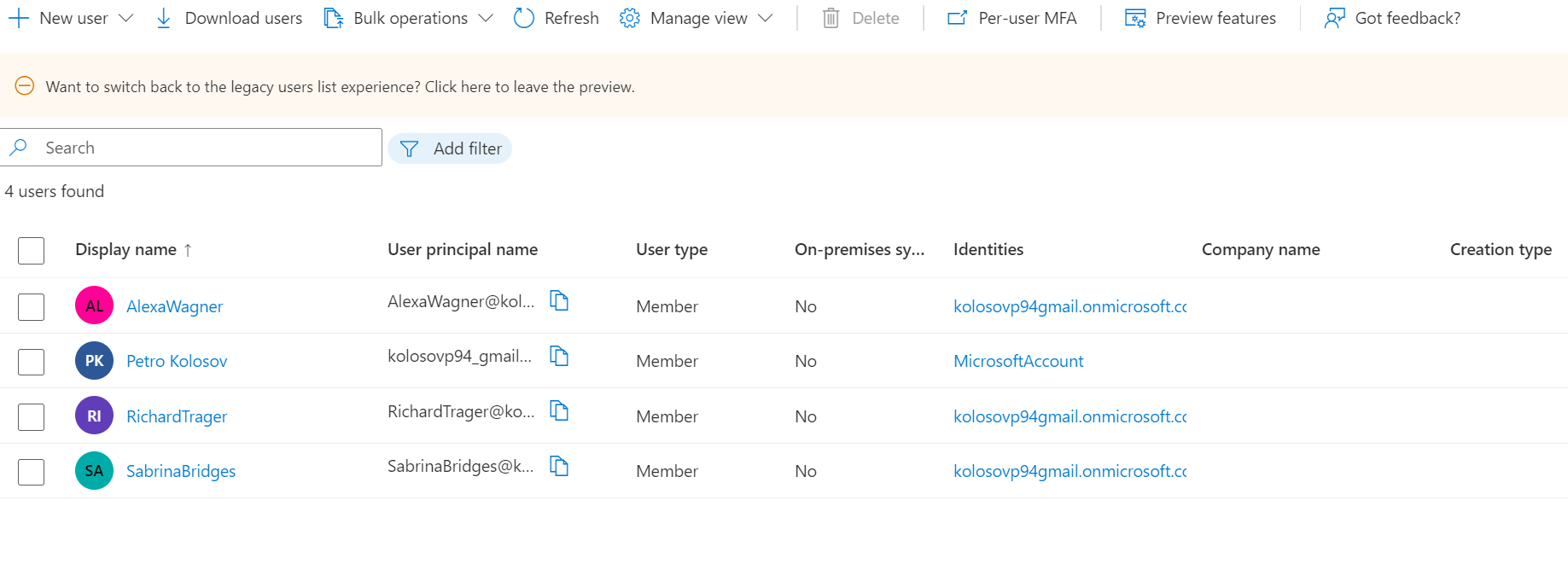
AlexaWagner@kolosovp94gmail.onmicrosoft.com
- Create password profile:
$passwordProfile = New-Object -TypeName Microsoft.Open.AzureAD.Model.PasswordProfile$passwordProfile.Password = $env:AD_TEST_USER_PASSWORD$passwordProfile.ForceChangePasswordNextLogin = $false
- Define username variable:
$userName="RichardTrager" - Create Richard Trager user:
New-AzureADUser -AccountEnabled $true -DisplayName $userName -PasswordProfile $passwordProfile -MailNickName $userName -UserPrincipalName "$userName@$aadDomainName" - Print new user principal name:
(Get-AzureADUser -Filter "MailNickName eq '$userName'").UserPrincipalName - User Principal Name (UPN):
RichardTrager@kolosovp94gmail.onmicrosoft.com
- Create password profile:
