-
-
Save HackingGate/b75ac856397075756ea878380c5b848c to your computer and use it in GitHub Desktop.
| VERSION=19.07.7 | |
| # Download imagebuilder for R7800. | |
| aria2c -c -x4 -s4 https://downloads.openwrt.org/releases/${VERSION}/targets/ipq806x/generic/openwrt-imagebuilder-${VERSION}-ipq806x-generic.Linux-x86_64.tar.xz | |
| # Extract & remove used file & cd to the directory | |
| tar -xvf openwrt-imagebuilder-${VERSION}-ipq806x-generic.Linux-x86_64.tar.xz | |
| rm openwrt-imagebuilder-${VERSION}-ipq806x-generic.Linux-x86_64.tar.xz | |
| cd openwrt-imagebuilder-${VERSION}-ipq806x-generic.Linux-x86_64/ | |
| # Use https when making image | |
| sed -i 's/http:/https:/g' repositories.conf | |
| # Make all kernel modules built-in | |
| sed -i -e "s/=m/=y/g" build_dir/target-arm_cortex-a15+neon-vfpv4_musl_eabi/linux-ipq806x_generic/linux-*/.config | |
| # Run the final build configuration | |
| make image PROFILE=netgear_r7800 \ | |
| PACKAGES="ca-bundle ca-certificates libustream-openssl -ppp -ppp-mod-pppoe \ | |
| uhttpd uhttpd-mod-ubus libiwinfo-lua luci-base luci-app-firewall luci-mod-admin-full luci-theme-bootstrap \ | |
| -wpad-mini -wpad-basic wpad-openssl usbutils block-mount e2fsprogs samba4-server luci-app-samba4 \ | |
| aria2 luci-app-aria2 ariang stubby curl wget tcpdump kmod-fs-ext4 kmod-usb-storage kmod-usb-storage-uas" | |
| # list result | |
| ls $PWD/bin/targets/ipq806x/generic |
| # To use opkg via https | |
| opkg update | |
| opkg install ca-bundle ca-certificates libustream-openssl curl wget | |
| sed -i 's/http:/https:/g' /etc/opkg/distfeeds.conf | |
| # DoH with Dnsmasq and https-dns-proxy | |
| # https://openwrt.org/docs/guide-user/services/dns/doh_dnsmasq_https-dns-proxy | |
| opkg install https-dns-proxy luci-app-https-dns-proxy | |
| # pkg-upgrade.sh | |
| wget https://gist.github.com/HackingGate/b75ac856397075756ea878380c5b848c/raw/db404b6028b9136b47192ce90f3520e97a3faa3e/pkg-upgrade.sh | |
| chmod +x pkg-upgrade.sh | |
| ./pkg-upgrade.sh | |
| # sys-upgrade.sh | |
| wget https://gist.github.com/HackingGate/b75ac856397075756ea878380c5b848c/raw/725c991f7286400e4f0d6ae5f993f8dd17caca90/sys-upgrade.sh | |
| chmod +x sys-upgrade.sh | |
| ./sys-upgrade.sh | |
| # Capturing packets | |
| opkg install tcpdump | |
| # Deploy WPA3 Wi-Fi | |
| opkg remove wpad-mini wpad-basic | |
| opkg install wpad-openssl | |
| /etc/init.d/network restart | |
| # Using storage devices | |
| opkg update | |
| opkg install kmod-usb-storage | |
| opkg install kmod-usb-storage-uas | |
| opkg install usbutils | |
| lsusb -t | |
| opkg install block-mount | |
| block info | grep "/dev/sd" | |
| lsusb -t | |
| opkg install e2fsprogs | |
| opkg install kmod-fs-ext4 | |
| block detect | uci import fstab | |
| uci set fstab.@mount[-1].enabled='1' | |
| uci set fstab.@global[0].check_fs='1' | |
| uci commit fstab | |
| uci show fstab | |
| service fstab boot | |
| # SMB Samba4 | |
| opkg install samba4-server | |
| opkg install luci-app-samba4 | |
| # Aira2 and ariang | |
| opkg install aria2 | |
| opkg install luci-app-aria2 | |
| opkg install ariang |
| #!/bin/sh | |
| set -e | |
| # Force HTTPS | |
| sed -i 's/http:/https:/g' /etc/opkg/distfeeds.conf | |
