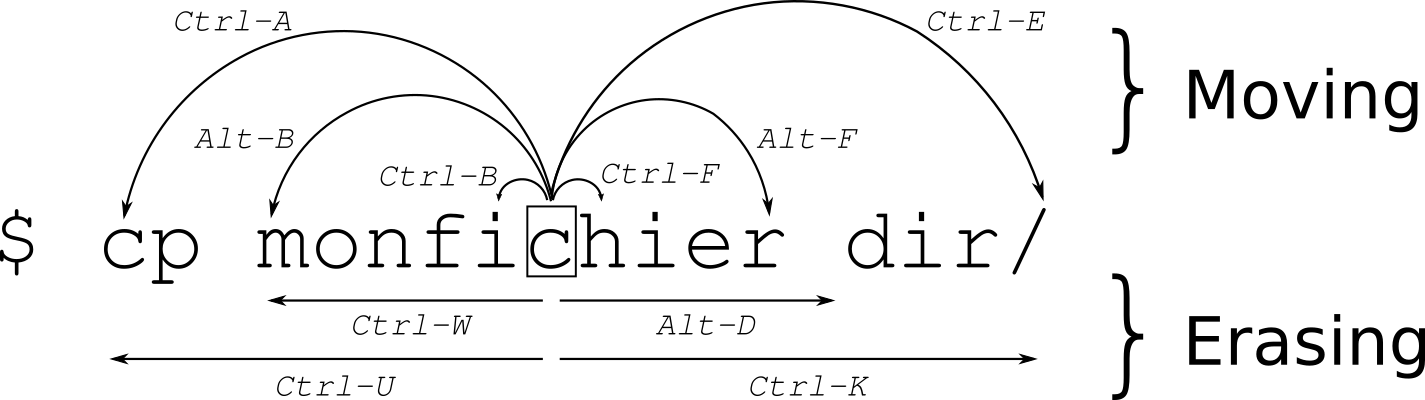
h - Move left
j - Move down
k - Move up
l - Move right
$ - Move to end of line
0 - Move to beginning of line (including whitespace)
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| ##TCP FLAGS## | |
| Unskilled Attackers Pester Real Security Folks | |
| ============================================== | |
| TCPDUMP FLAGS | |
| Unskilled = URG = (Not Displayed in Flag Field, Displayed elsewhere) | |
| Attackers = ACK = (Not Displayed in Flag Field, Displayed elsewhere) | |
| Pester = PSH = [P] (Push Data) | |
| Real = RST = [R] (Reset Connection) | |
| Security = SYN = [S] (Start Connection) |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #Read multiple keys from an authorized_keys file and print the finger print | |
| [root@server01 .ssh]# while read line; do ssh-keygen -l -f /dev/stdin <<< $line; done < authorized_keys | |
| 2048 87:7a:4d:70:d2:10:a4:4b:b7:e1:2b:7c:77:92:25:04 /dev/stdin (RSA) | |
| 2048 7d:f0:89:94:00:09:bc:70:46:59:8d:9a:70:3b:ac:70 /dev/stdin (RSA) | |
| 2048 61:63:ee:0d:f6:d2:d8:d6:ae:37:0c:35:ae:da:51:6a /dev/stdin (RSA) | |
| #read a key from authorized key file | |
| [root@server01 .ssh]# ssh-keygen -l -f authorized_keys | |
| 2048 87:7a:4d:70:d2:10:a4:4b:b7:e1:2b:7c:77:92:25:04 authorized_keys (RSA) |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #!/usr/bin/ruby | |
| DATA.each_line do |line| | |
| puts line | |
| end | |
| __END__ | |
| Doom | |
| Quake | |
| Diablo |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #!/bin/bash | |
| HEIGHT=10 | |
| WIDTH=40 | |
| CHOICE_HEIGHT=4 | |
| BACKTITLE="Cluster Options" | |
| TITLE="Select Cluster" | |
| MENU="Choose one of the following options:" | |
| ENV="${ENV:-dev}" |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #!/bin/bash -x | |
| #Date: 21/7/2017 | |
| #Author: Mohan | |
| #Purpose: To upload files to AWS S3 via Curl | |
| #Uploads file at the top level folder by default | |
| #S3 parameters | |
| S3KEY="XXXXXXXXXXX" | |
| S3SECRET="XXXXXXXXXXXXXXXX" |
NOTE: This used to be a gist that continually expanded. It's now a github project because it's considerably easier for other people to edit, fix and expand on Docker using Github. Just click README.md, and then on the "writing pen" icon on the right to edit.
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #!/usr/bin/env python | |
| #Date: 05/03/2016 | |
| #Author: Mohan Balasundaram | |
| #Purpose: To read a json file with a dictionary list and sort the output | |
| import json | |
| import sys | |
| json_filename=sys.argv[1] | |
| #print json_filename |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #file /etc/sysconfig/slapd | |
| # OpenLDAP server configuration | |
| # see 'man slapd' for additional information | |
| # Where the server will run (-h option) | |
| # - ldapi:/// is required for on-the-fly configuration using client tools | |
| # (use SASL with EXTERNAL mechanism for authentication) | |
| # - default: ldapi:/// ldap:/// | |
| # - example: ldapi:/// ldap://127.0.0.1/ ldap://10.0.0.1:1389/ ldaps:/// | |
| SLAPD_URLS="ldap:/// ldaps:///" |
NewerOlder