Jaff ransomware makes entries in the Windows Registry to achieve a form of persistence, and even launch and repress processes inside the Windows Operating System. Some of these entries are designed in a way that will start the virus automatically with every launch of Windows. One registry entry reported to be implemented by this ransomware is the following:
→HKCU\Control Panel\Desktop\Wallpaper “C:\ProgramData\Rondo\WallpapeR.bmp”
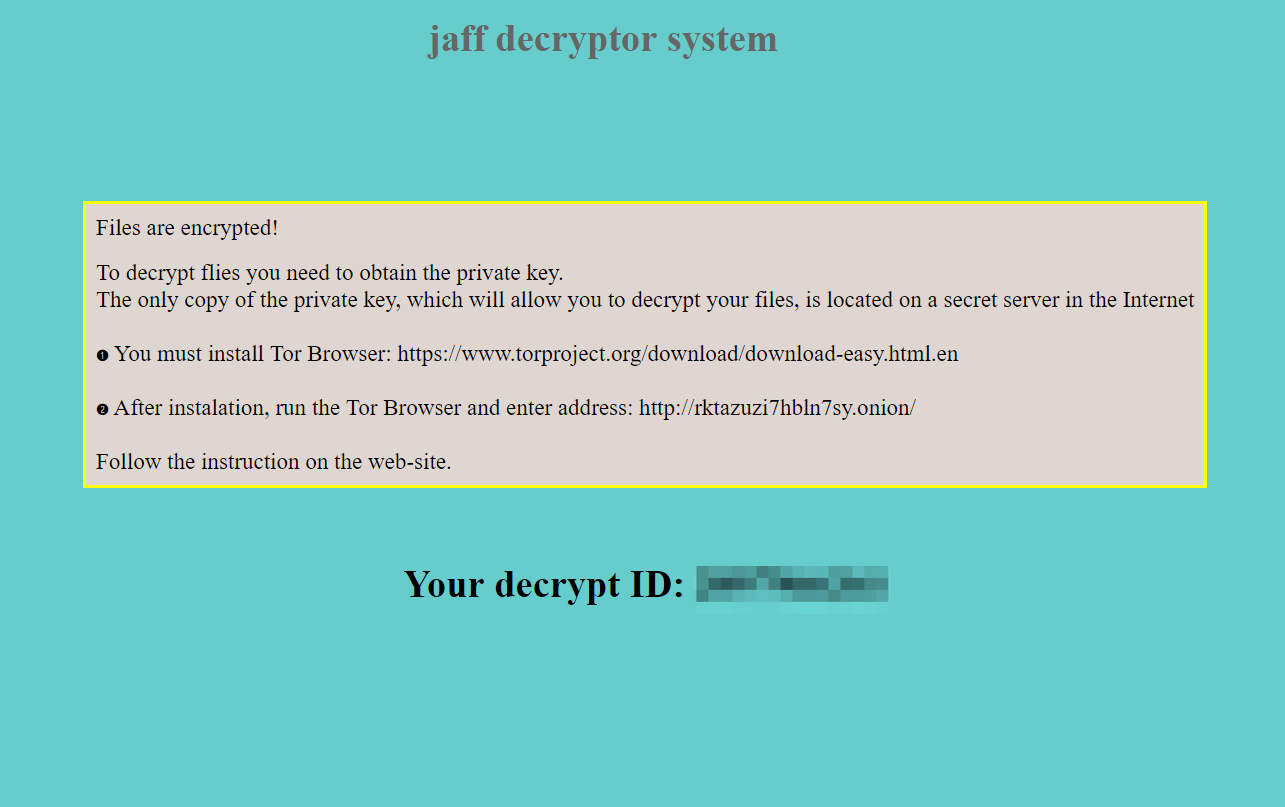
The ransom note will be displayed after the encryption process is complete. It will be put in three identical files which are ReadMe.bmp, ReadMe.html and ReadMe.txt. Inside them there will be instructions.