| # Update packages | |
| opkg update | |
| for ipk in $(opkg list-upgradable | awk '$1!~/^base-files|^kmod|^Multiple/{print $1}'); do | |
| opkg upgrade $ipk | |
| done | |
| # Download bt trackers | |
| TRACKERS=`curl -s https://raw.githubusercontent.com/ngosang/trackerslist/master/trackers_best.txt \ | |
| | tr '\n' ' ' \ | |
| | sed 's/ *$//'` | |
| echo "Updating /etc/config/aria2 bt_tracker" | |
| # Delete config | |
| sed -i "/list bt_tracker/d" /etc/config/aria2 | |
| # Append config | |
| echo -e "\tlist bt_tracker '$TRACKERS'" | tee -a /etc/config/aria2 | |
| # Download netboot.xyz | |
| wget https://boot.netboot.xyz/ipxe/netboot.xyz.efi -O /root/tftp/netboot.xyz.efi |
| #!/bin/sh | |
| set -e | |
| OPENWRT_TAG=`git ls-remote git://github.com/openwrt/openwrt.git | grep -E -o 'v[0-9]+\.[0-9]+\.[0-9]+' | tail -1` | |
| OPENWRT_VERSION=`echo ${OPENWRT_TAG} | grep -E -o '[0-9]+\.[0-9]+\.[0-9]+'` | |
| rm -f *.manifest manifest.diff | |
| # Use sed remove vlmcsd | |
| opkg list-installed | sed '/vlmcsd/d' | tee list-installed.manifest | |
| wget https://downloads.hackinggate.com/openwrt-${OPENWRT_VERSION}-ipq806x-generic-netgear-r7800/openwrt-${OPENWRT_VERSION}-ipq806x-generic-device-netgear-r7800.manifest | |
| diff openwrt-${OPENWRT_VERSION}-ipq806x-generic-device-netgear-r7800.manifest list-installed.manifest | tee manifest.diff | |
| FILE1_LINES=`cat manifest.diff | grep '<' | wc -l` | |
| FILE2_LINES=`cat manifest.diff | grep '>' | wc -l` | |
| # n1 -ge n2 True if the integer n1 is algebraically greater than or equal to the integer n2. | |
| # n1 -gt n2 True if the integer n1 is algebraically greater than the integer n2. | |
| if [ ${FILE1_LINES} -ge 0 ] && [ ${FILE1_LINES} -eq ${FILE2_LINES} ] | |
| then | |
| echo "Upgrading to ${OPENWRT_TAG}" | |
| rm -f openwrt-${OPENWRT_TAG}-ipq806x-generic-netgear_r7800-squashfs-sysupgrade.bin | |
| wget https://downloads.hackinggate.com/openwrt-${OPENWRT_VERSION}-ipq806x-generic-netgear-r7800/openwrt-${OPENWRT_VERSION}-ipq806x-generic-netgear_r7800-squashfs-sysupgrade.bin | |
| # -o attempt to preserve all changed files in /, except those | |
| # from packages but including changed confs. | |
| sysupgrade -o openwrt-${OPENWRT_VERSION}-ipq806x-generic-netgear_r7800-squashfs-sysupgrade.bin | |
| fi |
Install and verify USB drivers
opkg update
opkg install kmod-usb-storage
opkg install kmod-usb-storage-uas
opkg install usbutils
lsusb -tVerify the disk
opkg install block-mount
block info | grep "/dev/sd"Install ext4 file system drivers
opkg install e2fsprogs
opkg install kmod-fs-ext4Automount the partition
block detect | uci import fstab
uci set fstab.@mount[-1].enabled='1'
uci set fstab.@global[0].check_fs='1'
uci commit fstab
uci show fstabservice fstab bootSMB Samba4
opkg install samba4-server
opkg install luci-app-samba4Aira2 and ariang
opkg install aria2
opkg install luci-app-aria2
opkg install ariangCloudflare DDNS
opkg install ddns-scripts
opkg install ddns-scripts-cloudflare
opkg install luci-app-ddnsDNS requests via TCP not supported
BusyBox's nslookup and hostip do not support to specify to use TCP instead of default UDP when requesting DNS server!