$passwordProfile = New-Object -TypeName Microsoft.Open.AzureAD.Model.PasswordProfile$passwordProfile.Password = $env:AD_TEST_USER_PASSWORD$passwordProfile.ForceChangePasswordNextLogin = $false
- Define username variable:
$userName="SabrinaBridges" - Create Sabrina Bridges user:
New-AzureADUser -AccountEnabled $true -DisplayName $userName -PasswordProfile $passwordProfile -MailNickName $userName -UserPrincipalName "$userName@$aadDomainName" - Print new user principal name:
(Get-AzureADUser -Filter "MailNickName eq '$userName'").UserPrincipalName - User Principal Name (UPN):
SabrinaBridges@kolosovp94gmail.onmicrosoft.com
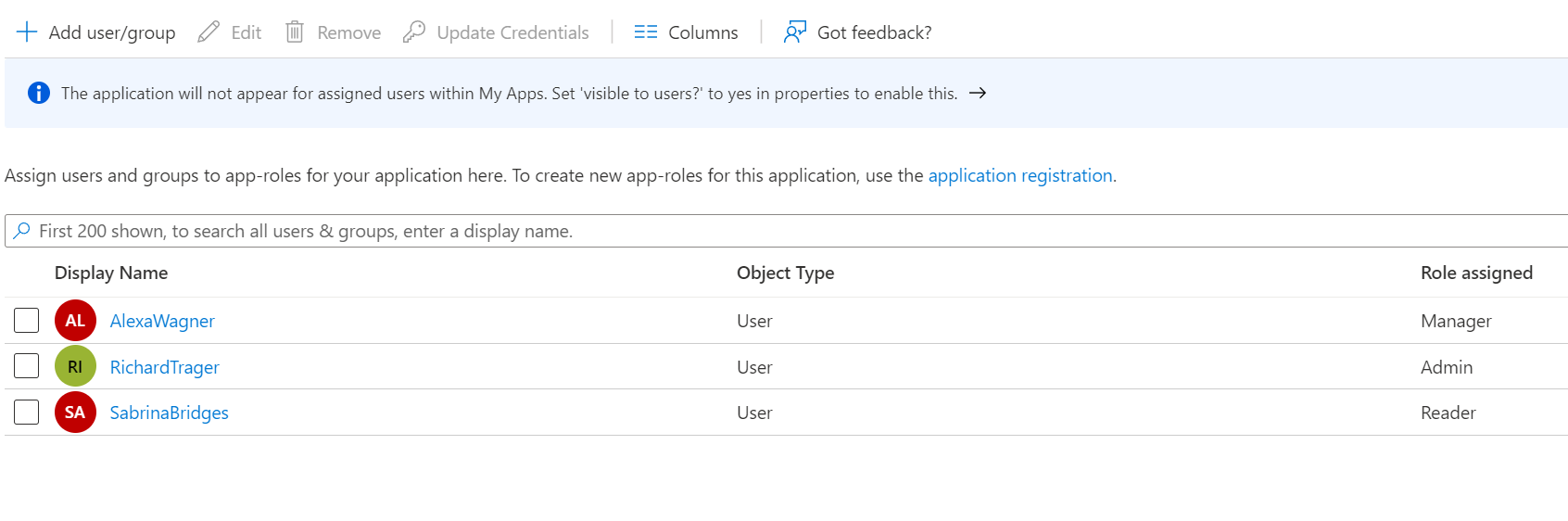
- Go to
Azure Portal -> Enterprise Applications -> QuickAndSimpleApiAuth -> 1. Assign users and groups - Assign roles to the test users:
