-
-
Save leona4040/6541e3b11da6ea7675d0498d0db98832 to your computer and use it in GitHub Desktop.
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| In firmware version 4.50 of Zyxel XGS2210-52HP, Multiple stored Cross-site scripting (XSS) vulnerability allows remote authenticated users to inject arbitrary web script via rpSys.html. |
Sign up for free
to join this conversation on GitHub.
Already have an account?
Sign in to comment
Product:Zyxel XGS2210-52HP



FW version info:4.50
inject arbitrary web script or HTML via the "port_setup name" field.
an attacker to execute arbitrary JavaScript code within the auto login admin management page.
inject arbitrary web script or HTML via the "classifier config name" field.
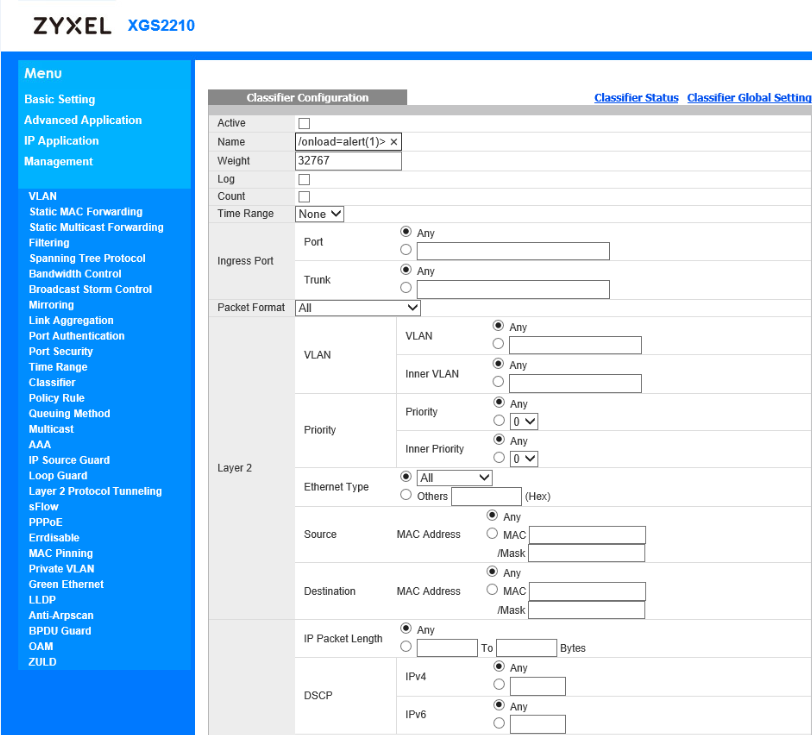


via F12 button, you can seeinject arbitrary web script
an attacker to execute arbitrary JavaScript code within the auto login admin management page.
inject arbitrary web script or HTML via the "filter name" field.


an attacker to execute arbitrary JavaScript code within the auto login admin management page.
inject arbitrary web script or HTML via the "location" field.