- You should install 'bind-host' or 'knot-host' or 'drill' package for DNS requests.
- You should install 'bind-host' or 'knot-host' or 'drill' package for DNS requests.
opkg install bind-hostEnable WPA2-Enterprise
As of Oct 20, 2019. OpenWrt does not support WPA3-EAP.
You will use WAP2-EAP instead.
You will need iOS 13 or later. As far as I know iOS 12.4 will only work with WPA-EAP NOT WPA2-EAP.
Install freeradius3 on OpenWrt if you don't have a RADIUS server
opkg update
eval $(opkg find freeradius3* | sed 's/ - .*//' | sed 's/^/opkg install /')
Rest of the tutorial here:
https://openwrt.org/docs/guide-user/network/wifi/freeradius
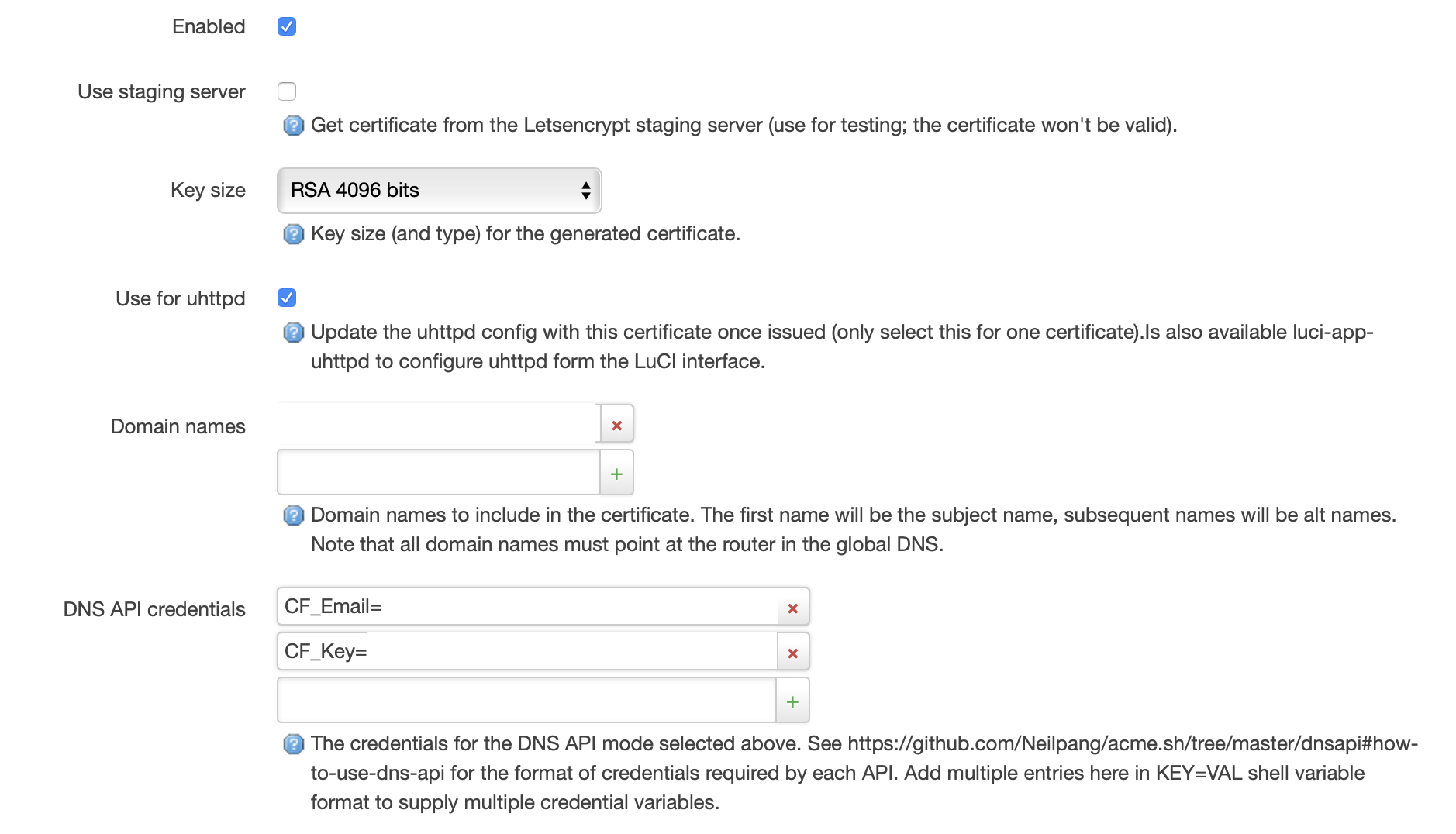
opkg install acme
opkg install luci-app-acme
opkg install socat
Update acme.sh to the latest
https://forum.openwrt.org/t/solved-luci-app-acme-lets-encrypt-and-connection-reset-by-peer/9657/2
Recently I ran out of 80MB flash storage of my R7800.
