This is the challenge.
In order to protect their maximum security facilities, the Club employs an electronic security lock activated by a 256-bit key which changes every minute. When a Club member is authorized to enter some of these facilities, he receives this key in hexadecimal format, the same format which is used to enter the key in the electronic lock’s keyboard. The last year (in 2015), Project SKY intercepted a key valid for April 1st at 11:00 UTC: 01cd9de119e1231e29b0972a618da6c79fc1f3bd96cee86c93a8068bdc5e4c59, however we got access to this key only after it was already expired. It seems that these keys are the same for all facilities, independent from their geographical location, that is, they vary only with time. This year, our truck driver Alisson, undercover in the Club’s fleet, was able to intercept the shipment of one of these locks to a warehouse which is currently under construction. Quickly, he drafted a block diagram of the lock’s circuit and generated a dump of the flash memory (N25Q032A), both contained in the file which we are providing to you. A few minutes after sending this information through 3G using his Samsung Note Edge™ smartphone, Alisson suffered a tragic transit accident, which means the Club has probably discovered our plans, so that we have only 48h before they change all of their electronic lock scheme. Our teams are ready to deploy next to 3 facilities of critical importance to the Club. They only need that you send a key valid for the current minute to the address https://door.pwn2win.party/KEY.
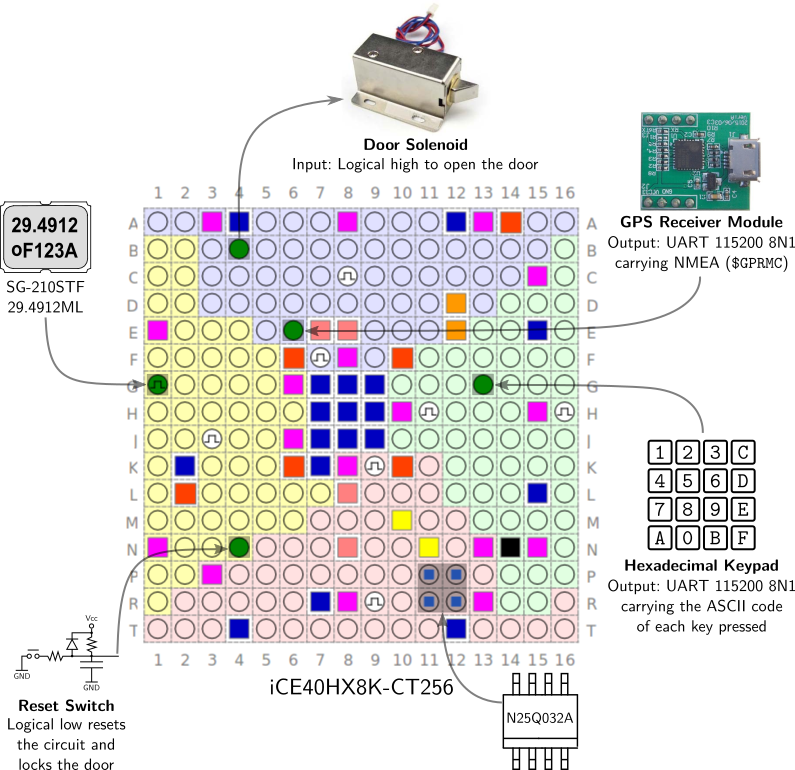
We can find here the dump of the flash memory. And this is the stolen diagram of the lock's circuit:
Some reasonings...
-
iCE40HX8K-CT256: This is a FPGA produced by Lattice Semiconductors. Here is the datasheet. The modifier CT256 means caBGA style with 256 lears, which is the size of the key.
-
Solenoid is what makes the door open, according to the figure (PM confirmed).
-
UART 115200 8N1: GPS module that writes in UART with standard baudrate (115200)
-
Hex keyboard: It enters the keys, probably as password prompt. It uses UART with the same standard baudrate.
-
N25Q032A: NOR Flash Serial-SPI. That's where the dump is from!
-
Reset switch: Probably what makes the key to be reset.
So we have a key, we have the binary file from the flash drive, we have the circuit diagram, and we have a clue as to what each component is doing. The first thing I tried was to check whether I could simulate a FPGA. If I could, I probably would be able to use the provided key and then propagate it until the desired time... Looking quickly at wikipedia, I found Icarus Verilog, which means there is a chance. However, I apparently cannot use the binary file -- I would need the verilog code. Thus, the best next move would be to try and reverse-engineer the binary file.
