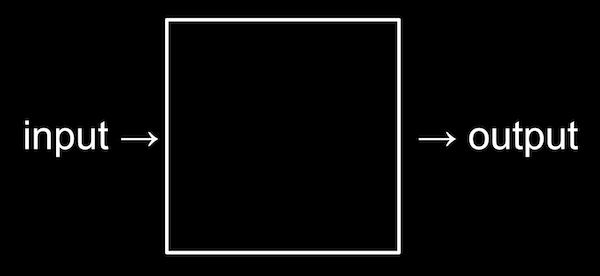
What is computer science - problem solving
Ten digits - Human
0 1 2 3 4 5 6 7 8 9
Two digits - Computer
0 1
bits = binary + digits
Physical input of computer is electricity
| 100 | 10 | 1 |
|---|---|---|
| 1 | 2 | 3 |
| 100x1 | 10x2 | 1x3 |
|---|---|---|
| 100 | 20 | 3 |
| 10^2 | 10^1 | 10^0 | |
|---|---|---|---|
| # | # | # | human world |
| 2^2 | 2^1 | 2^0 | |
|---|---|---|---|
| # | # | # | binary system |
| 4 | 2 | 1 |
| binary | decimal |
|---|---|
| 001 | 1 |
| 010 | 2 |
| 011 | 3 |
| 100 | 4 |
| 101 | 5 |
| 110 | 6 |
| 111 | 7 |
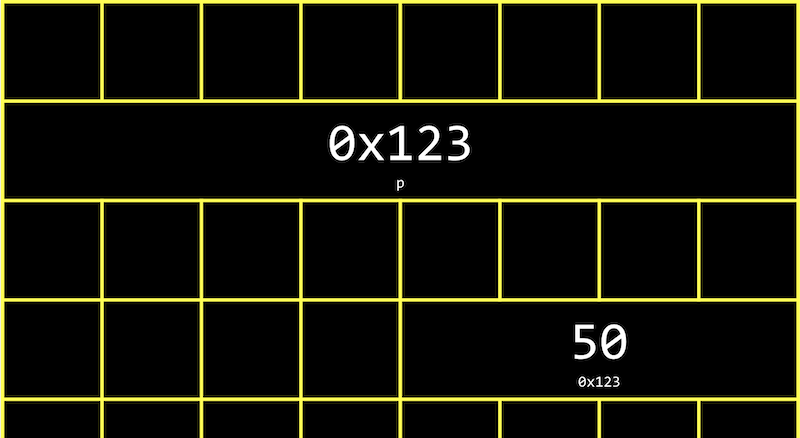
| 110010 | 50 |
Computers only compute
| A | character |
| 65 | decimal |
| 01000001 | binary |
| ASCII | |||
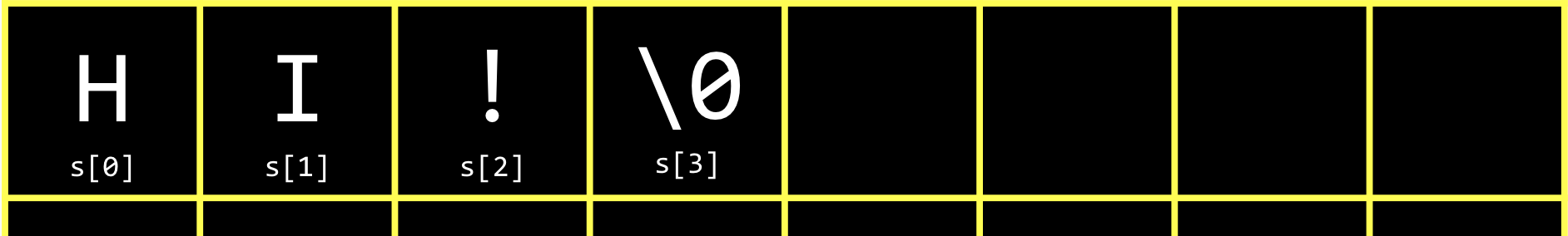
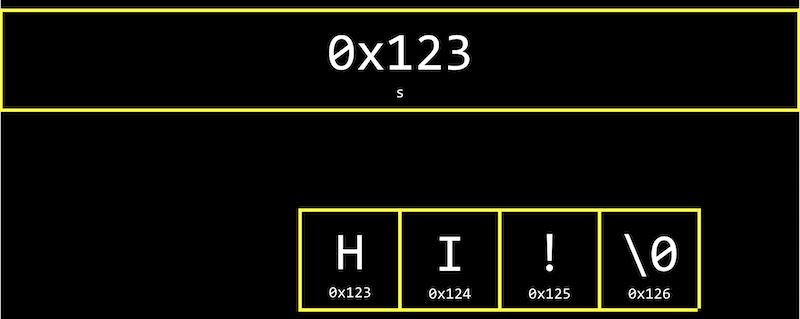
| character | H | I | ! |
| decimal | 72 | 73 | 33 |
| binary | 01001000 | 01001001 | 00100001 |
1 bytes = 8 bits
How many symbols can you represent with 8 bits?
256 = 2x2x2x2x2x2x2x2
Unicode
An example emoji = 128514(decimal)
| RGB | |||
| red | green | blue | photoshoot, images |
| 72 | 73 | 33 | decimal |
algorithms - step by step computer gets what you want
bug - mistake in problem or algorithm
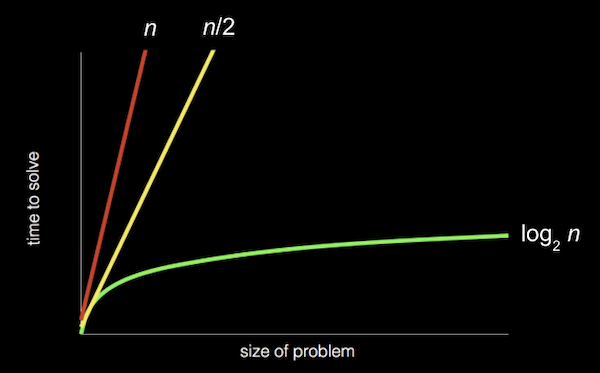
third algorithm - faster, more efficient
Pseudocode
1 *Pick up* phone book
2 *Open* to middle of phone book
3 *Look* at page
4 **If** person is on page
5 *Call* person
6 **Else if** person is earlier in book
7 *Open* to middle of left half of book
8 *Go back* to line 3
9 **Else if** person is later in book
10 *Open* to middle of right half of book
11 *Go back* to line 3
12 **Else**
13 *Quit*
- functions
- conditions
- Boolean expressions
- loops
- variables
- threads
- events
- ...
Actual code
#include<stdio.h>
int main(void)
{
printf("hello, world\n");
}