So I tried ImageBuilder
Here's what I have done
Preparation
Download imagebuilder-19.07.3 for R7800.
aria2c -c -x4 -s4 https://downloads.openwrt.org/releases/19.07.3/targets/ipq806x/generic/openwrt-imagebuilder-19.07.3-ipq806x-generic.Linux-x86_64.tar.xzExtract & remove used file & cd to the directory
tar -xvf openwrt-imagebuilder-19.07.3-ipq806x-generic.Linux-x86_64.tar.xz
rm openwrt-imagebuilder-19.07.3-ipq806x-generic.Linux-x86_64.tar.xz
cd openwrt-imagebuilder-19.07.3-ipq806x-generic.Linux-x86_64/The command will make your own R7800 image (RUN THE FINAL BUILD COMMAND)
make image PROFILE=netgear_r7800Configuration
Use https when making image
sed -i 's/http:/https:/g' repositories.confYou will need some additional packages to make opkg over https work
make image PROFILE=netgear_r7800 \
PACKAGES="ca-bundle ca-certificates libustream-openssl"I will do some recommendations from Saving firmware space to reduce firmware size
Excluding packages
I live in Japan and my ISP came with IPv6-plus I don't need PPPoE.
make image PROFILE=netgear_r7800 \
PACKAGES="ca-bundle ca-certificates libustream-openssl -ppp -ppp-mod-pppoe"Sometimes using LuCI is easier to maintenance your router so I'm definitely going to have it
make image PROFILE=netgear_r7800 \
PACKAGES="ca-bundle ca-certificates libustream-openssl -ppp -ppp-mod-pppoe \
uhttpd uhttpd-mod-ubus libiwinfo-lua luci-base luci-app-firewall luci-mod-admin-full luci-theme-bootstrap"Making all kernel modules built-in
Oh I use a lot of kernel modules. Instead of turning them on one by one. Why not just enable all?
sed -i -e "s/=m/=y/g" build_dir/target-arm_cortex-a15+neon-vfpv4_musl_eabi/linux-ipq806x_generic/linux-4.14.180/.configModifying build configuration variables
I'm not quite sure about that... Just pass.
Replace LuCI icons with a blank pixel
Looks like I have to clone the sources so that I can replace the images. That will make a lot of time to compile... Just pass.
Adding more packages
Since we enabled all kernel modules so when don't need to install kmod anymore.
make image PROFILE=netgear_r7800 \
PACKAGES="ca-bundle ca-certificates libustream-openssl -ppp -ppp-mod-pppoe \
uhttpd uhttpd-mod-ubus libiwinfo-lua luci-base luci-app-firewall luci-mod-admin-full luci-theme-bootstrap \
-wpad-mini -wpad-basic wpad-openssl usbutils block-mount e2fsprogs samba4-server luci-app-samba4 \
aria2 luci-app-aria2 ariang stubby curl wget tcpdump kmod-fs-ext4 kmod-usb-storage kmod-usb-storage-uas"Build
Run the final build configuration
make image PROFILE=netgear_r7800 \
PACKAGES="ca-bundle ca-certificates libustream-openssl -ppp -ppp-mod-pppoe \
uhttpd uhttpd-mod-ubus libiwinfo-lua luci-base luci-app-firewall luci-mod-admin-full luci-theme-bootstrap \
-wpad-mini -wpad-basic wpad-openssl usbutils block-mount e2fsprogs samba4-server luci-app-samba4 \
aria2 luci-app-aria2 ariang stubby curl wget tcpdump kmod-fs-ext4 kmod-usb-storage kmod-usb-storage-uas"Your own image is located in $PWD/bin/targets/ipq806x/generic
Auto KMS
Install luci-compat
opkg update
opkg install luci-compatInstall the packages
Go to luci, activate it.