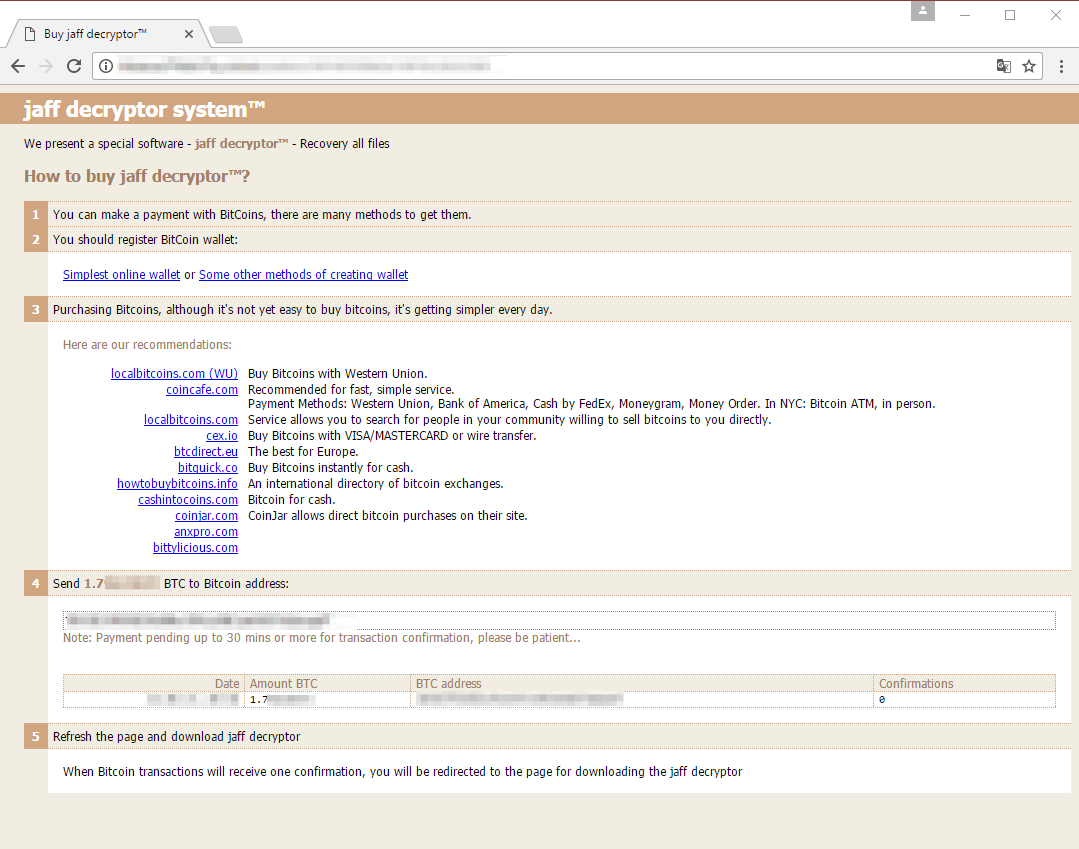
Jaff Ransomware Indicators of Compromise (IOCs) IOC IOC Type Description 5bd8352171880485bf06d2d089e39d4112e8540f28d0f84bb045ab58737ad6bf SHA256 nm.pdf email attachment f41b4b6de5d7680b554b177ab6ebad01b5248a7b54044d64bf0593f383166eec SHA256 CM9SJG1.docm embedded in nm.pdf hxxp://5hdnnd74fffrottd[.]com/af/f87346b URL Payload URL hxxp://babil117[.]com/f87346b URL Payload URL hxxp://boaevents[.]com/f87346b URL Payload URL hxxp://byydei74fg43ff4f[.]net/af/f87346b URL Payload URL hxxp://easysupport[.]us/f87346b URL Payload URL hxxp://edluke[.]com/f87346b URL Payload URL hxxp://julian-g[.]ro/f87346b URL Payload URL hxxp://phinamco[.]com/f87346b URL Payload URL hxxp://takanashi[.]jp/f87346b URL Payload URL hxxp://techno-kar[.]ru/f87346b URL Payload URL hxxp://tending[.]info/f87346b URL Payload URL hxxp://tiskr[.]com/f87346b URL Payload URL hxxp://trans-atm[.]com/f87346b URL Payload URL hxxp://trialinsider[.]com/f87346b URL Payload URL hxxp://vscard[.]net/f87346b URL Payload URL hxxp://wipersdirect[.]com/f87346b URL Payload URL hxxp://fkksjobnn43[.]org/a5/ URL Jaff C&C hxxp://rktazuzi7hbln7sy[.]onion/ URL Payment URL
The different subject lines that are being used are:
Copy_[Random Numbers] Document_[Random Numbers] Scan_[Random Numbers] File_[Random Numbers] PDF_[Random Numbers]
Jaff will now begin to encrypt the victims computer using AES encryption. When encrypting a computer, Jaff will only encrypt files that contain certain file extensions. The file extensions targeted by Jaff are:
.xlsx | .acd | .pdf | .pfx | .crt | .der | .cad | .dwg | .MPEG | .rar | .veg | .zip | .txt | .jpg | .doc | .wbk | .mdb | .vcf | .docx | .ics | .vsc | .mdf | .dsr | .mdi | .msg | .xls | .ppt | .pps | .obd | .mpd | .dot | .xlt | .pot | .obt | .htm | .html | .mix | .pub | .vsd | .png | .ico | .rtf | .odt | .3dm | .3ds | .dxf | .max | .obj | .7z | .cbr | .deb | .gz | .rpm | .sitx | .tar | .tar.gz | .zipx | .aif | .iff | .m3u | .m4a | .mid | .key | .vib | .stl | .psd | .ova | .xmod | .wda | .prn | .zpf | .swm | .xml | .xlsm | .par | .tib | .waw | .001 | .002 | 003. | .004 | .005 | .006 | .007 | .008 | .009 | .010 | .contact | .dbx | .jnt | .mapimail | .oab | .ods | .ppsm | .pptm | .prf | .pst | .wab | .1cd | .3g2 | .7ZIP | .accdb | .aoi | .asf | .asp. | aspx | .asx | .avi | .bak | .cer | .cfg | .class | .config | .css | .csv | .db | .dds | .fif | .flv | .idx | .js | .kwm | .laccdb | .idf | .lit | .mbx | .md | .mlb | .mov | .mp3 | .mp4 | .mpg | .pages | .php | .pwm | .rm | .safe | .sav | .save | .sql | .srt | .swf | .thm | .vob | .wav | .wma | .wmv | .xlsb | .aac | .ai | .arw | .c | .cdr | .cls | .cpi | .cpp | .cs | .db3 | .docm | .dotm | .dotx | .drw | .dxb | .eps | .fla | .flac | .fxg | .java | .m | .m4v | .pcd | .pct | .pl | .potm | .potx | .ppam | .ppsx | .ps | .pspimage | .r3d | .rw2 | .sldm | .sldx | .svg | .tga | .wps | .xla | .xlam | .xlm | .xltm | .xltx | .xlw | .act | .adp | .al | .bkp | .blend | .cdf | .cdx | .cgm | .cr2 | .dac | .dbf | .dcr | .ddd | .design | .dtd | .fdb | .fff | .fpx | .h | .iif | .indd | .jpeg | .mos | .nd | .nsd | .nsf | .nsg | .nsh | .odc | .odp | .oil | .pas | .pat | .pef | .ptx | .qbb | .qbm | .sas7bdat | .say | .st4 | .st6 | .stc | .sxc | .sxw | .tlg | .wad | .xlk | .aiff | .bin | .bmp | .cmt | .dat | .dit | .edb | .flvv | .gif | .groups | .hdd | .hpp | .log | .m2ts | .m4p | .mkv | .ndf | .nvram | .ogg | .ost | .pab | .pdb | .pif | .qed | .qcow | .qcow2 | .rvt | .st7 | .stm | .vbox | .vdi | .vhd | .vhdx | .vmdk | .vmsd | .vmx | .vmxf | .3fr | .3pr | .ab4 | .accde | .accdt | .ach | .acr | .adb | .srw | .st5 | .st8 | .std | .sti | .stw | .stx | .sxd | .sxg | .sxi | .sxm | .tex | .wallet | .wb2 | .wpd | .x11 | .x3f | .xis | .ycbcra | .qbw | .qbx | .qby | .raf | .rat | .raw | .rdb | rwl | .rwz | .s3db | .sd0 | .sda | .sdf | .sqlite | .sqlite3 | .sqlitedb | .sr | .srf | .oth | .otp | .ots | .ott | .p12 | .p7b | .p7c | .pdd | .pem | .plus_muhd | .plc | .pptx | .psafe3 | .py | .qba | .qbr.myd | .ndd | .nef | .nk | .nop | .nrw | .ns2 | .ns3 | .ns4 | .nwb | .nx2 | .nxl | .nyf | .odb | .odf | .odg | .odm | .ord | .otg | .ibz | .iiq | .incpas | .jpe | .kc2 | .kdbx | .kdc | .kpdx | .lua | .mdc | .mef | .mfw | .mmw | .mny | .moneywell | .mrw.des | .dgc | .djvu | .dng | .drf | .dxg | .eml | .erbsql | .erd | .exf | .ffd | .fh | .fhd | .gray | .grey | .gry | .hbk | .ibank | .ibd | .cdr4 | .cdr5 | .cdr6 | .cdrw | .ce1 | .ce2 | .cib | .craw | .crw | .csh | .csl | .db_journal | .dc2 | .dcs | .ddoc | .ddrw | .ads | .agdl | .ait | .apj | .asm | .awg | .back | .backup | .backupdb | .bank | .bay | .bdb | .bgt | .bik | .bpw | .cdr3 | .as4 | .tif | .asp | .hdr