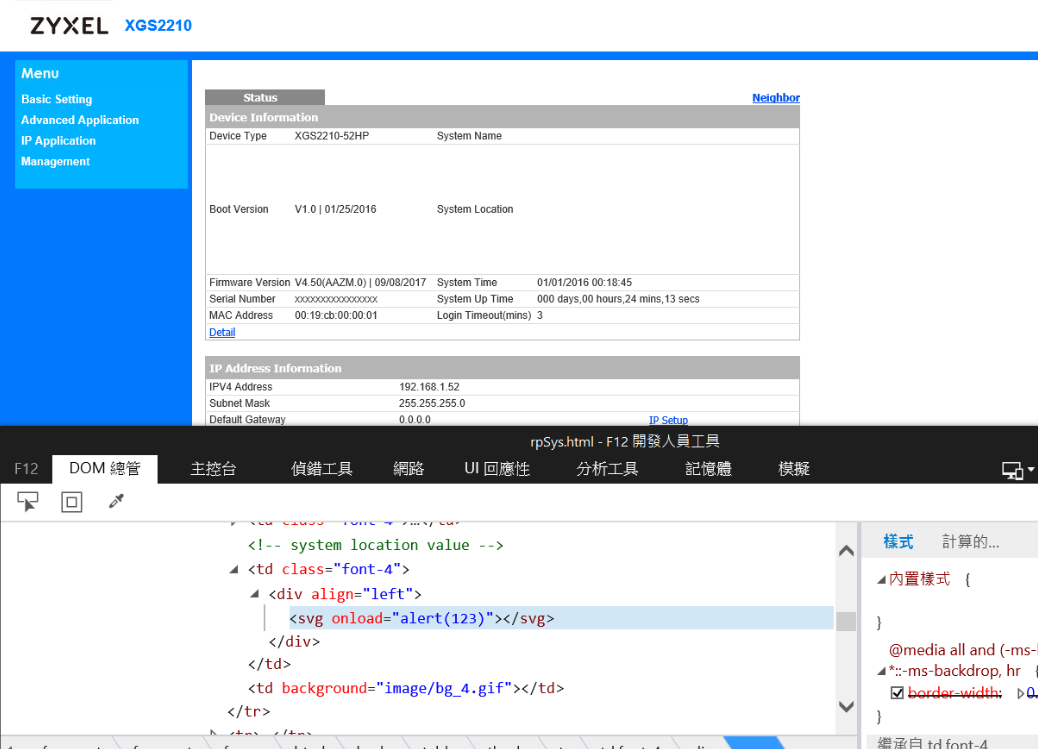

via F12 button, you can seeinject arbitrary web script
an attacker to execute arbitrary JavaScript code within the auto login admin management page.
inject arbitrary web script or HTML via the "system name" field.
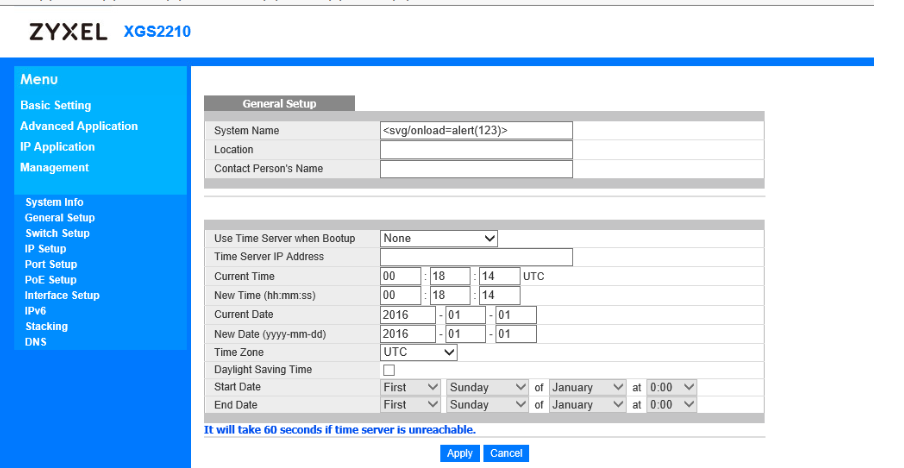