On your computer that connected your OpenWrt router. Run the command to check if it work.
nslookup -type=srv _vlmcs._tcp.lanServer: pi.hole
Address: 192.168.4.45
_vlmcs._tcp.lan SRV service location:
priority = 0
weight = 100
port = 1688
svr hostname = HG-X4S.lan
HG-X4S.lan AAAA IPv6 address = fd7b:1af4:a297::1
HG-X4S.lan internet address = 192.168.4.1
Key Management Services (KMS) client activation and product keys
https://learn.microsoft.com/en-us/windows-server/get-started/kms-client-activation-keys
Statistics
https://openwrt.org/docs/guide-user/luci/luci_app_statistics
opkg install luci-app-statistics
opkg list | grep collectd-mod
opkg install collectd-mod-cpu collectd-mod-interface collectd-mod-memory collectd-mod-ping collectd-mod-rrdtool collectd-mod-wireless
/etc/init.d/luci_statistics enable
/etc/init.d/collectd enableEdit /etc/config/luci_statistics
Change /tmp/rrd to /mnt/sda1/rrd
cd /mnt/sda1
mkdir rrd
chown -R nobody:nogroup rrd
My Samba Storage
- Everyone can access and edit files in Unlimited disk.
- Users have a Private and a Public folder in Shared disk.
Result:
When I logged in as hg, I can't access smb_test_user's Private folder. And I can't edit or delete files from its Public folder.

Add user
echo -n 'hg:*:1000:65534:hg:/var:/bin/false' >> /etc/passwd65534 is the nogroup id where you can see in /etc/group.
The Configuration
Folder structure and permissions:
# ll /mnt/sda1 | awk '{print $1, $3, $4, $9}'
drwxr-xr-x root root ./
drwxr-xr-x root root ../
drwxr-xr-x root root Shared/
drwxr-xr-x root root Unlimited/
drwx------ root root lost+found/
# ll /mnt/sda1/Shared/* | awk '{print $1, $3, $4, $9}'
hg:
drwxr-xr-x root root ./
drwxr-xr-x root root ../
drwx------ hg root Private/
drwxr-xr-x hg root Public/
smb_test_user:
drwxr-xr-x root root ./
drwxr-xr-x root root ../
drwx------ smb_test root Private/
drwxr-xr-x smb_test root Public/
Configuration file:
# cat /etc/config/samba4
config samba
option workgroup 'WORKGROUP'
option charset 'UTF-8'
option description 'Samba on OpenWRT'
option macos '1'
config sambashare
option read_only 'no'
option guest_ok 'yes'
option create_mask '0666'
option dir_mask '0777'
option force_root '1'
option name 'Unlimited'
option path '/mnt/sda1/Unlimited'
option inherit_owner 'yes'
config sambashare
option read_only 'no'
option create_mask '0666'
option dir_mask '0777'
option name 'Shared'
option path '/mnt/sda1/Shared'
option users 'smb_test_user,hg'
option guest_ok 'no'
option inherit_owner 'yes'
Add a user in samba
smbpasswd -a hg
Reference
[OpenWrt Wiki] SMB / Samba share overview (Windows file sharing)
Using Time Machine feature in samba4 is unstable. So I changed to AFP.
AFP Netatalk share configuration (aka Apple Time Machine)
Running both AFP and SAMBA on the same router is no problem.
Your macOS only show AFP disk. If you want access SAMBA you may need enter the address smb:// in your browser manually.
You can use both over VPN.
Don't use HOSTNAME.local you can't find the address over VPN.
You may need enter address smb://HOSTNAME.lan or afp://HOSTNAME.lan.