- Manager:
AlexaWagner@kolosovp94gmail.onmicrosoft.com - Admin:
RichardTrager@kolosovp94gmail.onmicrosoft.com - Reader:
SabrinaBridges@kolosovp94gmail.onmicrosoft.com
- Manager:
- Review created role assignments
- Navigate to Azure portal and create app registration:
QuickAndSimpleApiAuthPostmanAppwithSingle tenant - Record the data of newly created
QuickAndSimpleApiAuthPostmanAppapp registration:- Client ID:
0efacdad-fe7d-48b3-9531-771e612d3b4e - Tenant ID:
b40a105f-0643-4922-8e60-10fc1abf9c4b
- Client ID:
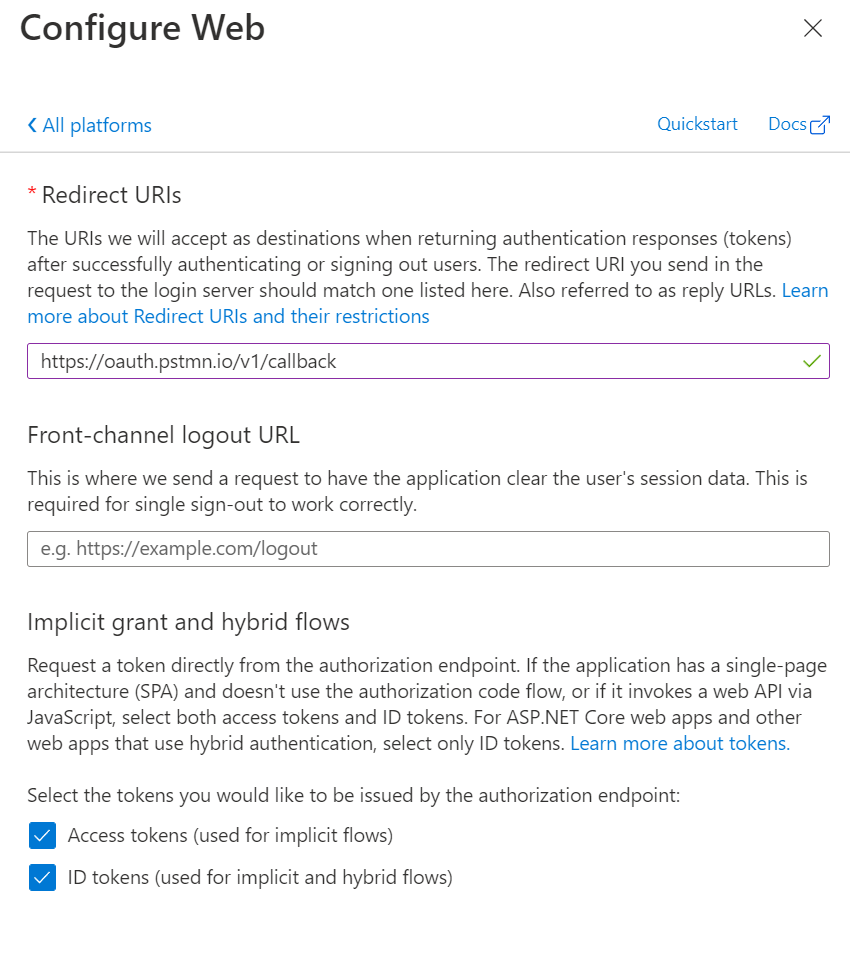
- In
AuthenticationbladeAdd a platformwith parameters
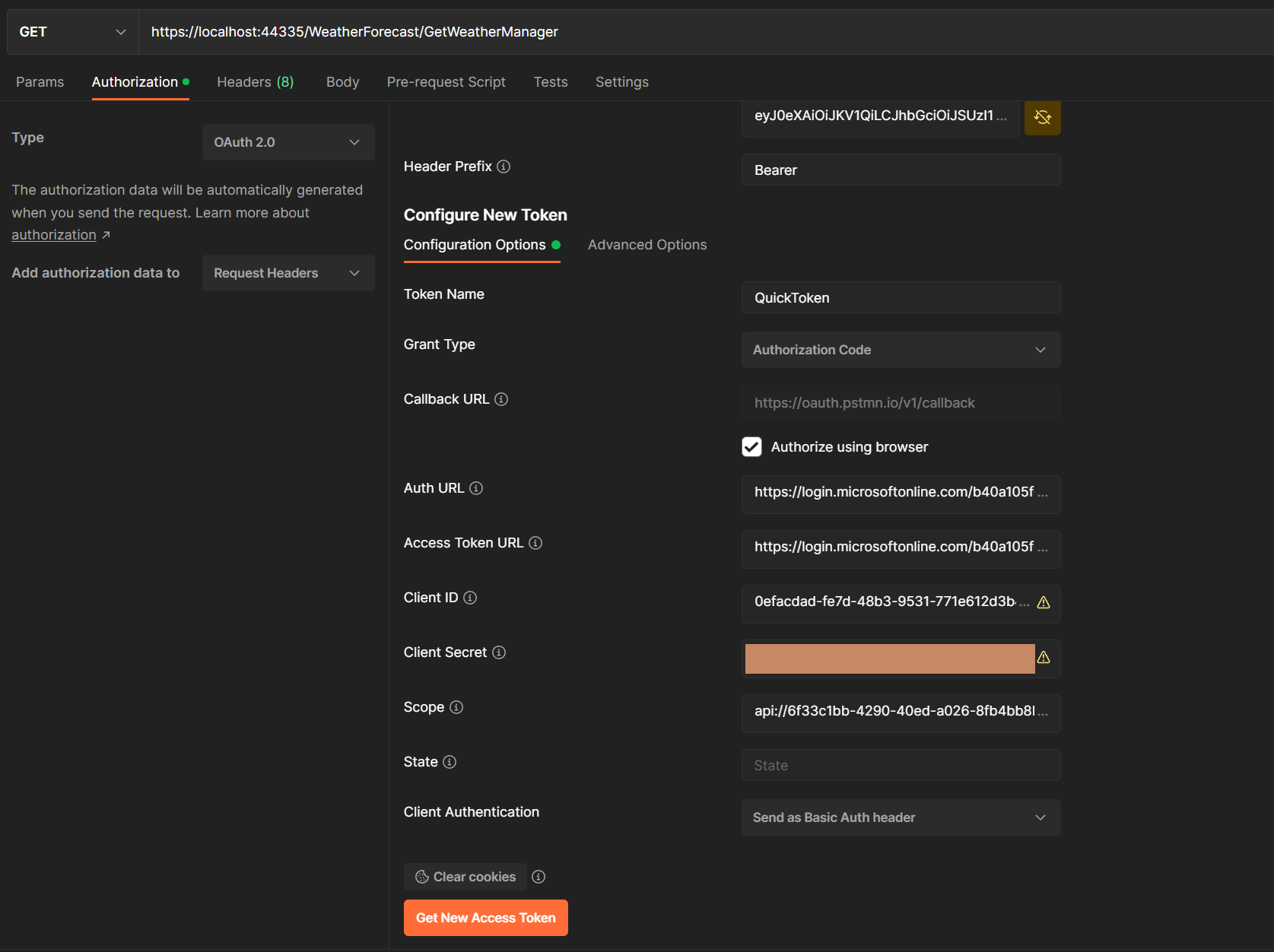
- Request type:
GET - Request URL:
https://localhost:44335/WeatherForecast/GetWeatherManager - Headers:
- Content-Type:
application/x-www-form-urlencoded
- Content-Type:
- Authorization:
- Type:
OAuth 2.0 - Add authorization data to:
Request Headers - Token name:
QuickToken - Grant type:
Authorization Code - Callback URL:
https://oauth.pstmn.io/v1/callback - Auth URL:
https://login.microsoftonline.com/b40a105f-0643-4922-8e60-10fc1abf9c4b/oauth2/v2.0/authorize - Access Token URL:
https://login.microsoftonline.com/b40a105f-0643-4922-8e60-10fc1abf9c4b/oauth2/v2.0/token - Client ID:
0efacdad-fe7d-48b3-9531-771e612d3b4e - Client Secret:
Create you own in app regirstation -> Certificates and secrets - Scope:
api://6f33c1bb-4290-40ed-a026-8fb4bb8b326e/QuickAndSimpleApiAuth.All - Client Authentication:
Send as Basic Auth header
- Type:
- Postman config screenshot