** 02/05/2017 12pm - ** According to PM: iverilog is not very fast to simulate that circuit. His communication with me:
> quando eu resolvi meu próprio problema,
eu perdi 1 dia inteiro com isso hehe
> o iverilog não é rápido o suficiente 😛
> tem que usar um simulador mais rápido que ele..
> existe simulador opensource mais veloz
esse foi o primeiro hint que dei
depois eu dei um outro, que era o site do simulador
mas veja se vc acha sozinho
** 19:56 -** Attempting to reverse engineer the binary file. After duck-duck-ing "reverse engineer fpga iCE40", I have found the project IceStorm.
** 20:05 -** Installed IceStorm on a VMBOX on Ubuntu. Following their documentation:
sudo apt-get install build-essential clang bison flex libreadline-dev \
gawk tcl-dev libffi-dev git mercurial graphviz \
xdot pkg-config python python3 libftdi-dev
git clone https://github.com/cliffordwolf/icestorm.git
cd icestorm
make
sudo make install
I did not use -j flag...
** 20:12 - ** Installation done. Jaque wants to have dinner...
** 11:00 - ** Back and trying to understand icestorm. Apparently before anything I need bin -> ascii.
** 11:34 - ** I used ice(un)pack (learned from documentation):
iceunpack timekeeperslock.bin > timekeeperslock.bin.ascii
** 11:40 - ** Converting into description of cell configuration
python3 icebox_explain.py < timekeeperslock.bin.ascii > timekeeperslock.bin.ascii.cellconfig
** 11:45 - ** Everything seems to be working quite well. Trying now to get it into verilog:
python3 icebox_vlog.py timekeeperslock.bin.ascii > timekeeperslock.bin.ascii.vlog
It does take a while, but once it is done, this is how the resulting file looks like:
usr@vu3box:~/pm/$ more timekeeperslock.bin.ascii.vlog
// Reading file 'timekeeperslock.bin.ascii'...
module chip (input io_0_17_0, input io_0_3_0, input io_33_23_1, input io_7_33_0, output io_6_33_1);
wire n1;
// (0, 0, 'glb_netwk_1')
// (2, 25, 'lutff_global/cen')
// (2, 28, 'lutff_global/cen')
// (4, 24, 'lutff_global/cen')
// (4, 24, 'neigh_op_tnr_3')
// (4, 25, 'lutff_global/cen')
// (4, 25, 'neigh_op_rgt_3')
// (4, 26, 'lutff_global/cen')
(...)
** 11:53 - ** icebox_vlog has an interesting option -s, which stripes all comments.
usr@vu3box:~/pm/icestorm/icebox$ python3 icebox_vlog.py timekeeperslock.bin.ascii > timekeeperslock.bin.ascii.vlog
usr@vu3box:~/pm/icestorm/icebox/$ more timekeeperslock.bin.ascii.vlog
module chip (input io_0_17_0, input io_0_3_0, input io_33_23_1, input io_7_33_0, output io_6_33_1);
wire n1, n2, io_0_17_0, n4, n5, n6, io_0_3_0, n17, n20, n22;
wire n27, n39, n40, n42, n45, n51, n60, n63, n81, n83;
wire n106, n108, n115, n117, n118, n129, n130, n131, n132, n133;
wire n134, n136, n137, n138, n140, n141, n143, n144, n145, n146;
wire n148, n150, n151, n152, n153, n154, n155, n158, n159, n160;
wire n162, n163, n164, n165, n166, n167, io_33_23_1, n173, n175, n179;
(...)
** 11:55 - ** Am I done?
** 05/02 ~12pm - ** PM said the code seems correct :)
** 05/02 13:09 - ** Ok, so PM said iverilog is not a good option because it is slow. Here is a list of things that may be informative in this regard:
https://www.aldec.com/en/products/fpga_simulation/active-hdl/feature/83
https://www.veripool.org/wiki/veripool/Verilog_Simulator_Benchmarks
http://www.embecosm.com/appnotes/ean6/embecosm-or1k-verilator-tutorial-ean6-issue-1.html
BB suggested looking into qucs
** 1:18 - ** Final decision for verilator. In Wikiedia's comparison page, they explicitly say verilator is the fatest available nowadays. https://en.wikipedia.org/wiki/Comparison_of_EDA_software