# grep users /etc/group
users:x:100:hgKeep configurations while sysupgrade
# DNS
/etc/dnsmasq.conf
# AFP
/etc/afp.conf
/etc/avahi/
/etc/extmap.conf
/var/netatalk/
# Samba
/etc/samba/secrets.tdb
/etc/samba/smbpasswd
Multi WAN
Setup VLAN
Add a new VLAN 3. Assign LAN 1 port to VLAN 3. (On R7800 the port no. is 4)
If you don't what no. is on your router, go to this page:
[OpenWrt Router]/cgi-bin/luci/admin/network/switch
After adding a new VLAN. /etc/config/network will look like this:
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 6t'
option vid '1'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '2'
option ports '0t 5'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '3'
option ports '0t 4'
Setup load balancing
Install mwan3
opkg install mwan3 luci-app-mwan3
Edit /etc/config/network
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config interface 'wanb'
option ifname 'eth0.3'
option proto 'dhcp'
config interface 'wanb6'
option ifname 'eth0.3'
option proto 'dhcpv6'
If you don't know what 'eth0.2' or 'eth0.3' is and don't know what the number means or your router is different from me. Read OpenWrt Switch Documentation.
The final thing is enable MWAN interfaces.
Use LuCI or edit /etc/config/mwan3.
MWAN3 with domain support
Setup
opkg info mwan3
When you install mwan3, ipset is also installed.
/etc/dnsmasq.conf example:
ipset=/youtube.com/youtube
Follow this article.
OpenWRT conditional hostname routing using MWAN3 and ipset
opkg remove dnsmasq
opkg install dnsmasq-full
Download the script https://gist.github.com/tmkasun/4f9e1fe6ed8254a115d2924f6b3b885d
cd /etc/init.d/
wget https://gist.github.com/tmkasun/4f9e1fe6ed8254a115d2924f6b3b885d/raw/e99d155d627d2056e1aeb143328896f734e14e05/autoipset
Edit
vim autoipset
Enable
chmod +x autoipset
/etc/init.d/autoipset enable
/etc/init.d/autoipset start
/etc/init.d/dnsmasq restart
/etc/init.d/mwan3 restart
My configuration
- Cygames returns 503 to my IPv4 address and Cygames is not available in IPv6
- Engadget JP says my IPv6 (JP node / US address) from HE.net is in EU and don't let me access so I have to force it to use IPv4
/etc/init.d/autoipset:
- cygames (IPv4 only)
- engadget_jp (IPv6 only)
ipset -N cygames hash:ip
ipset -N engadget_jp hash:ip family inet6
/etc/dnsmasq.conf:
- cygames.jp and all subdomains
- japanese.engadget.com
# Unblock Cygames
ipset=/cygames.jp/cygames
# Unblock Engadget JP
ipset=/japanese.engadget.com/engadget_jp
/etc/config/mwan3:
config rule 'cygames'
option proto 'all'
option sticky '1'
option timeout '60'
option ipset 'cygames'
option use_policy 'wanb_wan'
config rule 'engadget_jp'
option proto 'all'
option sticky '1'
option timeout '60'
option ipset 'engadget_jp'
option use_policy 'wan_wanb'
Ad blocking
https://openwrt.org/docs/guide-user/services/ad-blocking
opkg install adblock luci-app-adblock
reboot
IPv6 tunnel
Object
- Obtain IPv6 for IPv4 only network
Requirement
- IPv4
Background
I'm using a free PPPoE access point on NTT East FLET'S HIKARI provided by SoftEther.
I don't have a useable IPv6 connection.
I don't have a public IPv4 address. My internal IPv4 address and DNS is in 100.64.0.0/10.
Looks like I'm connecting with CGN (Carrier Grade NAT).
Setup
Get a free IPv6 tunnel on HE.net by clicking Create Regular Tunnel.
If you already have one. It will show on the homepage: tunnelbroker.net.
opkg install 6in4
config interface 'henet'
option proto '6in4'
option tunlink 'wan'
option peeraddr '' # Server IPv4 Address
option ip6addr '' # Copy Client IPv6 Address
option tunnelid ''
option username ''
list ip6prefix ''
option password '' # Update Key in Advanced tab
Dynamic IPv6-in-IPv4 Tunnel (HE.net only) - OpenWrt Document
Setup WireGuard server
Last modified: 2021/04/04 14:23 by vgaetera
The document is missing LuCI app, client psk, key and pub. The fixed command here:
- Preparation
# Install packages
opkg update
opkg install luci-proto-wireguard
# Configuration parameters
WG_IF="vpn"
WG_PORT="51820"
WG_ADDR="192.168.9.1/24"
WG_ADDR6="fdf1:e8a1:8d3f:9::1/64"
- Key management
# Generate keys
umask go=
wg genkey | tee wgserver.key | wg pubkey > wgserver.pub
wg genpsk > wgclient.psk
wg genkey | tee wgclient.key | wg pubkey > wgclient.pub
# Server private key
WG_KEY="$(cat wgserver.key)"
# Pre-shared key
WG_PSK="$(cat wgclient.psk)"
# Client public key
WG_PUB="$(cat wgclient.pub)"
Follow the rest of the document.
