- We have an app that the users can log in only with a few selected social and the enterprise connections. These users should have a specific app_metadata and user_metadata starting from the first login.
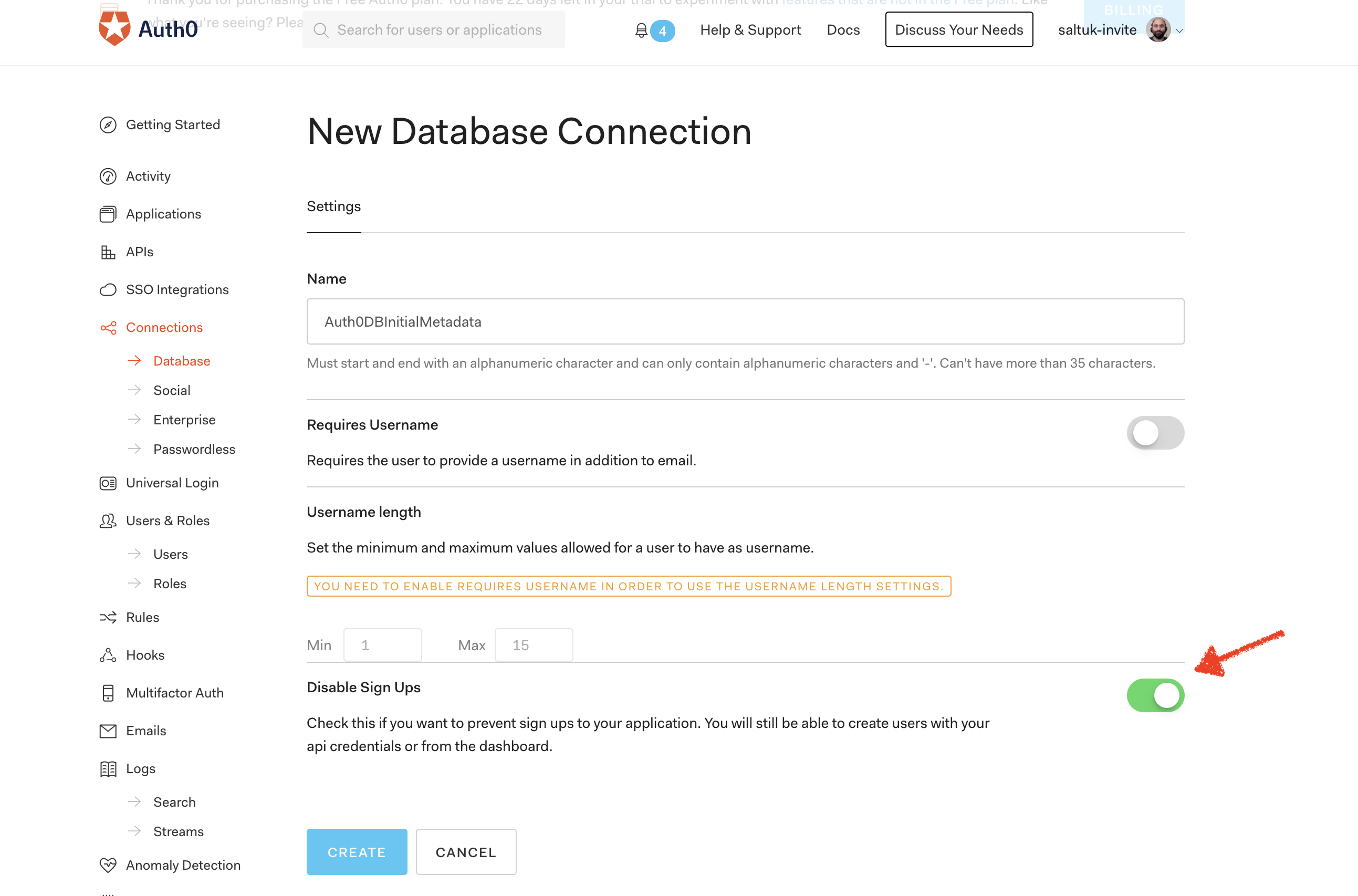
1-) Creaate a regular Auth0 DB connection with signup option turned off. Let's assume it's named as Auth0DBInitialMetadata.
