Its unfortunately extremely common for customers and enterprises operating in AWS to have chosen a workload/storage bearing account (more than likely, the main production account) as the Organization Management Account (formerly known Organization "Master" account, before AWS adopted better naming).
Many customers and companies operating in AWS made this decision in 2018 or so and its unforunately not something that can be easily changes as of today (2024). Many customers have requests to AWS to make a friendly path for rehoming the Org Management account but last I heard it is still not prioritized. Thus, we as customers are left to go through the nerve-wracking, if not dangerous process of migrating to a new AWS Organization in order to align with modern best practices and reduce common privilege escalation and account to account lateral movement concerns (made worse if you happen to have enabled things like Cloudformation Stacksets, Control Tower, or other powerful services in the s
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Windows Registry Editor Version 5.00 | |
| [HKEY_CURRENT_USER\Software\7-Zip\Options] | |
| "WriteZoneIdExtract"=dword:00000001 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| # See https://halu.lu/%E6%9D%82%E8%B0%88/cloudflare-warp/ | |
| # Depolyed at https://warp.halu.lu/ | |
| // Change keys if needed | |
| const keys = [ | |
| "9WO41D5p-6OP8xj27-36gQG75D", | |
| "R65K12Up-aU907O2e-4nuvD581", | |
| "06LM94EJ-1nl0V2d7-V847va5y", | |
| ] |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #include <windows.h> | |
| #include <iostream> | |
| #include <chrono> | |
| #include <ctime> | |
| #include <sstream> | |
| // White Knight Labs - Offensive Development Course | |
| // DLL Kill Date Example | |
| bool parseDate(const std::string& dateStr, std::tm& date) { |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| /* | |
| TaskManagerSecret | |
| Author: @splinter_code | |
| This is a very ugly POC for a very unreliable UAC bypass through some UI hacks. | |
| The core of this hack is stealing and using a token containing the UIAccess flag set. | |
| A trick described by James Forshaw, so all credits to him --> https://www.tiraniddo.dev/2019/02/accessing-access-tokens-for-uiaccess.html | |
| From there it uses a task manager "feature" to run a new High IL cmd.exe. | |
| This has been developed only for fun and shouldn't be used due to its high unreliability. |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #!/usr/bin/env bash | |
| word_max=9 # Exclude words longer than this | |
| nphrases=3 # Generate this many passphrases | |
| defwords=4 # Default number of words/phrase | |
| pls() { | |
| local -i n=${#1} r=$2 | |
| local s | |
| printf -v s -- ' %s%*s%s\n' \ |
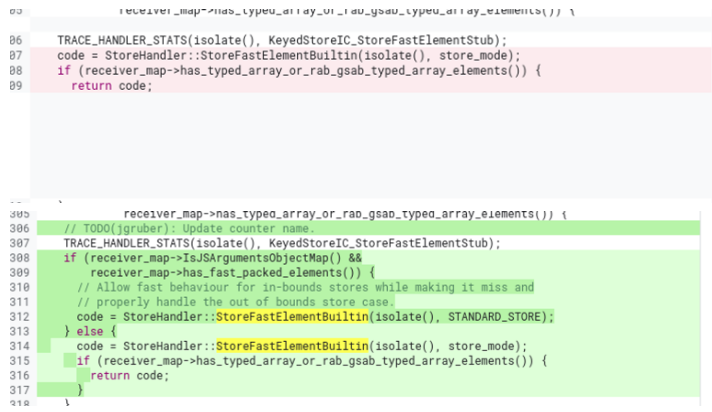
Official patch: https://chromium-review.googlesource.com/c/v8/v8/+/4584248
Patch come from KeyedStoreIC::StoreElementHandler(), it returns fast path code(Turbofan builtin) for keyed store depends on "receiver_map" and "store_mode". Based on the content of this function is all about element STORE, I personally believe that this is an OOB writes vulnerability.
If we divide the PoC exploration into two parts based on this func, they are:
NewerOlder