Setup WireGuard client
This will allow you access home resources from anywhere in the world.
I don't have public IPv4 address. I have public IPv6 addresses from HE.net. So my Endpoint is IPv6 only.
Replace wgclient.key, wgserver.pub, wgclient.psk, OpenWrt_LAN_Interface_Private_IPv6_Subnet, OpenWrt_Public_IPv6_Address with actual value.
DNS is optional.
[Interface]
PrivateKey = wgclient.key
Address = 192.168.9.2/32, fdf1:e8a1:8d3f:9::2/128
DNS = 192.168.9.1, fdf1:e8a1:8d3f:9::1
[Peer]
PublicKey = wgserver.pub
PresharedKey = wgclient.psk
AllowedIPs = 192.168.0.0/16, fdf1:e8a1:8d3f:9::/64, OpenWrt_LAN_Interface_Private_IPv6_Subnet
Endpoint = [OpenWrt_Public_IPv6_Address]:51820
Restart WireGuard server
/etc/init.d/network restartRoute all connections to VPN
(client side settings only)
You can change AllowedIPs to 0.0.0.0/0, ::/0. It will route all IP connection (OSI layer 3) (except some private addresses like default gateway) to WireGuard VPN.
To show routing table on macOS:
netstat -rn
192.168.1.1 is the default gateway and it goes through en0 which is the default Wi-Fi interface on macOS.
http://192.168.1.1 will be my friend's home router's authentication page.
Route 192.168.1.1 to WireGuard VPN. (utun2 is my WireGuard's interface, run ifconfig to see yours.)
sudo route change 192.168.1.1 -interface utun2
http://192.168.1.1 will be my router so I can maintenance my home network remotely.
And Internet will down.
To reset it turn off/on Wi-Fi and re-enable WireGuard.
R7800 Debricking
[OpenWrt Wiki] Netgear R7800 (Nighthawk X4S AC2600) Debricking
On macOS the tftp command is a little different.
References
# Enable TFTP server
sudo launchctl unload -w /System/Library/LaunchDaemons/tftp.plist
# Check if TFTP server running
sudo lsof -i:69
More about launchctl: https://apple.stackexchange.com/a/308421/105981
Commands
$ tftp
tftp> connect 192.168.1.1
tftp> mode binary
tftp> put openwrt-21.02.0-rc3-ipq806x-generic-netgear_r7800-squashfs-factory.img
DoH with Dnsmasq and https-dns-proxy
https://openwrt.org/docs/guide-user/services/dns/doh_dnsmasq_https-dns-proxy
opkg install https-dns-proxy luci-app-https-dns-proxyPS4 Remote Play
Common Ways To Remote Play While Away Home
-
The official PS Remote Play app away home play feature
I'm currently using v6プラス(based on MAP-E) option from my ISP. I have public IPv4/v6 addresses but I have only SOME IPv4 ports available. I failed to connect my PS4. -
The official PS Remote Play app in-home play feature with a home VPN server
This method works on OSI-layer 2 VPN but not on layer 3.
WireGuard is layer 3. And I have no plan to start a OpenVPN TAP mode (layer 2) VPN.
The solution (the third way to remote play)
Prepare a layer 3 home VPN server.
Use Chiaki instead of official PS Remote Play. (I learned here)
Seems Chiaki don't wake PS4 on LAN. So I installed ps4-waker on my home Raspberry Pi.
Just follow the link and setup it.
The result
- Set PS4 to Rest Mode before leave home. (Don't Power Off)
- SSH into home Raspberry Pi.
- Run
ps4-wakercommand will wake up PS4. - Connect to home VPN (layer 3).
- Open Chiaki any enjoy it.
Block Country IPs
Tutorial for how to boycott CN IPv4 on OpenWrt.