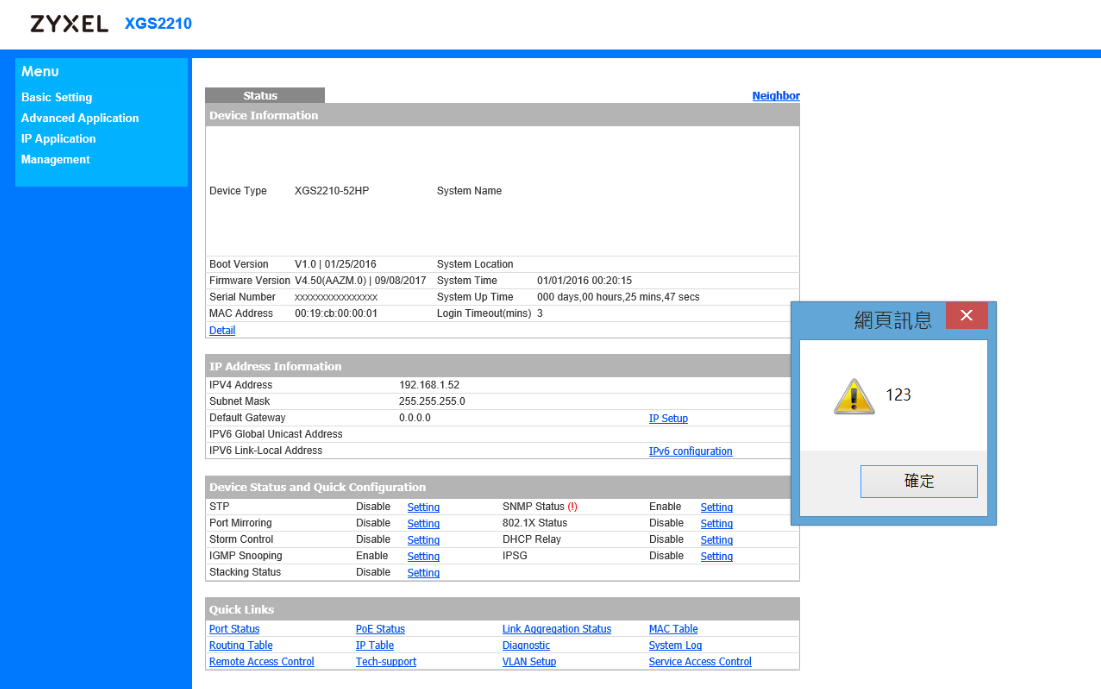
via F12 button, you can seeinject arbitrary web script
an attacker to execute arbitrary JavaScript code within the auto login admin management page.
inject arbitrary web script or HTML via the "static multicate forwarding name" field.


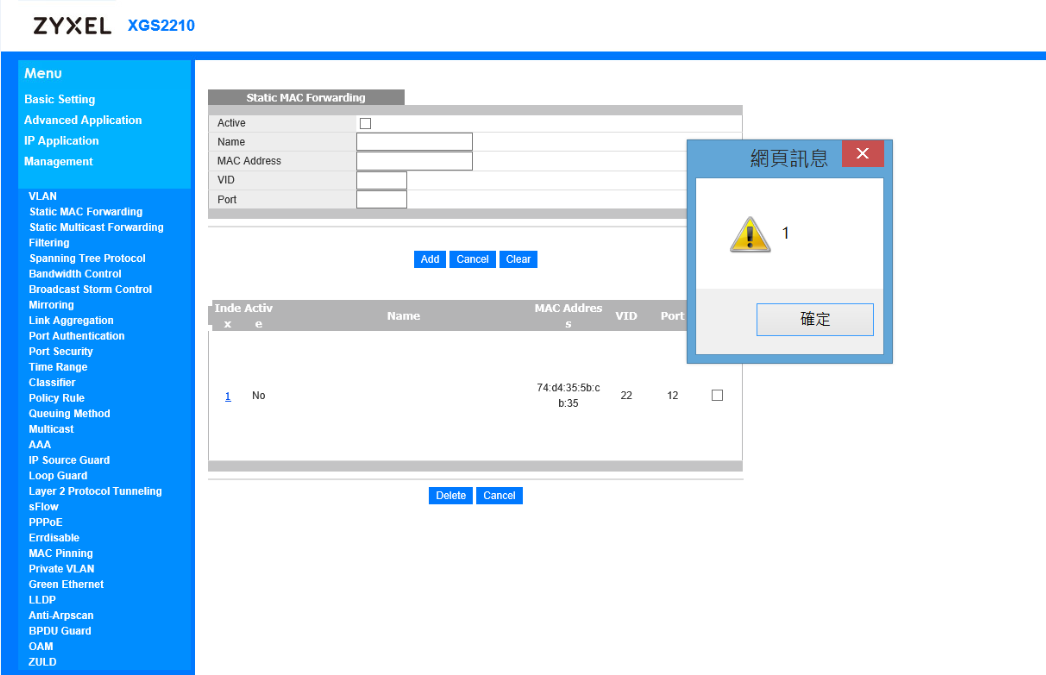
via F12 button, you can seeinject arbitrary web script
an attacker to execute arbitrary JavaScript code within the auto login admin management page.