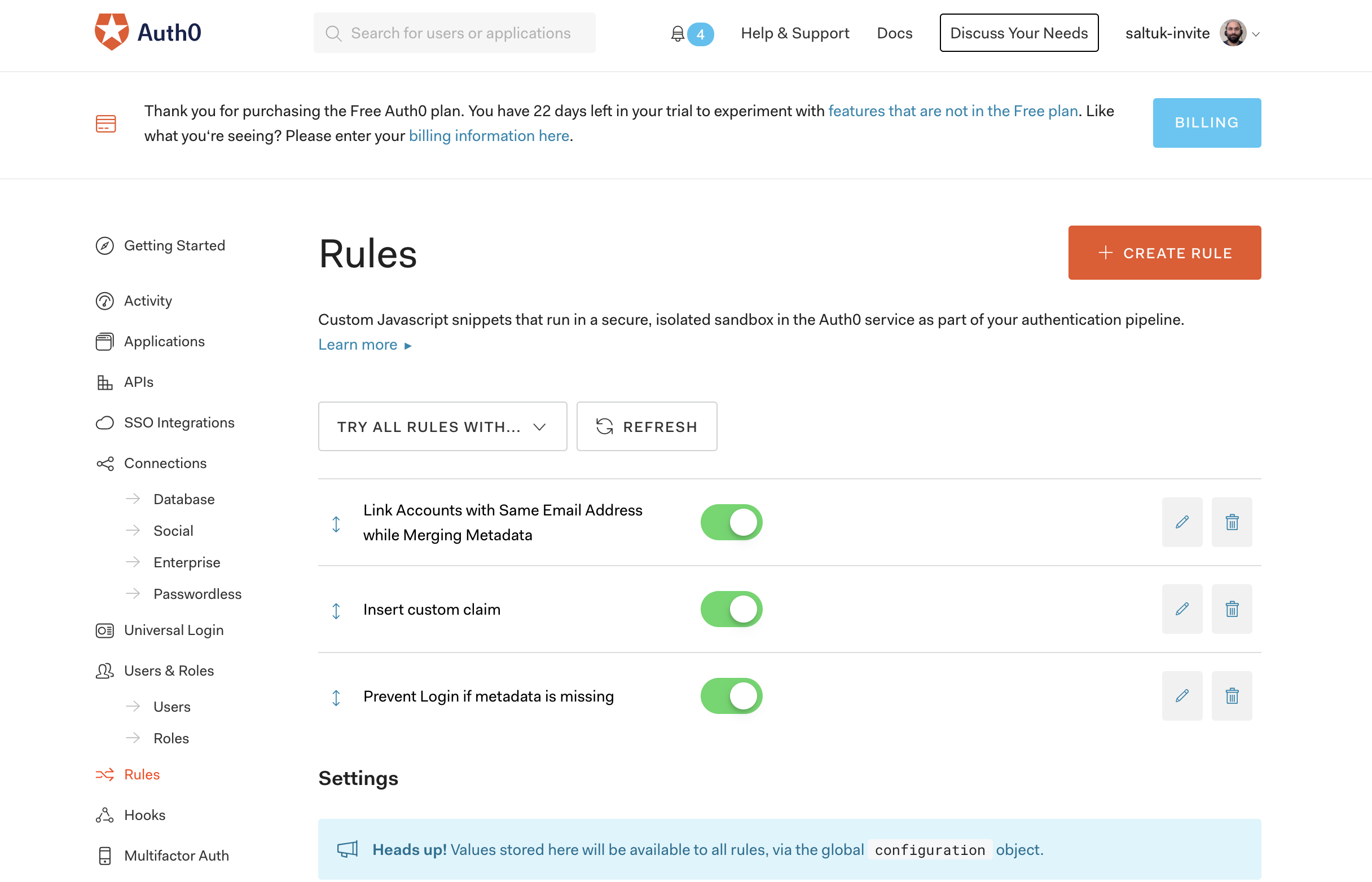
2-) Set a rule which prevents login in with the Auth0 DB connection above. So that this connection isn't used for login directly unintentionally.
E.g.:
function whitelistForSpecificConnection(user, context, callback) {
if(context.connection === 'Auth0DBInitialMetadata') {
return callback(new UnauthorizedError('Access denied.'));
}
callback(null, user, context);
}
3-) Use the following account linking rule which merges the user's metadata and allows using the merged metadata on the next rules.
4-) No need to enable the Auth0DBInitialMetadata connection for the application. Only enabling the required social and enterprise connection is sufficient.
5-) (optional) Add a rule which inserts the user's app metadata and user metadata into the id_token as custom claims.
E.g.:
function(user, context, callback) {
const namespace = 'https://myapp.example.com/';
context.idToken[namespace + 'company'] = global.updateAppMetadata && global.updateAppMetadata.company || user.app_metadata && user.app_metadata.company || "unemployed";
context.idToken[namespace + 'middle_name'] = global.updateUserMetadata && global.updateUserMetadata.middle_name || user.user_metadata && user.user_metadata.middle_name || "no middle name";
callback(null, user, context);
}
6-) (optional) Add a rule to prevent login if certain metadata is missing so that the user can't use the social or the enterprise connection until they are manually created on the Auth0 regular DB.
E.g:
function(user, context, callback) {
if (global.updateAppMetadata && global.updateAppMetadata.company || user.app_metadata && user.app_metadata.company) {
return callback(null, user, context);
}
callback(new UnauthorizedError('Access denied.'));
}
1-) Use the management API to create the user.
E.g.
POST /api/v2/users
{
"email": "saltukalakus@gmail.com",
"password": GENERATE_A_RANDOM_STRONG_PASSWORD,
"connection": "Auth0DBInitialMetadata",
"app_metadata": { "company": "auth0"}, //attributes users should not be able change themselves.
"user_metadata": { "middle_name": "rasim" }, // attributes users may change themselves.
}
2-) Wait for the user to login with their social or enterprise account. As the account linking rule is in place, the user will have the required metadata starting from the first login.
Passwordless flow isn't supported with the new universal login as of April 2020