Script from here https://github.com/kravietz/blacklist-scripts
CIDR IP list from my project https://country-ip-blocks.hackinggate.com
OpenWrt Setup
Install
opkg install ipset curl
wget https://raw.githubusercontent.com/kravietz/blacklist-scripts/master/blacklist.sh
mv blacklist.sh /etc/firewall.user
Create /etc/ip-blacklist.conf
URLS="https://country-ip-blocks.hackinggate.com/CN_IPv4.txt"
Edit /etc/firewall.user
I don't have pppoe-wan and the blocklist don't work.
I replaced IN_OPT="-i $wan_iface" with IN_OPT="" and it works now. (kravietz/blacklist-scripts#6)
Activate
# Manual run
sh /etc/firewall.user
# Daily update
echo "01 01 * * * sh /etc/firewall.user" >>/etc/crontabs/root
Check & Test
ipset list -name
Two new sets are added
manual-blacklist
country-ip-blocks.hac
View blocked CN IPv4 entries
ipset list country-ip-blocks.hac
Here's how to use manual-blacklist.
ipset add manual-blacklist 8.8.8.8
ipset list manual-blacklist
ping 8.8.8.8
ipset del manual-blacklist 8.8.8.8
ping 8.8.8.8
Block Multi Lists
Example of /etc/ip-blacklist.conf
# Emerging Threats lists offensive IPs such as botnet command servers
URLS="https://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt"
# Blocklist.de collects reports from fail2ban probes, listing password brute-forces, scanners and other offenders
URLS="$URLS https://www.blocklist.de/downloads/export-ips_all.txt"
URLS="$URLS https://country-ip-blocks.hackinggate.com/CN_IPv4.txt"
URLS="$URLS https://country-ip-blocks.hackinggate.com/HK_IPv4.txt"
URLS="$URLS https://country-ip-blocks.hackinggate.com/MO_IPv4.txt"
All set will name country-ip-blocks.hac and override.
To fix it. Edit /etc/firewall.user. Insert script between the two lines. L116
# download the blocklist
set_name=$(echo "$url" | awk -F/ '{print substr($3,0,21);}') # set name is derived from source URL hostname
curl -L -v -s ${COMPRESS_OPT} -k "$url" >"${unsorted_blocklist}" 2>"${headers}"
Will be
# download the blocklist
set_name=$(echo "$url" | awk -F/ '{print substr($3,0,21);}') # set name is derived from source URL hostname
# autodetect country-ip-blocks.hackinggate.com
if echo "${url}" | grep -q 'country-ip-blocks.hackinggate.com'; then
set_name=$(echo "$url" | awk -F/ '{print substr($4,0,21);}')
fi
curl -L -v -s ${COMPRESS_OPT} -k "$url" >"${unsorted_blocklist}" 2>"${headers}"
sh /etc/firewall.user and ipset list -name will be
manual-blacklist
rules.emergingthreats
www.blocklist.de
CN_IPv4.txt
HK_IPv4.txt
MO_IPv4.txt
Check if there's entries
ipset list CN_IPv4.txt | wc -l
netboot.xyz
cd /root
mkdir tftp
cd tftp
wget https://boot.netboot.xyz/ipxe/netboot.xyz.efi
Edit /etc/config/dhcp
config dnsmasq
...
option enable_tftp '1'
option dhcp_boot 'netboot.xyz.efi'
option tftp_root '/root/tftp'
config dhcp 'lan'
...
list dhcp_option '66,0.0.0.0'
/etc/init.d/dnsmasq restart
Upgrade OpenWrt
auc
Advertise DNS server
/etc/config/dhcp
config dhcp 'lan'
...
list dhcp_option '6,192.168.4.45'





Deploy WPA3 Wi-Fi on OpenWrt 18.06
This will take a lot steps. Better to use 19.07 or snapshots.
https://gist.github.com/est31/d92d17acbb4ea152296f9b38764cd791
Deploy WPA3 Wi-Fi on OpenWrt 19.07 or snapshots
Uninstall
wpad-minithat came from previous stable release orwpad-basicthat came from snapshots.Install the 'full' version of wpad/hostapd.
Edit
option encryption 'psk2'or edit it on LuCI. Available WPA modes are here.Restart network