Route all traffic with a raspberry pi like a VPN.
- get raspbian up and running https://www.raspberrypi.org/downloads/raspbian/
- turn on ssh https://www.raspberrypi.org/documentation/remote-access/ssh/README.md
- maybe update your packages
- install zerotier with linux instruction https://zerotier.com/download.shtml
- create account
- create network on Networks tab
- copy Network ID
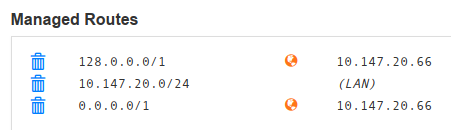
- delete the auto-assign range and managed route for IPv4
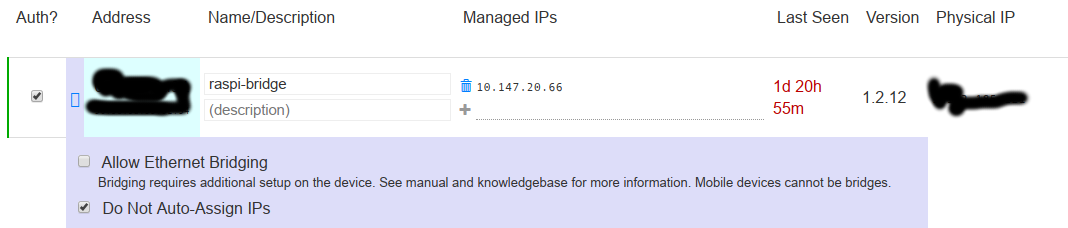
- ip listed here must be what gets assigned in zerotier web interface 'managed ips' section
10.147.20.66. See below - eth0 of raspberry pi
10.147.17.1
- The main point is that the local-physical-ethernet-network
10.147.17.0/24and zt-network is10.147.20.0/24 - If you have public ips it did not work for me
sudo zerotier-cli join ${networkId}
- Since our office has NAT network I have blacked the public IP - right side...
- Warning: Do not enable Bridge
# Include files from /etc/network/interfaces.d:
source-directory /etc/network/interfaces.d
auto eth0
iface eth0 inet manual
auto eth0
iface eth0 inet static
address 10.147.17.1
netmask 255.255.255.0
broadcast 10.147.20.255
gateway 10.147.20.254
dns-nameservers redacted
dns-search redacted
This file is default
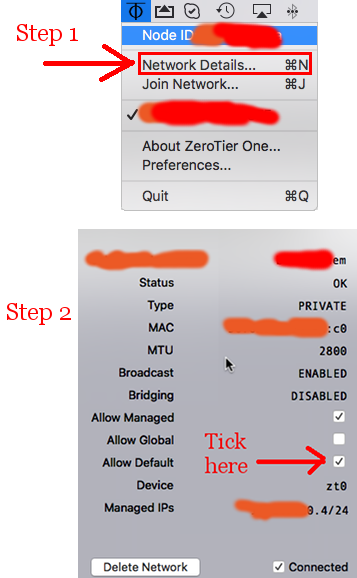
allowManaged=1
allowGlobal=0
allowDefault=0
ip a
1: lo:
2: eth0:
3: wlan0:
5: zt0:
/etc/sysctl.conf
net.ipv4.ip_forward=1
#!/bin/bash
# A very basic IPtables / Netfilter script /etc/firewall/enable.sh
PATH='/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin'
#service networking restart > /dev/null 2>&1
touch /root/RUNNING_FIREWALL_IPTABLES_NOW
# Flush the tables to apply changes
/sbin/iptables -F
# Default policy to drop 'everything' but our output to internet
/sbin/iptables -P FORWARD ACCEPT
/sbin/iptables -P INPUT ACCEPT
/sbin/iptables -P OUTPUT ACCEPT
# Allow established connections (the responses to our outgoing traffic)
/sbin/iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
# Allow local programs that use loopback (Unix sockets)
/sbin/iptables -A INPUT -s 127.0.0.0/8 -d 127.0.0.0/8 -i lo -j ACCEPT
/sbin/iptables -t nat -A POSTROUTING -o enp2s0 -j MASQUERADE
/sbin/iptables -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
/sbin/iptables -A FORWARD -i ztklhsm3zp -o enp2s0 -j ACCEPT
exit 0
Hi ! I have tried your tutorial, but I am not sure what to do with the last script " #!/bin/bash... "
I have also tried the DO tutorial and I got stuck on step 5
sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADEMy eth0 is named enp0s3 and the zt0 is named enp0s3, so I changed the script to:
sudo iptables -t nat -A POSTROUTING -o enp0s3 -j MASQUERADE sudo iptables -A FORWARD -i zt21r4amuq -o enp0s3 -j ACCEPTIf I set default route on my phone, I cant acces internet or the network at all.
Can you help me with it ? What to do with the last script ? Or that to do in the DO tutorial to make it works ?
Thank you.