-
-
Save elreydetoda/d8ce2673e539cf1aee45ef379beb80eb to your computer and use it in GitHub Desktop.
A different PowerShell script that finds permissions assigned to OUs. This one must be run from a windows system joined to the domain to be queried.
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| function Get-OUPermissions{ | |
| <# | |
| .SYNOPSIS | |
| FindOuPermissions is a Windows PowerShell script that finds all of the different OUs in a domain, | |
| determins the permissions assigned to different users and groups, and reports back which are different | |
| from their parent; including what those permissions are. | |
| This script does require that the device be joined to the domain being queried and RSAT is installed. | |
| Author: Eric Kuehn | |
| #> | |
| Function Get-OUacl ($ACLlist){ | |
| $MyOUAclArray = New-Object System.Collections.ArrayList | |
| Foreach ($ACL in $ACLlist){ | |
| $ACLobjectType = if($ACL.ObjectType -eq '00000000-0000-0000-0000-000000000000'){ | |
| "All" | |
| }ELSE{ | |
| $RawGUID = ([guid]$ACL.ObjectType).ToByteArray() | |
| (Get-ADObject -Searchbase (Get-ADRootDSE).schemaNamingContext -Filter {schemaIDGUID -eq $RawGuid}).Name | |
| } | |
| #if the ACL is not for an object type but a property, search the config partition for a property name | |
| if($ACLobjectType -eq $null){ | |
| $ACLobjectTypeFilter = $ACL.ObjectType | |
| $ACLobjectType = (Get-ADObject -SearchBase "CN=Extended-Rights,$((Get-ADRootDSE).configurationNamingContext)" -LDAPFilter "(&(objectClass=controlAccessRight)(rightsguid=$ACLobjectTypeFilter))").Name | |
| } | |
| $ACLinheritedObjectType = if($ACL.InheritedObjectType -eq '00000000-0000-0000-0000-000000000000'){ | |
| "All" | |
| }ELSE{ | |
| $RawGUID = ([guid]$ACL.InheritedObjectType).ToByteArray() | |
| (Get-ADObject -Searchbase (Get-ADRootDSE).schemaNamingContext -Filter {schemaIDGUID -eq $RawGuid}).Name | |
| } | |
| $ACLentry = $ACL | Select IsInherited,AccessControlType, | |
| @{Name="ObjectTypeName";Expression={$ACLobjectType}}, @{Name="InheritedObjectTypeName";Expression={$ACLinheritedObjectType}}, | |
| ActiveDirectoryRights, IdentityReference, InheritanceType, InheritanceFlags, PropagationFlags | |
| [void] $MyOUAclArray.Add($ACLentry) | |
| } | |
| Return $MyOUAclArray | |
| } | |
| #Prep Output Directories | |
| if(!(Test-Path "./Output/ACLs")){ | |
| if(!(Test-Path "./Output")){New-Item -ItemType Directory -Path "./Output" | Out-Null} | |
| New-Item -ItemType Directory -Path "./Output/ACLs" | Out-Null | |
| } | |
| #Get the ACL of the Root and export it | |
| write-host "Gathering permissions set at root of Domain" | |
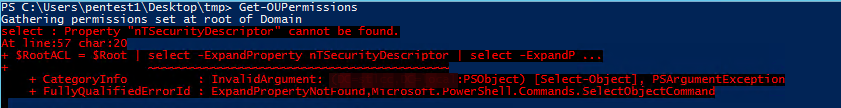
| $Root = Get-ADObject -Filter {objectClass -eq "domain"} -Properties CanonicalName, nTSecurityDescriptor | |
| $RootACL = $Root | select -ExpandProperty nTSecurityDescriptor | select -ExpandProperty Access | |
| $RootDNS = $Root.CanonicalName.split("/") | |
| $RootExpPath = "./Output/ACLs/" + $RootDNS[0] + ".csv" | |
| Get-OUacl -ACLlist $RootACL | Export-Csv $RootExpPath -NoType | |
| write-host "Finding OUs and containers" | |
| $MyOUArray = New-Object System.Collections.ArrayList | |
| #Get all the OUs in the Domain | |
| $OUs = Get-ADObject -Filter {objectcategory -eq "container" -or objectcategory -eq "builtinDomain"} -searchscope OneLevel -Properties CanonicalName, Name, nTSecurityDescriptor | |
| $OUs += Get-ADOrganizationalUnit -Filter * -Properties CanonicalName, Name, nTSecurityDescriptor | |
| $OUs = $OUs | sort canonicalname | |
| write-host $OUs.count "OUs to examine" | |
| Foreach ($OU in $OUs){ | |
| write-host "Checking security of" $OU.CanonicalName | |
| $Parent = $OU.DistinguishedName.Substring($OU.DistinguishedName.IndexOf(",")+1) | |
| $MyACL = $OU | select -ExpandProperty nTSecurityDescriptor | select -ExpandProperty Access | |
| $ParnetAcl = Get-ADObject $Parent -Properties nTSecurityDescriptor | select -ExpandProperty nTSecurityDescriptor | select -ExpandProperty Access | select IdentityReference | |
| $comp = Compare-Object $ParnetAcl $MyACL -Property IdentityReference | |
| if($comp.count -gt 0){ | |
| $Sec = "Security Changed From Parent" | |
| write-host " " $Sec | |
| $OUName = $OU.CanonicalName.replace("/","--") | |
| $ExpOUpath = "./Output/ACLs/" + $OUName + ".csv" | |
| Get-OUacl -ACLlist $MyACL | Export-Csv $ExpOUpath -NoType | |
| }ELSE{ | |
| $Sec = "" | |
| } | |
| $OUentry = $OU | select canonicalName,Name,@{Name="Security";Expression={$Sec}} | |
| [void] $MyOUArray.Add($OUentry) | |
| } | |
| $MyOUArray | ft -AutoSize | |
| $MyOUArray | Export-Csv "./Output/OUs.csv" -NoType | |
| } |
Sign up for free
to join this conversation on GitHub.
Already have an account?
Sign in to comment
figure out why this is happening